-
项目九、无线组网
目录

1 配置AC使AP放出Wifi
1.1 确保AP和AC三层互通且AP知道AC的IP
1.1.1 配置管理SVI的IP
interface Vlanif100 ip address 192.168.100.254 255.255.255.0- 1
- 2
1.1.2 该SVI配置DHCP下发IP给AP
ip pool MGMT gateway-list 192.168.100.254 network 192.168.100.0 mask 255.255.255.0 option 43 sub-option 2 ip-address 192.168.100.254 # dhcp enable # interface Vlanif100 dhcp select global- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
1.2 AC为AP下发配置
1.2.1 AC用哪个接口回复AP
capwap source interface vlan 100- 1
以下命令在 WLAN 下配置
1.2.2 AC验证AP身份(可以不认证)
- 手动验证
ap auth-mode mac-auth //ap的默认认证模式,可以改为无需认证 ap-id 1 ap-mac 00e0-fcfb-10e0- 1
- 2
- 无需验证
ap auth-mode no-auth//ap的默认认证模式,可以改为无需认证- 1
1.2.3 配置ssid 文件确定Wifi名称
ssid-profile name staff ssid staff- 1
- 2
1.2.4 配置security 文件确定wifi密码
security-profile name staff security wpa-wpa2 psk password a1234567 aes- 1
- 2
1.2.5 配置vap绑定前两个文件(转发模式和业务VLAN设置)
vap-profile name staff service-vlan vlan-id 2(设置STA的IP所属的VLAN) forward-mode direct-forward(默认) ssid-profile staff security-profile staff- 1
- 2
- 3
- 4
- 5
1.2.6 创建组且配置组关联Vap(一个组可以关联多个Vap)
- 创建组
ap-group name all- 1
- 将ap加入组中
ap-id 1 ap-group all- 1
- 2
- 关联组和VAP
ap-group name all vap-profile staff wlan 1 radio all- 1
- 2
1.3 配置网关DHCP使得连接wifi客户获取IP
ip pool vlan 2 gateway-list 192.168.2.254 network 192.168.2.0 mask 255.255.255.0 dhcp enable interface Vlanif2 dhcp select global- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
2 配置网关和防火墙起OSPF邻居
2.1 防火墙接口加入对应组
firewall zone trust add interface GigabitEthernet0/0/0 # firewall zone untrust add interface GigabitEthernet0/0/1- 1
- 2
- 3
- 4
- 5
2.2 起OSPF邻居下发默认路由
- Firewall
ospf 1 default-route-advertise always area 0.0.0.0 network 192.168.1.2 0.0.0.0- 1
- 2
- 3
- 4
- 汇聚交换机
ospf 1 area 0.0.0.0 network 192.168.1.1 0.0.0.0 network 192.168.2.0 0.0.0.255 network 192.168.3.0 0.0.0.255- 1
- 2
- 3
- 4
- 5
3 配置出口NAPT
3.1 防火墙放行所有流量(也就是透明模式)
firewall packet-filter default permit all- 1
3.2 配置easy NAT也就是NAPT
- 实验配置
nat-policy interzone trust untrust outbound policy 1 action source-nat policy source 192.168.0.0 mask 16 easy-ip GigabitEthernet0/0/1- 1
- 2
- 3
- 4
- 5
- AR6121E-S配置
acl number 2000 rule 5 permit 192.168.0.0 mask 16 # int g0/0/1 nat outbound- 1
- 2
- 3
- 4
- 5
3.3 配置默认路由指向ISP
ip route-static 0.0.0.0 0.0.0.0 100.64.0.2- 1
4 补充——AP的Web批量上线
4.0 ENSP模拟进入AC的WEB页面的方法
- 1 拉出云,鼠标左击两下进入配置
- 2 修改端口类型后点击增加

- 3 修改绑定信息为非以太网的其他接口之后,也修改端口类型为GE,然后点击增加

- 4 修改框选内容后点击增加

- 5 将云和无线AC相连

- 6 AC和云互通(默认AC的管理VLAN为SVI 1)
AC配置WEB页面的IP地址
interface Vlanif1 ip address 10.8.2.1 255.255.255.0- 1
- 2
AC配置出接口类型
interface g0/0/2 port link-type access port default vlan 1- 1
- 2
- 3
本地网卡配置相同网段(本机使用环回口)

- 7 AC配置登录信息
http secure-server enable aaa local-user admin password irreversible-cipher admin@123 local-user admin privilege level 15 local-user admin service-type http- 1
- 2
- 3
- 4
- 5
- 8 本机打开浏览器输入网址(注意前缀得输入https,默认输IP则前缀为http那无法进入)
4.1 设备批量上线
-
1 在网络已经打通的情况下(直连转发模式),先将AP的认证方式改为不认证

-
2 将以这种方式认证的AP的组从“default”移入到已有配置的“all”
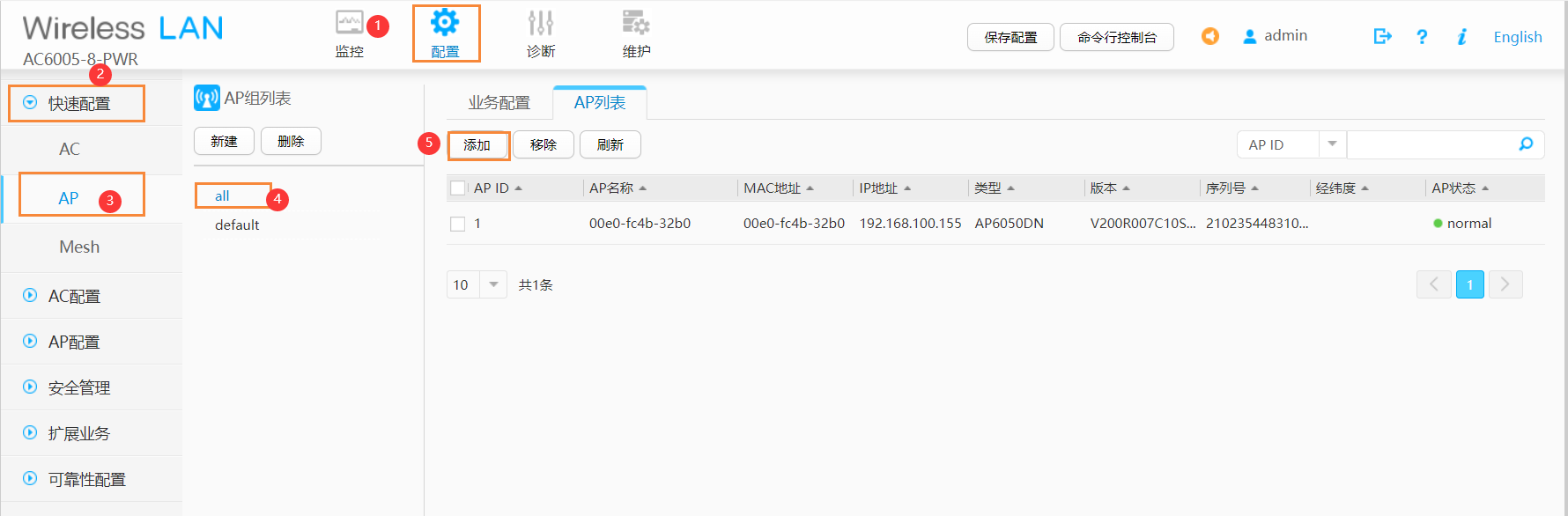


-
3 再将认证模式改为mac,防止后续非客户ap的接入
不再展示
5 补充——直连转发和隧道转发区别
注:MGMT-VLAN即管理VLAN为VLAN 100,PC的VLAN为VLAN 2
5.1 直连转发
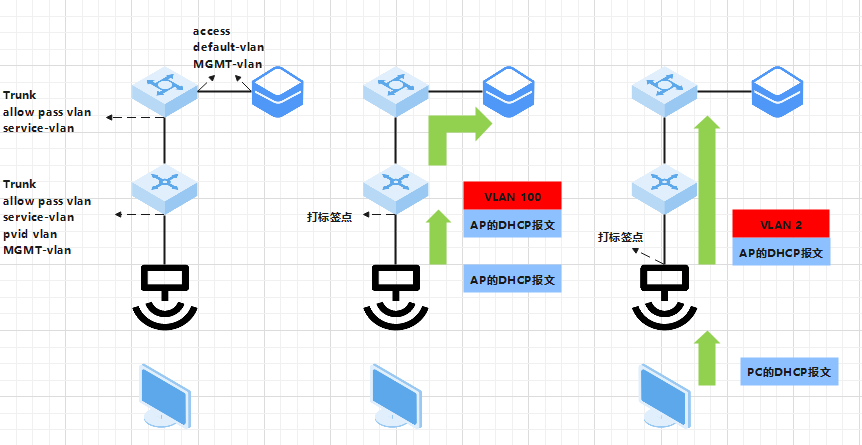
5.2 隧道转发

隧道转发的封装我们图中简化了,具体的封装如下,原理类似GRE VPN不赘述

6 补充——访客和员工的三层隔离
注:三层隔离的意思就是
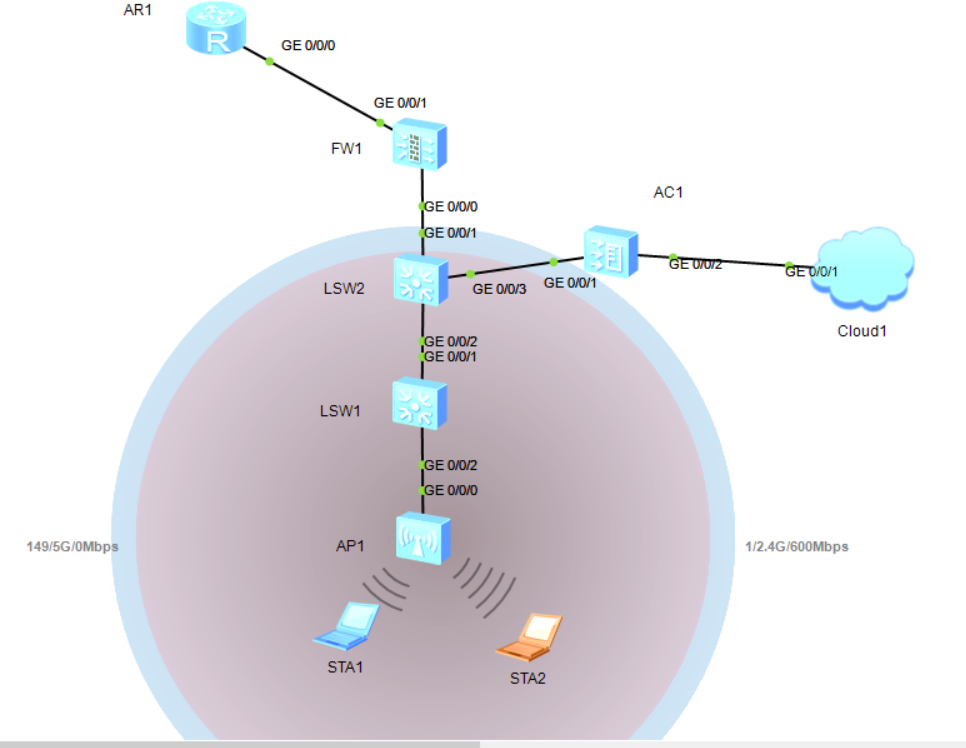
6.1 在物理口配置Traffic-filter
缺陷:需要在物理口上一个一个过滤,如果新加接口又得重新添加过滤,不灵活
# acl number 3000 rule 5 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 # # interface GigabitEthernet0/0/2 traffic-filter inbound acl 2000 #- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
6.2 在网关配置Traffic-filter
缺陷:需要匹配源目地址,当需要增加员工的地址时,需要添加新的ACL来过滤,不灵活
# acl number 3000 rule 5 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 # traffic-filter vlan 4 inbound acl 3000 #- 1
- 2
- 3
- 4
- 5
- 6
6.3 在网关配置PBR
优势:只需要匹配源IP地址,在员工的地址增加时,不需要额外的配置也能实现三层的隔离;
# acl number 2000 rule 5 permit source 192.168.2.0 0.0.0.255 # traffic classifier a operator and if-match acl 2000 # traffic behavior a redirect ip-nexthop 12.12.12.1 # traffic policy a classifier a behavior a # traffic-policy a global inbound- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
7 补充——Tel
可以通过远程登录到拥有公网IP的设备上,然后使用这个设备再远程登录到其内网的设备上;
8 AP原理
在接收到AC配置前
AP相当于是一个开启了DHCP自动获取的PC在接收到AC配置后
AP相当于一个交换机,上联口为Trunk,下联STA的接口为Access(STA连接哪个Wifi对应哪个Service VLAN,也就是Access的Default VLAN)注:STA就是连接AP发出无线型号的笔记本电脑
-
相关阅读:
38.sed高级编辑命令
SSM的整合与使用
HTTP协议3)----对于网络层的详细讲解
SpringBoot连接MySQL数据库,使用Mybatis框架(入门)
接口测试练习步骤
ESP32 之 ESP-IDF 教学(十八)—— 组件配置(KConfig)
溅射生长的铜和钨薄膜的应力调整
5分钟搭建图片压缩应用
不同的字符串之间的转换
Spring HandlerInterceptor工作机制
- 原文地址:https://blog.csdn.net/liyao1569/article/details/134068379