靶机来源: 知攻善防实验室公众号 https://mp.weixin.qq.com/s/gCWGnBiwbqSnafXU1apJCA
我是在另一台主机上通过ssh连接到靶机进行解题的,我的ip为192.168.1.104,以下为解题记录,有不对的地方希望各位大佬指正。
背景
前景需要:小王急匆匆地找到小张,小王说"李哥,我dev服务器被黑了",快救救我!!
挑战内容:
(1)黑客的IP地址
(2)遗留下的三个flag
解题
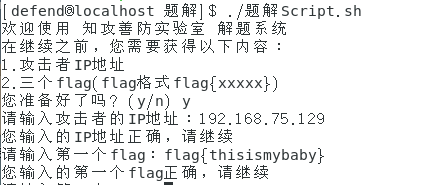
首先查看当前主机最近的用户登录情况,如何黑客成功登录,那么可以查到成功登录的记录。
[root@localhost defend]# grep "Accepted " /var/log/secure* | awk '{print $1,$2,$3,$9,$11}' Mar 18 20:23:07 root 192.168.75.129 Mar 20 14:28:21 defend 192.168.1.104
此处可以看到3月18日,root用户进行了登录,IP地址为192.168.75.129,该IP可能就是黑客的IP地址。
IP正确,接着看看有没有黑客新增的用户。
[root@localhost defend]# cat /etc/passwd root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin polkitd:x:999:998:User for polkitd:/:/sbin/nologin libstoragemgmt:x:998:996:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin colord:x:997:995:User for colord:/var/lib/colord:/sbin/nologin rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin saned:x:996:993:SANE scanner daemon user:/usr/share/sane:/sbin/nologin saslauth:x:995:76:Saslauthd user:/run/saslauthd:/sbin/nologin abrt:x:173:173::/etc/abrt:/sbin/nologin setroubleshoot:x:994:991::/var/lib/setroubleshoot:/sbin/nologin rtkit:x:172:172:RealtimeKit:/proc:/sbin/nologin pulse:x:171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin chrony:x:993:988::/var/lib/chrony:/sbin/nologin unbound:x:992:987:Unbound DNS resolver:/etc/unbound:/sbin/nologin radvd:x:75:75:radvd user:/:/sbin/nologin tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin usbmuxd:x:113:113:usbmuxd user:/:/sbin/nologin geoclue:x:991:985:User for geoclue:/var/lib/geoclue:/sbin/nologin qemu:x:107:107:qemu user:/:/sbin/nologin gluster:x:990:984:GlusterFS daemons:/run/gluster:/sbin/nologin gdm:x:42:42::/var/lib/gdm:/sbin/nologin rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin gnome-initial-setup:x:989:983::/run/gnome-initial-setup/:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin avahi:x:70:70:Avahi mDNS/DNS-SD Stack:/var/run/avahi-daemon:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin ntp:x:38:38::/etc/ntp:/sbin/nologin tcpdump:x:72:72::/:/sbin/nologin defend:x:1000:1000:defend:/home/defend:/bin/bash redis:x:988:982:Redis Database Server:/var/lib/redis:/sbin/nologin
这里好像没有看到可疑用户,接着看看有没有可疑的进程
[root@localhost defend]# ps -aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 0.3 0.1 193824 7000 ? Ss 14:25 0:03 /usr/lib/systemd/systemd --switched-root --system --deserialize 22 root 2 0.0 0.0 0 0 ? S 14:25 0:00 [kthreadd] root 4 0.0 0.0 0 0 ? S< 14:25 0:00 [kworker/0:0H] root 6 0.0 0.0 0 0 ? S 14:25 0:00 [ksoftirqd/0] root 7 0.0 0.0 0 0 ? S 14:25 0:00 [migration/0] root 8 0.0 0.0 0 0 ? S 14:25 0:00 [rcu_bh] root 9 0.0 0.0 0 0 ? S 14:25 0:00 [rcu_sched] root 10 0.0 0.0 0 0 ? S< 14:25 0:00 [lru-add-drain] root 11 0.0 0.0 0 0 ? S 14:25 0:00 [watchdog/0] root 12 0.0 0.0 0 0 ? S 14:25 0:00 [watchdog/1] root 13 0.0 0.0 0 0 ? S 14:25 0:00 [migration/1] root 14 0.3 0.0 0 0 ? S 14:25 0:03 [ksoftirqd/1] root 15 0.0 0.0 0 0 ? S 14:25 0:00 [kworker/1:0] root 16 0.0 0.0 0 0 ? S< 14:25 0:00 [kworker/1:0H] root 17 0.0 0.0 0 0 ? S 14:25 0:00 [watchdog/2] root 18 0.0 0.0 0 0 ? S 14:25 0:00 [migration/2] root 19 0.0 0.0 0 0 ? S 14:25 0:00 [ksoftirqd/2] ...... ...... ...... defend 3164 0.0 0.0 160988 2520 ? S 14:28 0:00 sshd: defend@pts/0 defend 3174 0.0 0.0 116328 2848 pts/0 Ss 14:28 0:00 -bash root 3300 0.0 0.1 231952 3928 pts/0 S 14:28 0:00 su root 3319 0.0 0.0 116324 2880 pts/0 S 14:28 0:00 bash root 3717 0.0 0.0 0 0 ? S 14:30 0:00 [kworker/2:0] root 3830 0.0 0.0 0 0 ? S 14:31 0:00 [kworker/0:0] defend 3919 0.2 0.8 697416 31464 ? Sl 14:31 0:00 /usr/libexec/gnome-terminal-server defend 3925 0.0 0.0 8536 724 ? S 14:31 0:00 gnome-pty-helper defend 3926 0.0 0.0 116444 2932 pts/1 Ss 14:31 0:00 bash defend 4011 0.0 0.0 116444 1916 pts/1 S+ 14:31 0:00 bash root 4094 0.0 0.0 0 0 ? S 14:35 0:00 [kworker/2:2] root 4104 0.0 0.0 0 0 ? S 14:36 0:00 [kworker/0:1] root 4133 0.0 0.0 108052 352 ? S 14:38 0:00 sleep 60 root 4134 0.0 0.0 157532 1900 pts/0 R+ 14:39 0:00 ps -aux
也没有看到可疑的进程,那就看看黑客登录成功之后都执行过什么命令
[root@localhost defend]# history 1 ls 2 chmod +x /etc/rc.d/rc.local 3 cat /etc/rc.d/rc.local 4 vim /etc/rc.d/rc.local 5 echo flag{thisismybaby} 6 exit 7 grep "Accepted " /var/log/secure* | awk '{print $1,$2,$3,$9,$11}' 8 cat /etc/passwd 9 netstat -anltup 10 ps -aux 11 history
这里直接发现了第一个flag:flag{thisismybaby}
除此之外,还发现黑客编辑了开机启动文件rc.local,查看一下这个文件
[root@localhost defend]# cat /etc/rc.d/rc.local #!/bin/bash # THIS FILE IS ADDED FOR COMPATIBILITY PURPOSES # # It is highly advisable to create own systemd services or udev rules # to run scripts during boot instead of using this file. # # In contrast to previous versions due to parallel execution during boot # this script will NOT be run after all other services. # # Please note that you must run 'chmod +x /etc/rc.d/rc.local' to ensure # that this script will be executed during boot. # flag{kfcvme50} touch /var/lock/subsys/local
在该文件中发现了第二个flag:flag{kfcvme50}

按照黑客的攻击思路,此时黑客已经拿到了root用户权限并且可以实现权限维持。那么第三个flag应该不会在计划任务中,而是在黑客打进来的地方。
那么黑客是怎么打进来的?
此时,想到了刚才查看passwd文件时,最后一个用户是redis用户,说明该机器上存在redis服务,于是查看网络连接,看看6379端口是否开放。
[root@localhost defend]# netstat -anltup Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1291/master tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 761/rpcbind tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN 1703/dnsmasq tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1089/sshd tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN 1092/cupsd tcp 0 0 192.168.1.105:22 192.168.1.104:59096 ESTABLISHED 3160/sshd: defend [ tcp6 0 0 ::1:25 :::* LISTEN 1291/master tcp6 0 0 :::111 :::* LISTEN 761/rpcbind tcp6 0 0 :::22 :::* LISTEN 1089/sshd tcp6 0 0 ::1:631 :::* LISTEN 1092/cupsd udp 0 0 192.168.122.1:53 0.0.0.0:* 1703/dnsmasq udp 0 0 0.0.0.0:67 0.0.0.0:* 1703/dnsmasq udp 0 0 0.0.0.0:68 0.0.0.0:* 3052/dhclient udp 0 0 0.0.0.0:111 0.0.0.0:* 761/rpcbind udp 0 0 127.0.0.1:323 0.0.0.0:* 821/chronyd udp 0 0 0.0.0.0:914 0.0.0.0:* 761/rpcbind udp 0 0 0.0.0.0:56315 0.0.0.0:* 802/avahi-daemon: r udp 0 0 0.0.0.0:5353 0.0.0.0:* 802/avahi-daemon: r udp6 0 0 :::111 :::* 761/rpcbind udp6 0 0 ::1:323 :::* 821/chronyd udp6 0 0 :::914 :::* 761/rpcbind
没有发现6379端口,那么先运行该服务。
[root@localhost defend]# redis-server 4368:C 20 Mar 14:55:04.305 # Warning: no config file specified, using the default config. In order to specify a config file use redis-server /path/to/redis.conf 4368:M 20 Mar 14:55:04.306 * Increased maximum number of open files to 10032 (it was originally set to 1024). _._ _.-``__ ''-._ _.-`` `. `_. ''-._ Redis 3.2.12 (00000000/0) 64 bit .-`` .-```. ```\/ _.,_ ''-._ ( ' , .-` | `, ) Running in standalone mode |`-._`-...-` __...-.``-._|'` _.-'| Port: 6379 | `-._ `._ / _.-' | PID: 4368 `-._ `-._ `-./ _.-' _.-' |`-._`-._ `-.__.-' _.-'_.-'| | `-._`-._ _.-'_.-' | http://redis.io `-._ `-._`-.__.-'_.-' _.-' |`-._`-._ `-.__.-' _.-'_.-'| | `-._`-._ _.-'_.-' | `-._ `-._`-.__.-'_.-' _.-' `-._ `-.__.-' _.-' `-._ _.-' `-.__.-' 4368:M 20 Mar 14:55:04.309 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128. 4368:M 20 Mar 14:55:04.309 # Server started, Redis version 3.2.12 4368:M 20 Mar 14:55:04.309 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect. 4368:M 20 Mar 14:55:04.309 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled. 4368:M 20 Mar 14:55:04.310 * DB loaded from disk: 0.001 seconds 4368:M 20 Mar 14:55:04.310 * The server is now ready to accept connections on port 6379
redis运行起来之后,需要进行登录,但是不知道密码,那就先尝试一下redis未授权。
[root@localhost defend]# redis-cli -h 127.0.0.1 127.0.0.1:6379>
直接登录成功,那么黑客应该是通过redis未授权打进来的,看看/root/.ssh下有没有被写入ssh密钥
[root@localhost .ssh]# pwd /root/.ssh [root@localhost .ssh]# ls -liah total 4.0K 51847075 drwxr-xr-x. 2 root root 29 Mar 18 20:22 . 33582977 dr-xr-x---. 7 root root 265 Mar 18 20:25 .. 51847076 -rw-r--r--. 1 root root 661 Mar 18 20:22 authorized_keys [root@localhost .ssh]# cat authorized_keys REDIS0007� redis-ver3.2.12� redis-bits�@�ctime�2�eused-mem��h ��TJB= ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAWLnUKcX0Wpd0/BDBwd6CKVb3MP9PmUwpnyIxRP3HbB7peiimjN1p6pmSHGU0NOszENTgCUGvesgwzNeG3yA/hTJOTWbHvV9Yp3ZsVPAC1JnptEWhNLbPjQjHyp/4o3H1aaFavtqrcOkFnd0/RxCYBZm8ZSEBEIV2QnN2c3ovrTYzKWDNCVJ/XM8db4i33sSpCVUJeZtBw0j3exSIpyJrxplYVDOlpY38UKuWptbAU5BdDDXPcaBLLK3TuXk2OUCBU+A6oTj9AOWgKkLfREYFavTWrifbrTrZ3nfL+YjHXS9IHoi4JKKUXoI/9yKXIIf2c7O6zoPy992nKV00wfe0TP7xEyKrrQVEitMkEAdyfyiMQ5wf9whl5xNPYrDwqO1fIzz1cUtf0UwPJ3hD6QT48PHxu9+L4heLd1J7YnwOn5l15/5CtIwkNDn035ZQq22PkhO7w02lrSBYWcT5XB2J8k/RrWwOu5u4Yi+fEPyQchXsoitcuDHMX/iPxnJOQO0= chinaran@kali �nh����[root@localhost .ssh]#
到此,推测黑客是通过redis未授权写入ssh密钥进行登录,然后通过写入开机启动文件进行权限维持。
接着来寻找第三个flag。到此,由于我比较菜就没啥思路了,于是就看看有哪些文件被修改过。
[root@localhost .ssh]# rpm -Vf /usr/bin/* file /usr/bin/alt-java is not owned by any package SM5....T. c /etc/rc.d/rc.local SM5....T. c /etc/rc.d/rc.local file /usr/bin/ControlPanel is not owned by any package SM5....T. c /etc/rc.d/rc.local SM5....T. c /etc/rc.d/rc.local file /usr/bin/itweb-settings is not owned by any package file /usr/bin/java is not owned by any package file /usr/bin/javaws is not owned by any package SM5....T. c /etc/rc.d/rc.local SM5....T. c /etc/rc.d/rc.local file /usr/bin/keytool is not owned by any package SM5....T. c /etc/rc.d/rc.local SM5....T. c /etc/rc.d/rc.local SM5....T. c /etc/rc.d/rc.local file /usr/bin/orbd is not owned by any package file /usr/bin/pack200 is not owned by any package file /usr/bin/policyeditor is not owned by any package file /usr/bin/policytool is not owned by any package missing /var/run/pulse file /usr/bin/readcd is not owned by any package S.5....T. c /etc/redis.conf S.5....T. c /etc/redis.conf S.5....T. c /etc/redis.conf S.5....T. c /etc/redis.conf S.5....T. c /etc/redis.conf S.5....T. c /etc/redis.conf file /usr/bin/rmid is not owned by any package file /usr/bin/rmiregistry is not owned by any package file /usr/bin/servertool is not owned by any package SM5....T. c /etc/rc.d/rc.local
从上面看到redis的配置文件/etc/redis.conf被修改过,打开看看
[root@localhost defend]# cat /etc/redis.conf # flag{P@ssW0rd_redis} # Redis configuration file example. # # Note that in order to read the configuration file, Redis must be # started with the file path as first argument: # # ./redis-server /path/to/redis.conf # Note on units: when memory size is needed, it is possible to specify # it in the usual form of 1k 5GB 4M and so forth: # # 1k => 1000 bytes # 1kb => 1024 bytes # 1m => 1000000 bytes # 1mb => 1024*1024 bytes # 1g => 1000000000 bytes # 1gb => 1024*1024*1024 bytes # # units are case insensitive so 1GB 1Gb 1gB are all the same.
直接在第一行看到了第三个flag:flag{P@ssW0rd_redis}

至此,就拿到了三个flag。