-
[StartingPoint][Tier1]Crocodile
Task 1
What Nmap scanning switch employs the use of default scripts during a scan?
(哪些 Nmap 扫描开关在扫描期间使用默认脚本?)
-sC
Task 2
What service version is found to be running on port 21?
发现端口 21 上运行的服务版本是什么?
$ nmap -sC 10.129.222.39 -p 21 -sV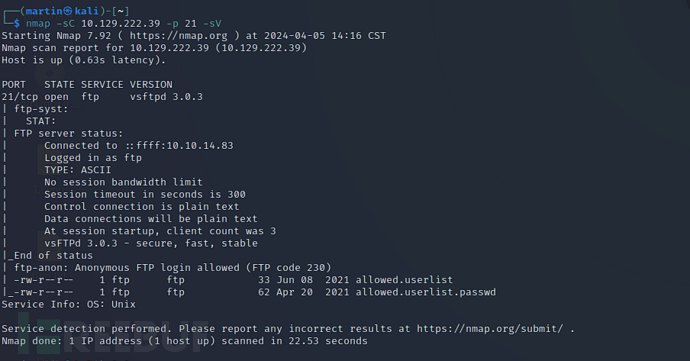
可以看到21端口FTP支持匿名访问
vsftpd 3.0.3
Task 3
What FTP code is returned to us for the “Anonymous FTP login allowed” message?
(对于“允许匿名 FTP 登录”消息,我们会返回什么 FTP 代码?)
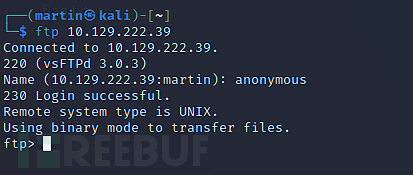
230
Task 4
After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
(使用ftp客户端连接到FTP服务器后,当提示匿名登录时,我们输入什么用户名?)
anonymous
Task 5
After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
(匿名连接到FTP服务器后,我们可以使用什么命令来下载我们在FTP服务器上找到的文件?)
get
Task 6
What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
(我们从 FTP 服务器下载的“allowed.userlist”中听起来权限较高的用户名之一是什么?)
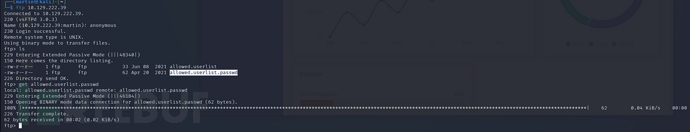
ftp>get allowed.userlist
$ cat allowed.userlist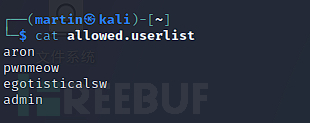
admin
Task 7
What version of Apache HTTP Server is running on the target host?
(目标主机上正在运行什么版本的 Apache HTTP Server?)
$ nmap 10.129.222.39 -p 80 -sV -Pn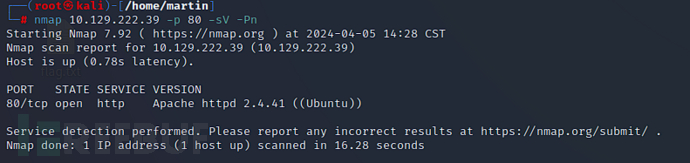
Apache httpd 2.4.41
Task 8
What switch can we use with Gobuster to specify we are looking for specific filetypes?
(我们可以在 Gobuster 中使用什么开关来指定我们正在寻找特定的文件类型?)
-x
Task 9
Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
(我们通过爆破目录后,哪个PHP文件是登陆验证页面)
-word.txt- login pass hack s-h4ck13 user manager- 1
- 2
- 3
- 4
- 5
- 6
- 7
$ gobuster dir -u "http://10.129.222.39" -x php -w ./word.txt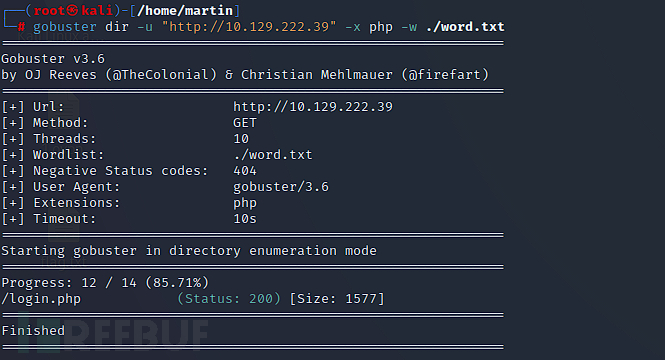
login.php
Flag
回忆一下,ftp连接后还有一个password文件,所以这里不是想让我们爆破,而是通过ftp内admin账密登录
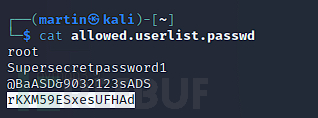
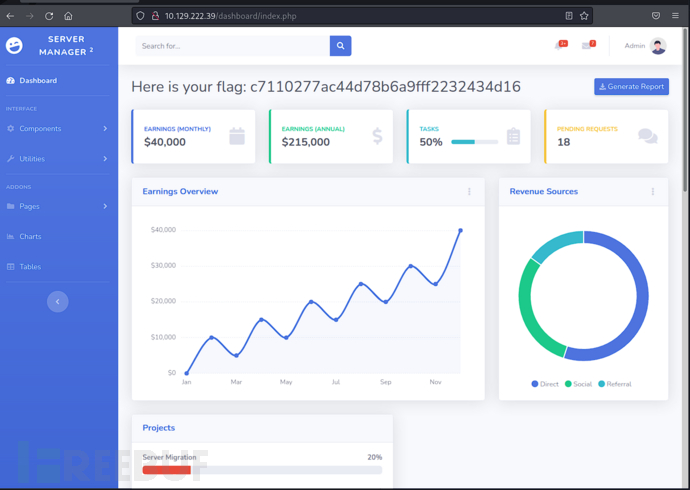
c7110277ac44d78b6a9fff2232434d16
-
相关阅读:
Cesium 空间量算——生成点位坐标
前端基础学习——带你夯实JavaScript基础
Python公共操作和推导式
推荐一款.NET开源的轻量级分布式服务框架
【重拾C语言】十三、动态数据组织(二)链表(创建、遍历检索、插入、删除、交换)
WebGL前言——WebGL相关介绍
深度学习:基于循环神经网络RNN实现自然语言生成
【技术追踪】SAM(Segment Anything Model)代码解析与结构绘制之Prompt Encoder
微医CodeReview工具链
自行更换内存条的操作规范
- 原文地址:https://blog.csdn.net/qq_51886509/article/details/137400482