-
华为防火墙基础自学系列 | Site to Site IPSec VdPdNd
视频来源:B站《乾颐堂HCIP-HCIE-security安全 2019年录制》
一边学习一边整理老师的课程内容及试验笔记,并与大家分享,侵权即删,谢谢支持!
附上汇总贴:华为防火墙基础自学系列 | 汇总_COCOgsta的博客-CSDN博客
Site to Site IPSec VPN组网
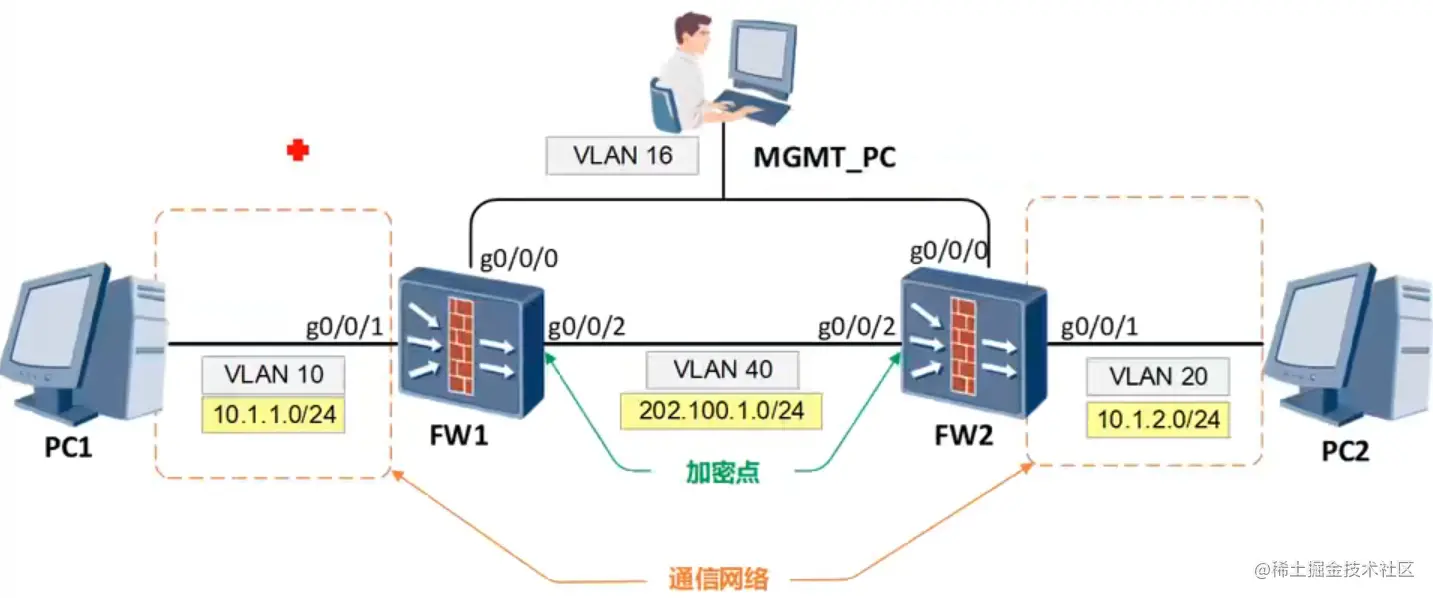
这个一个典型的站点到站点(Site to Site)IPSec VPN拓扑
IPSec VPN组网的通信网络为10.1.1.0/24和10.1.2.0/24(感兴趣流),加密点为两个防火墙的外部接口地址。
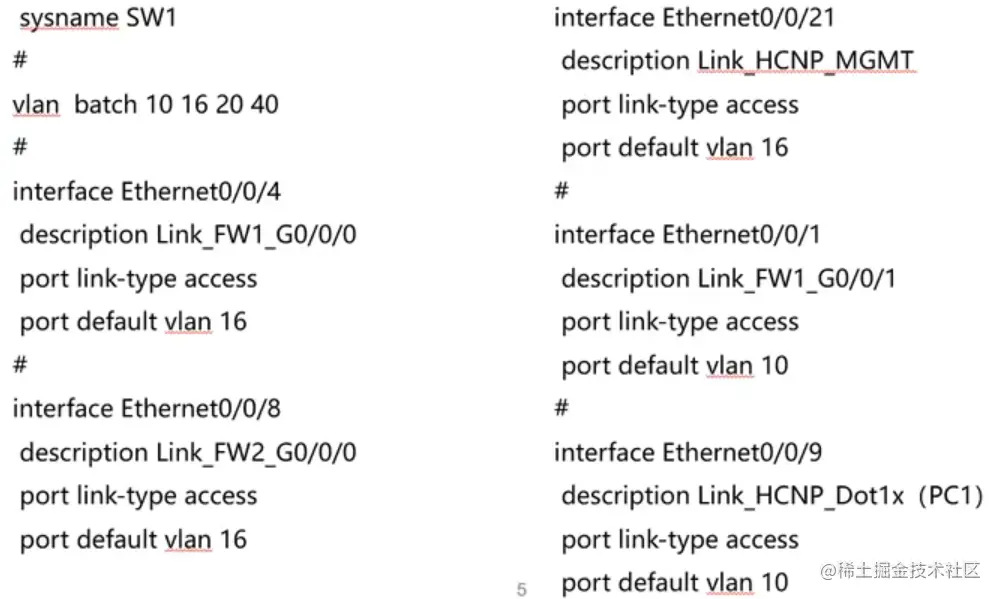
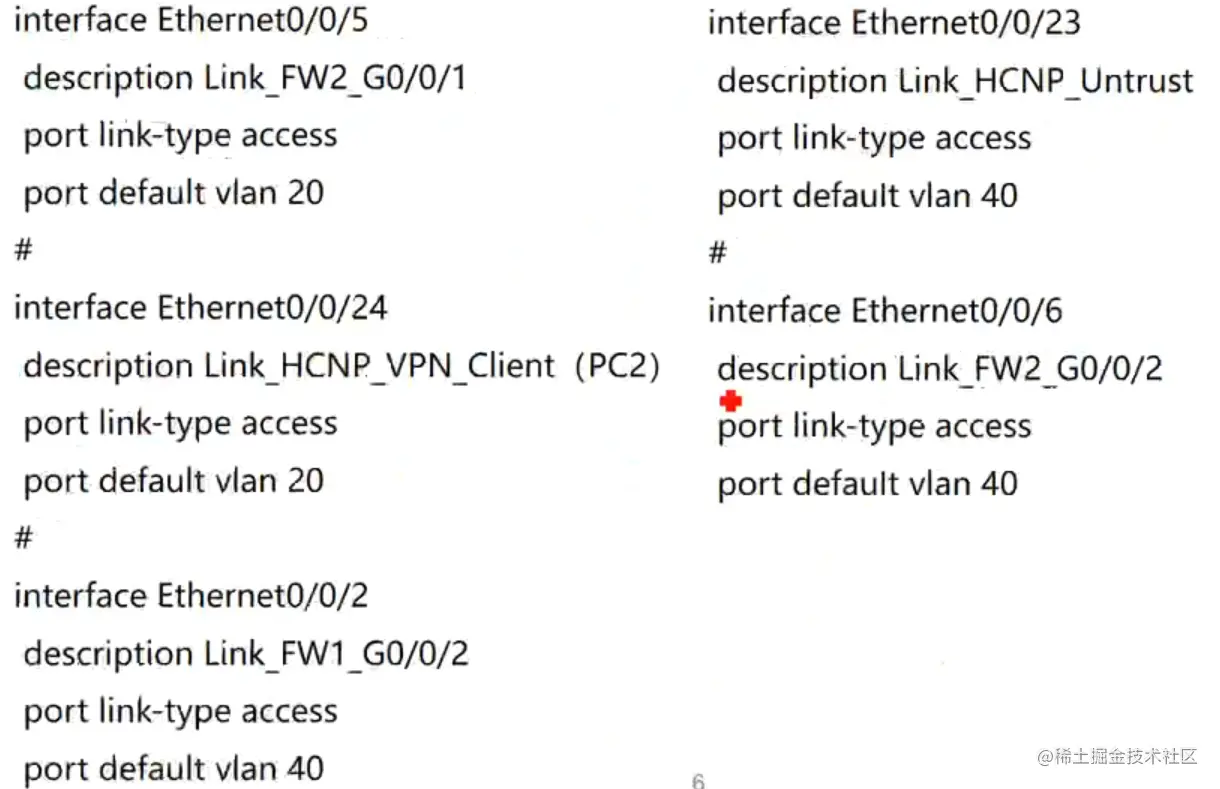
交换机底层桥接
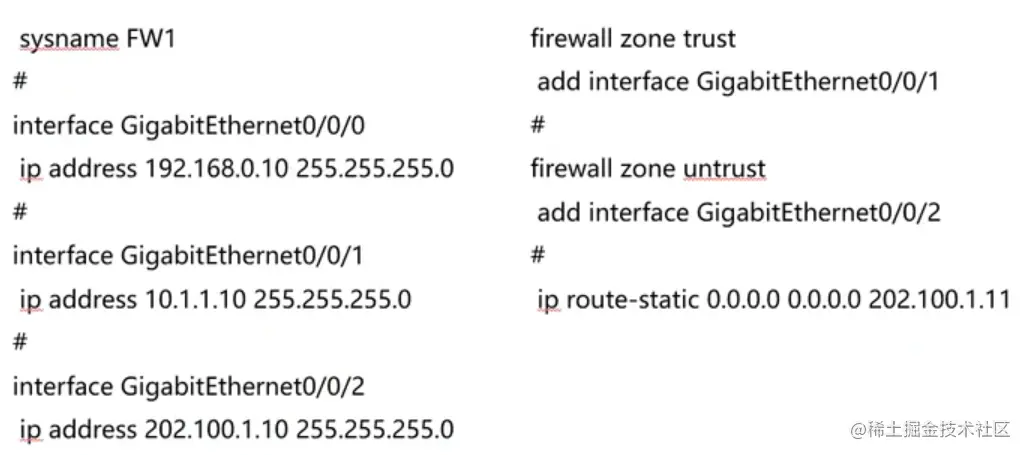
防火墙网络配置

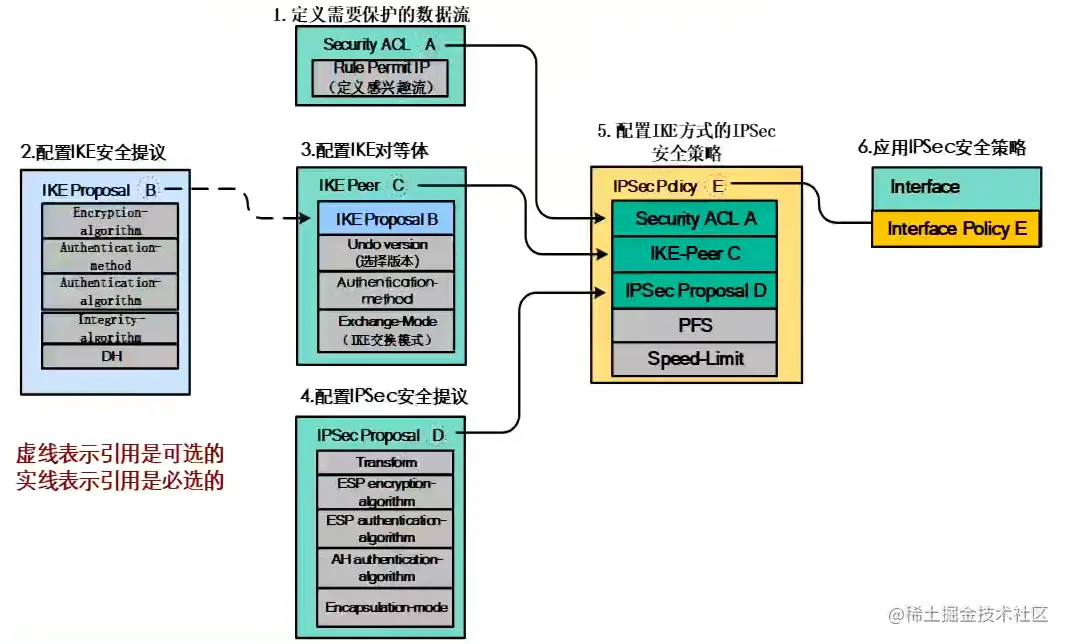
IPSec VPN安全策略配置流程图
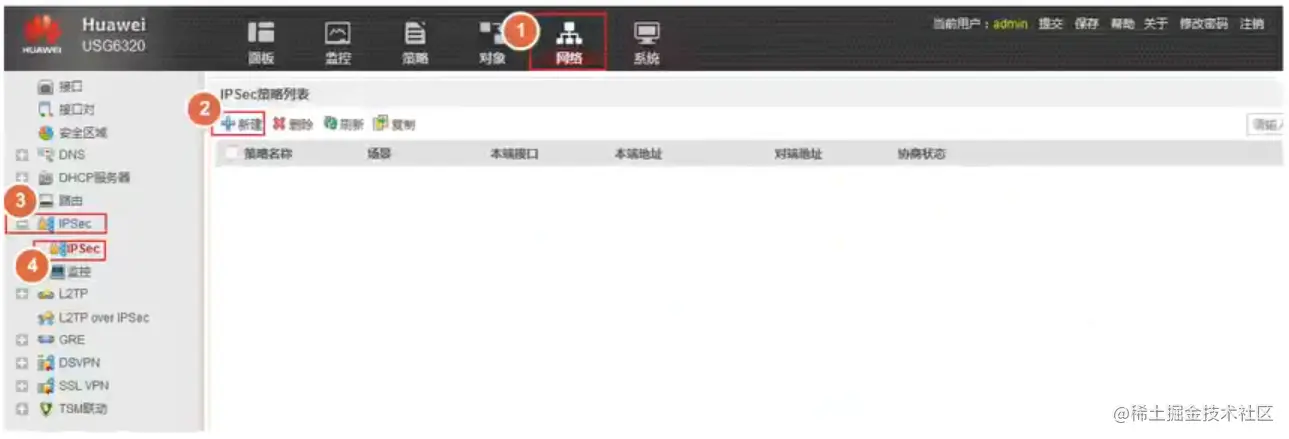
FW1配置IPsec策略-1(Web)
新建IPsec策略
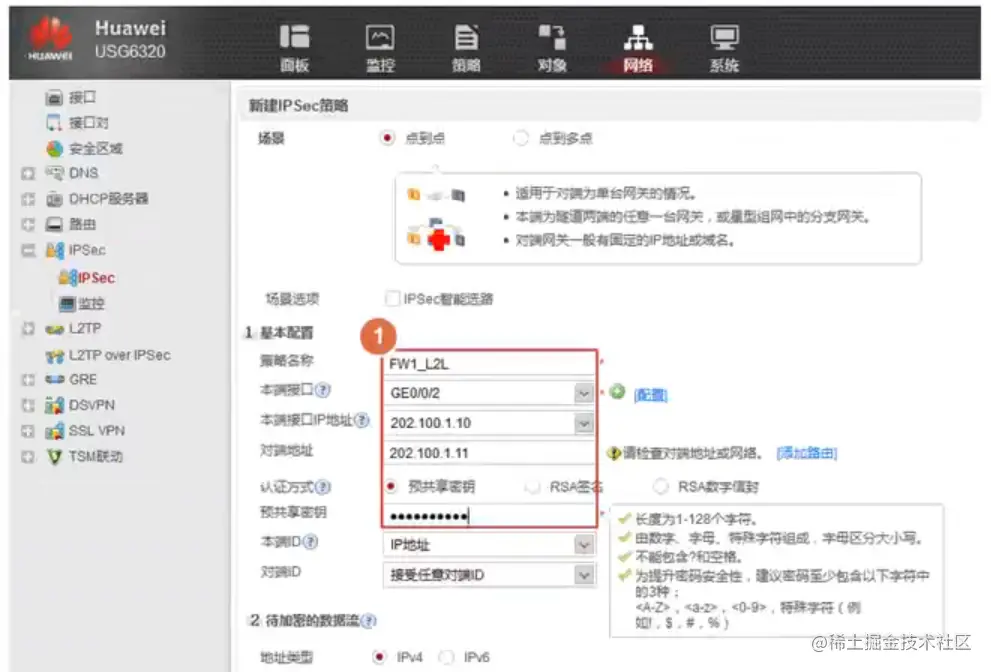
FW1配置IPsec策略-2(Web)
填写IPsec基本配置
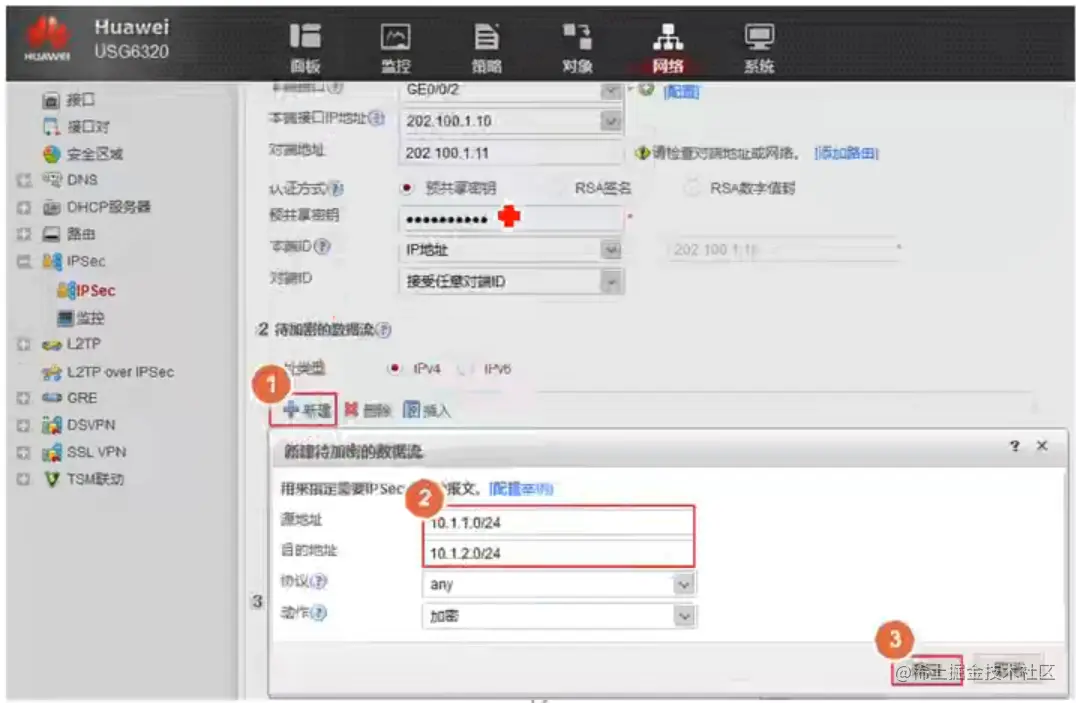
FW1配置IPsec策略-3(Web)
新建感兴趣流
FW1配置IPsec策略-4(Web)
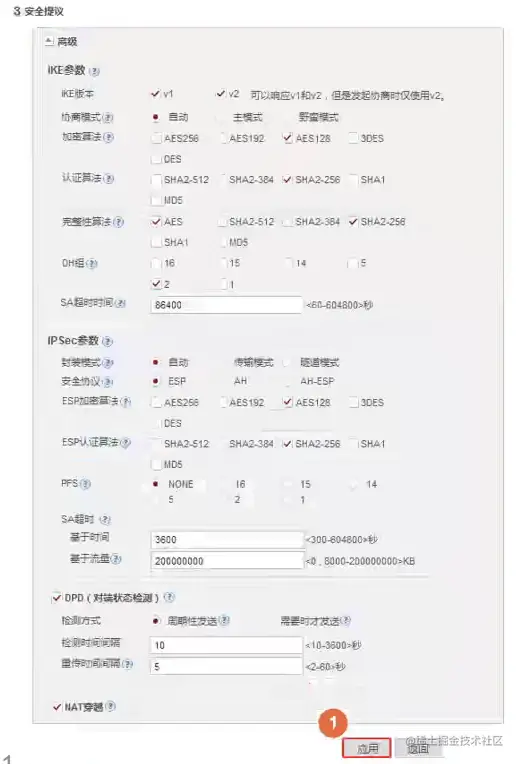
配置安全提议,保持默认即可。
FW1配置安全策略-1(Web)
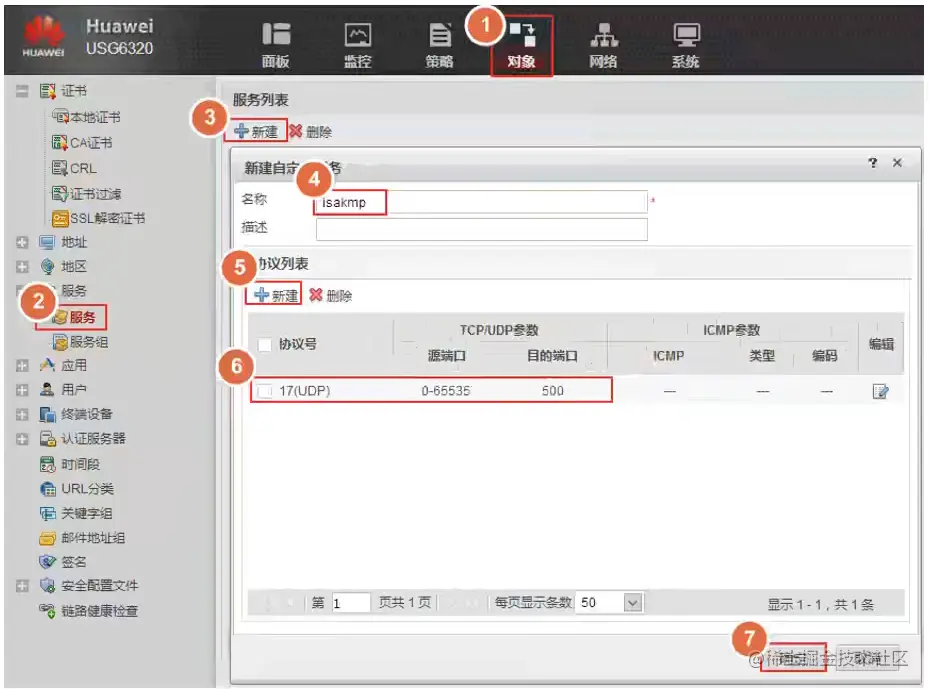
新建服务【isakmp】,UDP协议,目的端口为500。
FW1配置安全策略-2(Web)
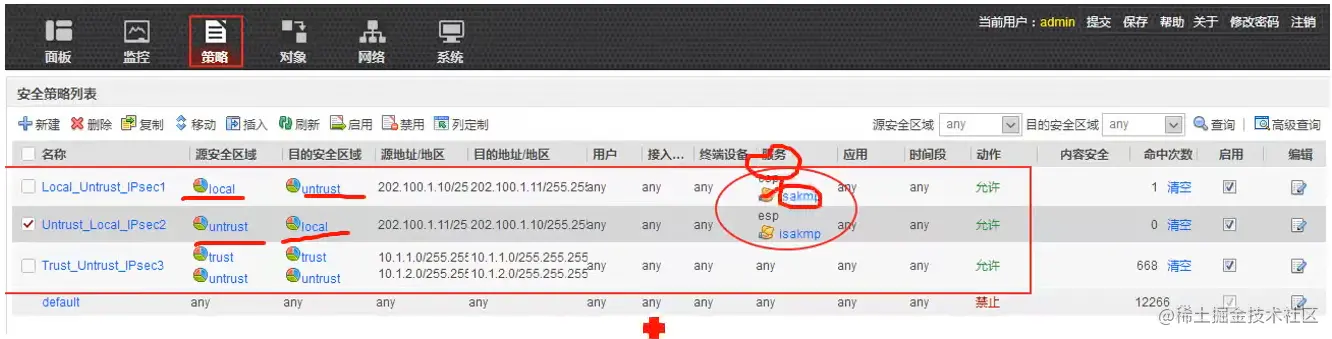
新建安全策略,放行两个防火墙的esp和isakmp流量。
放行本端感兴趣流,去往对端的流量。
FW1配置IPsec-1(CLI)
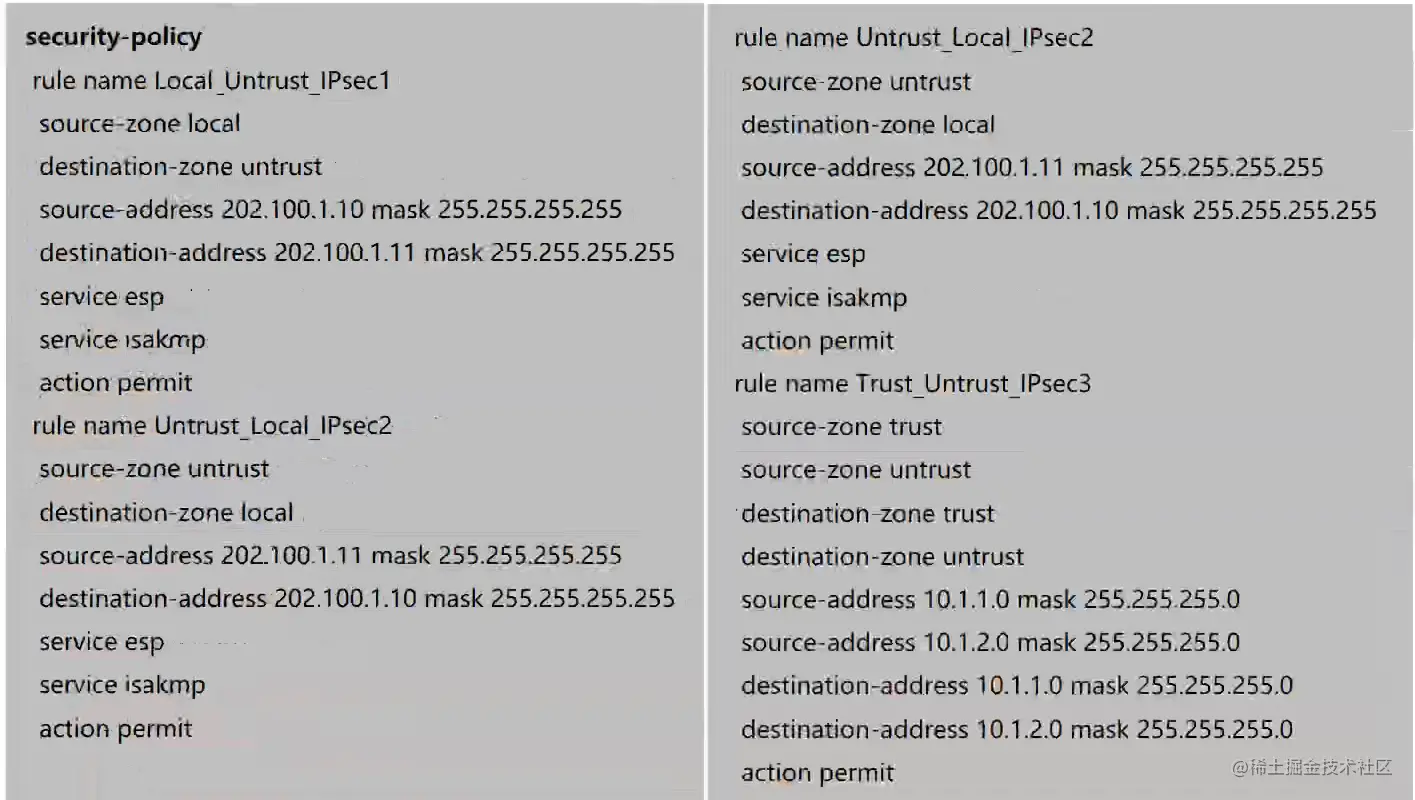
FW1配置ACL

FW1配置IKE Proposal

FW1配置IKE Peer

FW1配置IPsec-2(CLI)
FW1配置IPsec proposal

FW1配置IPsec policy

FW1调用IPsec policy

FW1配置安全策略(CLI)
FW2配置IPsec策略-1(Web)
新建IPsec策略,填写IPsec基本配置。
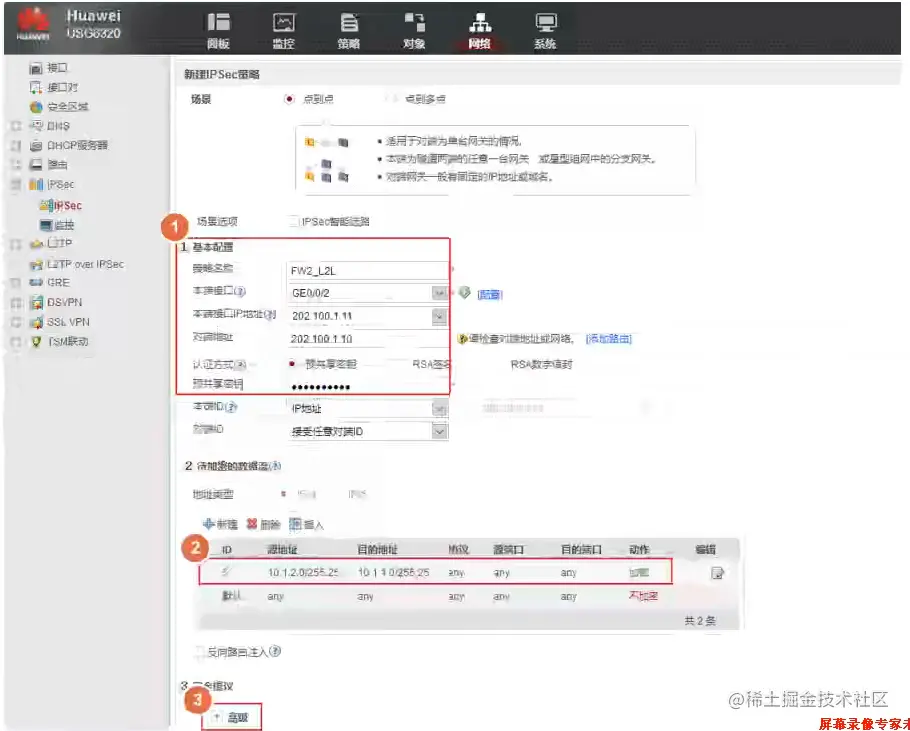
FW2配置IPsec策略-2(Web)
配置安全提议,保持默认即可。
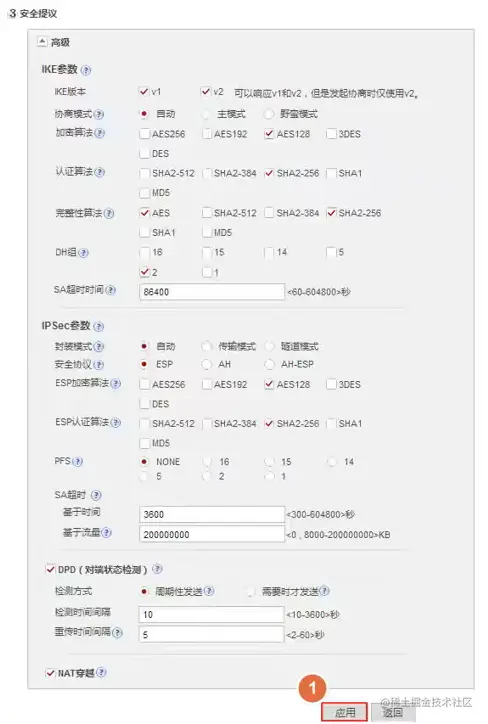
FW2配置安全策略-1(Web)
新建服务【isakmp】,UDP协议,目的端口为500。
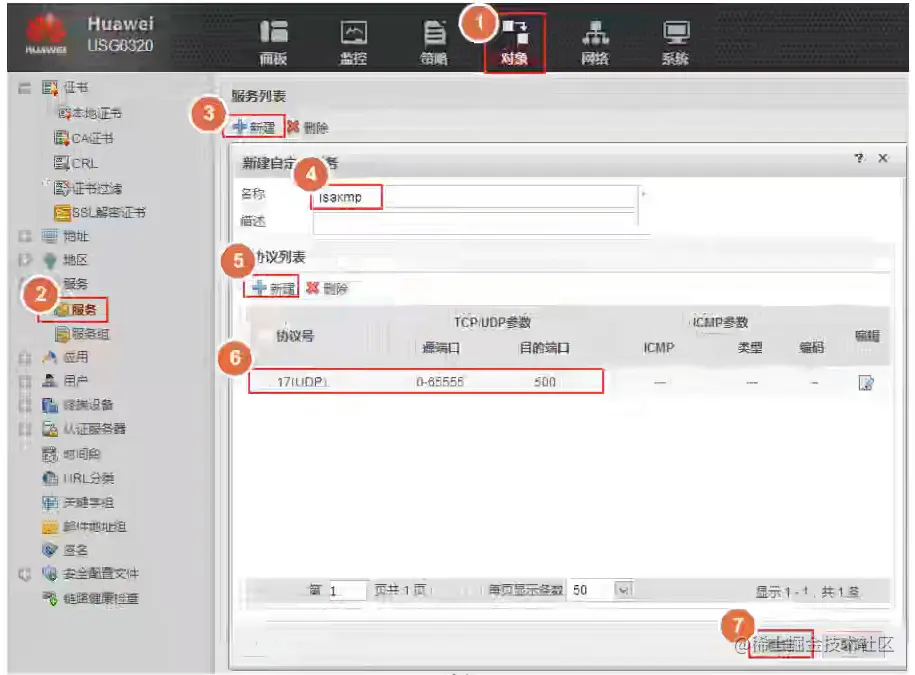
新建安全策略,放行两个防火墙的esp和isakmp流量。
放行本端感兴趣流,去往对端的流量。
FW2配置IPsec-1(CLI)
FW2配置ACL

FW2配置IKE Proposal

FW2配置IKE Peer

FW2配置IPsec-2(CLI)
FW2配置IPsec proposal

FW1配置IPsec policy

FW1调用IPsec policy

FW2配置安全策略(CLI)
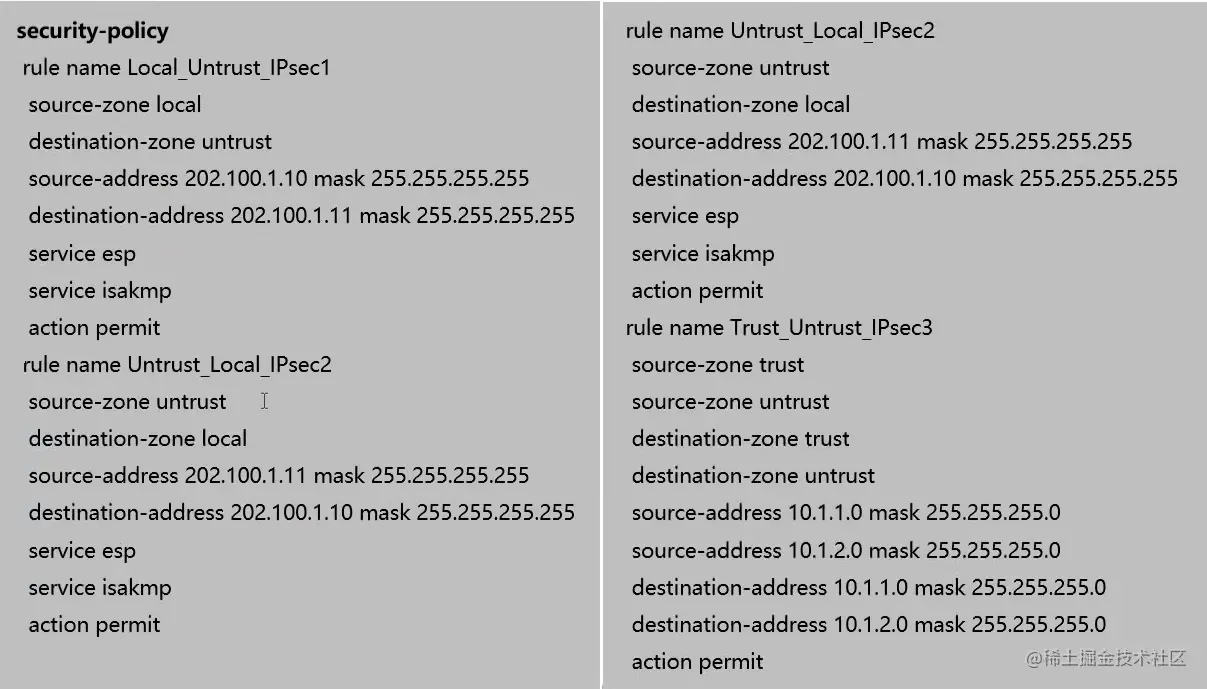
FW1查看IPsec状态(Web)
点击【监控】,查看IPsec协商状态。
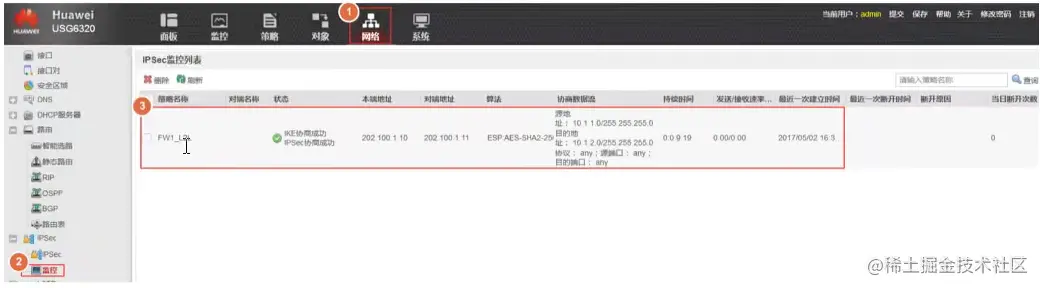
IPsec通信网络测试
在PC1上ping测试到PC2的地址,测试感兴趣流的连通性。
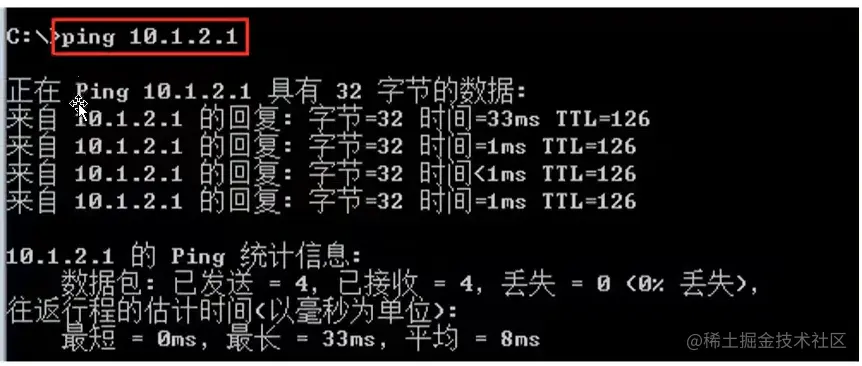
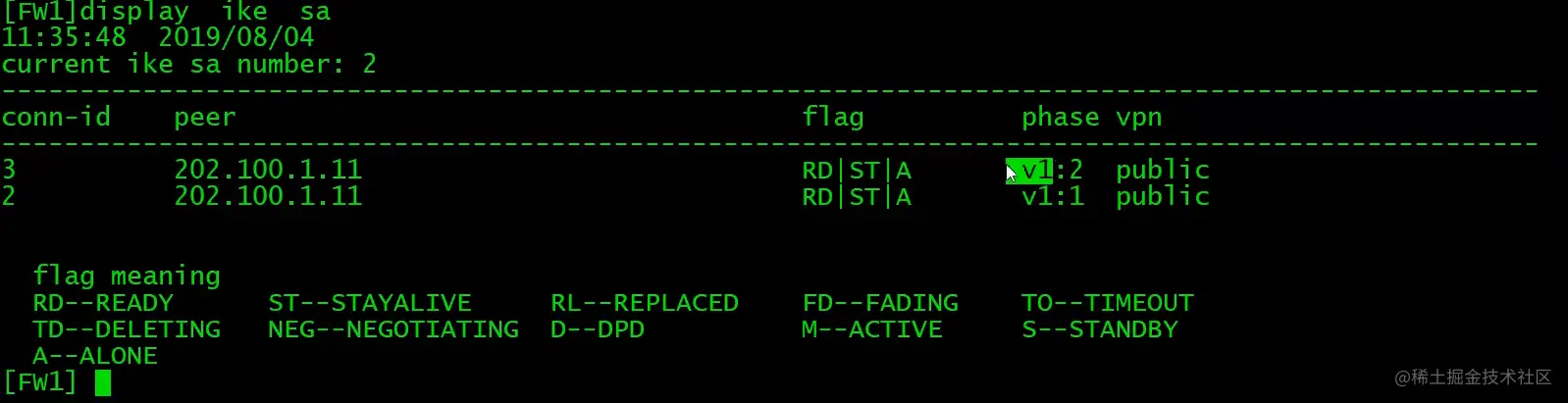
FW1查看IKE SA
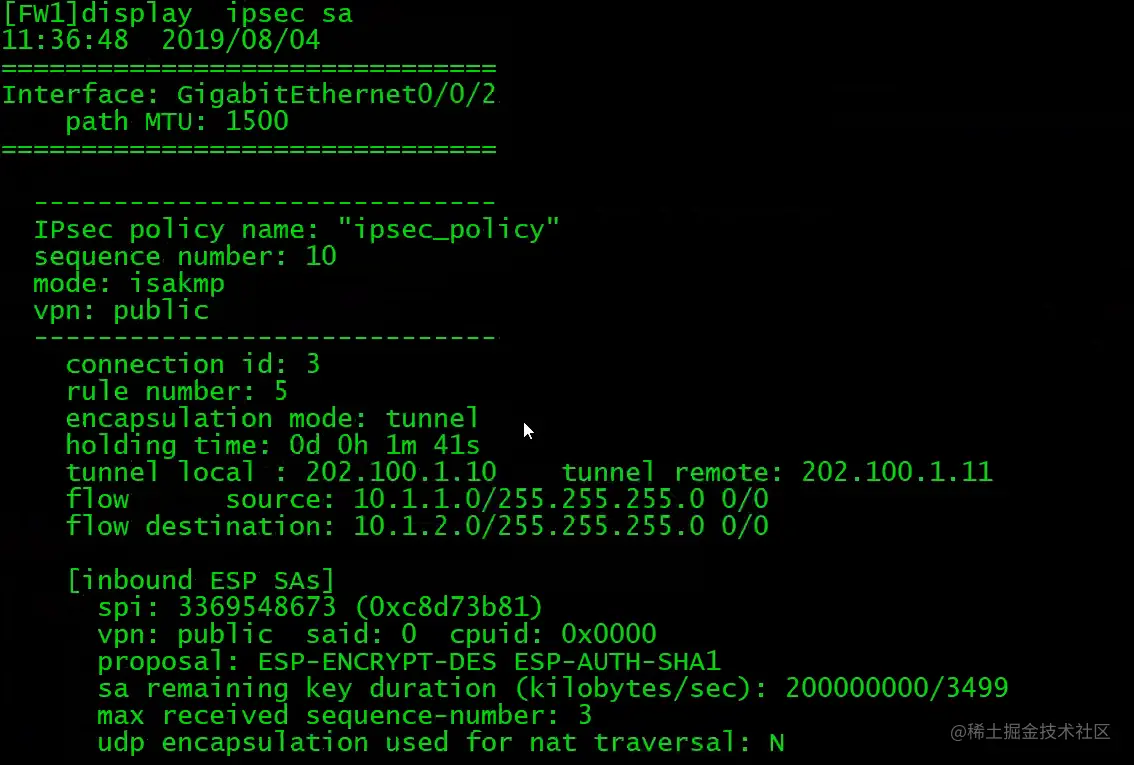
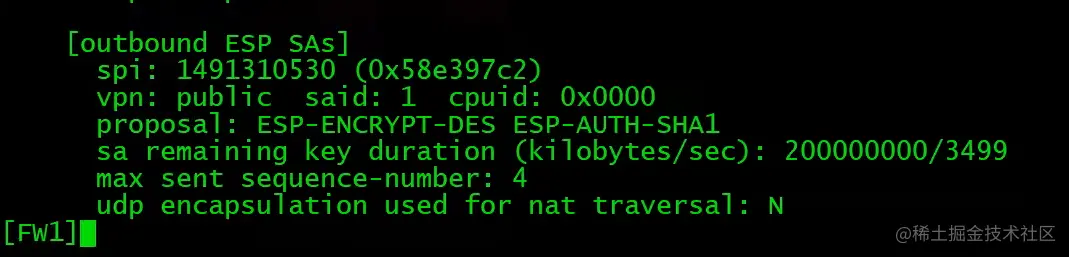
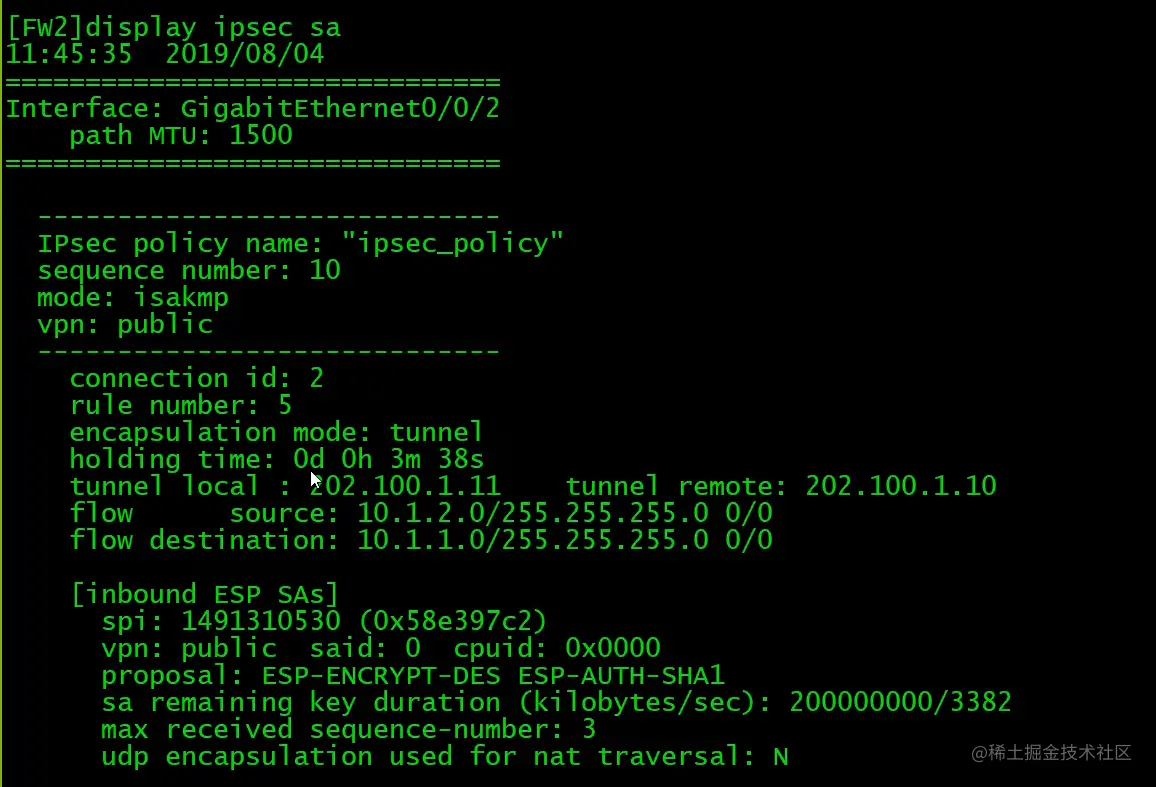
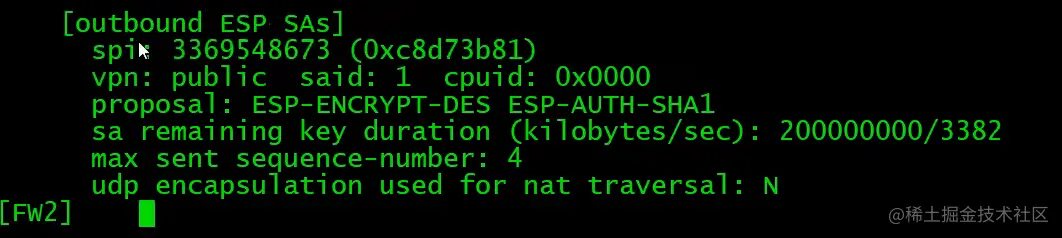
FW1查看IPsec SA
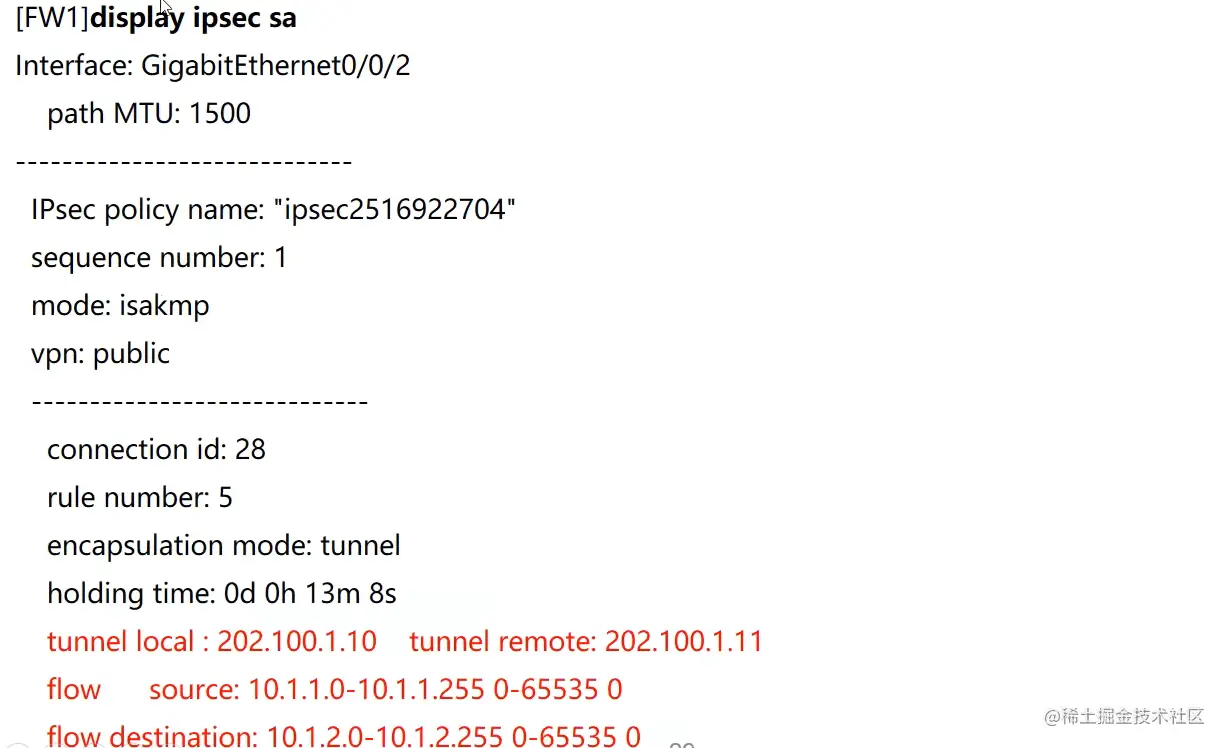
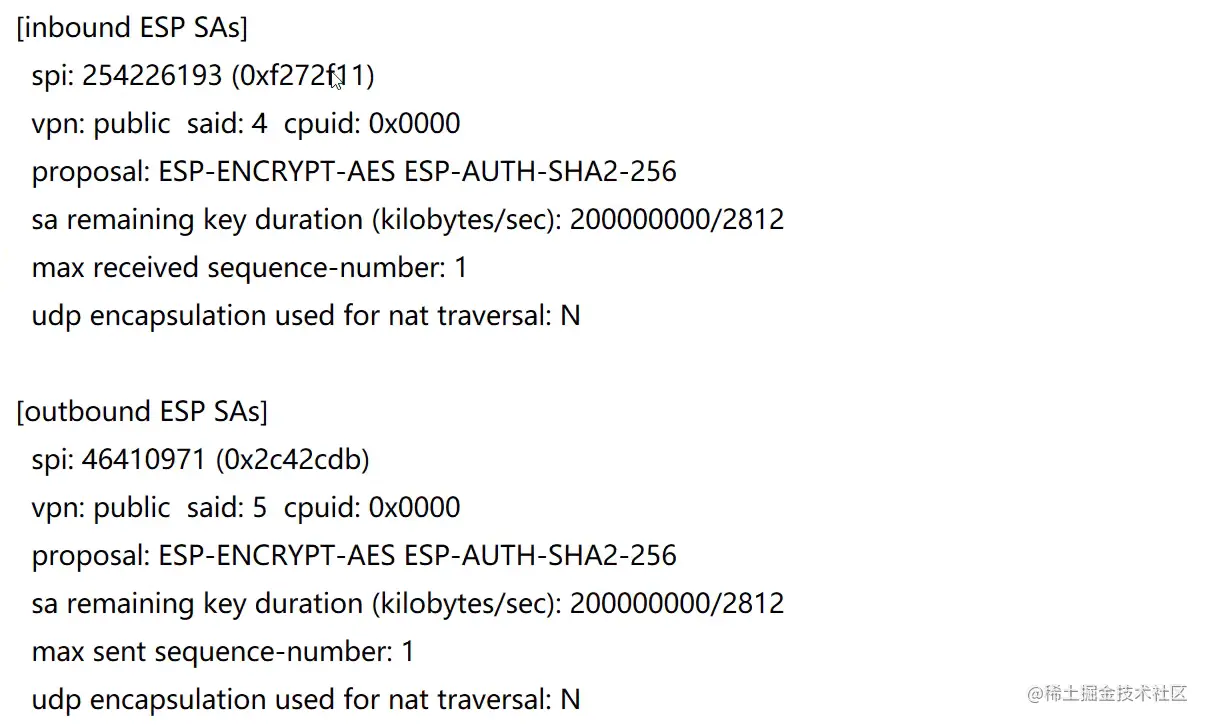
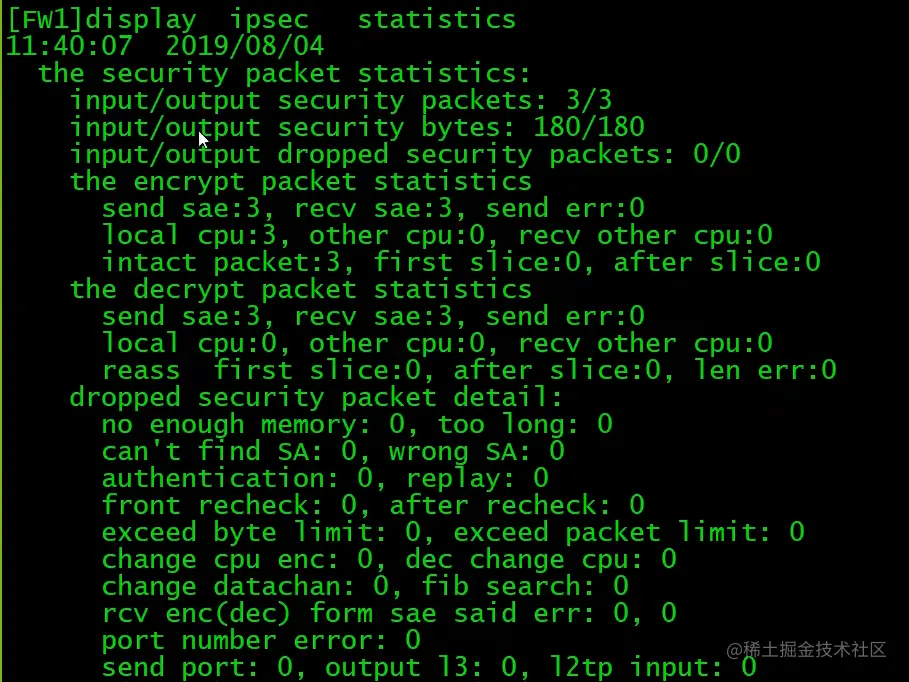
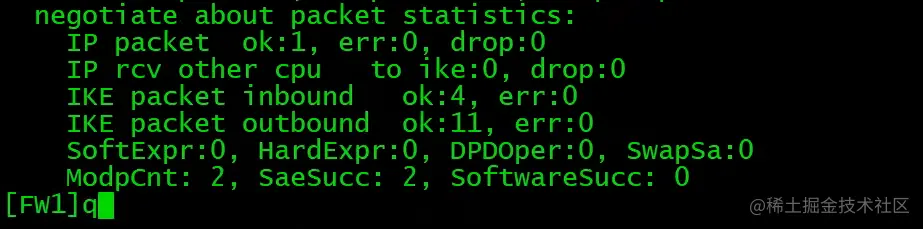
FW1查看加解密数量

实验
SW1
- interface Ethernet0/0/4
- description Link_FW1_G0/0/0
- port link-type access
- port default vlan 16
- interface Ethernet0/0/8
- description Link_FW2_G0/0/0
- port link-type access
- port default vlan 16
- interface Ethernet0/0/21
- description Link_HCNP_MGMT
- port link-type access
- port default vlan 16
- interface Ethernet0/0/1
- description Link_FW1_G0/0/1
- port link-type access
- port default vlan 10
- interface Ethernet0/0/9
- description Link_HCNP_Dot1x(PC1)
- port link-type access
- port default vlan 10
- interface Ethernet0/0/5
- description Link_FW2_G0/0/1
- port link-type access
- port default vlan 20
- interface Ethernet0/0/24
- description Link_HCNP_VPN_Client(PC2)
- port link-type access
- port default vlan 20
- interface Ethernet0/0/2
- description Link_FW1_G0/0/2
- port link-type access
- port default vlan 40
- interface Ethernet0/0/23
- description Link_HCNP_Untrust
- port link-type access
- port default vlan 40
- interface Ethernet0/0/6
- description Link_FW2_G0/0/2
- port link-type access
- port default vlan 40
- 复制代码
FW1
- int g0/0/0
- ip address 192.168.0.10 24
- int g0/0/1
- ip address 10.1.1.10 24
- int g0/0/2
- ip address 202.100.1.10 24
- firewall zone trust
- add int g0/0/1
- firewall zone untrust
- add int g0/0/2
- ip route-static 0.0.0.0 0.0.0.0 202.100.1.11
- ike proposal 10
- encryption-algorithm aes-192
- authentication-algorithm md5
- ike peer fw2
- exchange-mode main
- pre-shared-key Huawei@123
- ike-proposal 10
- remote-address 202.100.1.11
- undo version 2
- acl 3000
- rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
- ipsec proposal 10
- encapsulation-mode tunnel
- esp encryption-algorithm des
- esp authentication-algorithm sha1
- ipsec policy ipsec_policy 10 isakmp
- security acl 3000
- ike-peer fw2
- proposal 10
- int g0/0/2
- ipsec policy ipsec_policy
- 复制代码
FW2
- int g0/0/0
- ip addres 192.168.0.11 24
- int g0/0/1
- ip address 10.1.2.10 24
- int g0/0/2
- ip address 202.100.1.11 24
- service-manage ping permit
- firewall zone untrust
- add int g0/0/2
- firewall zone trust
- add int g0/0/1
- ip route-static 0.0.0.0 0.0.0.0 202.100.1.10
- ike proposal 10
- encryption-algorithm aes-192
- authentication-algorithm md5
- ike peer fw1
- exchange-mode main
- pre-shared-key Huawei@123
- ike-proposal 10
- remote-address 202.100.1.10
- undo version 2
- acl 3000
- rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
- ipsec proposal 10
- encapsulation-mode tunnel
- esp encryption-algorithm des
- esp authentication-algorithm sha1
- ipsec policy ipsec_policy 10 isakmp
- security acl 3000
- ike-peer fw1
- proposal 10
- int g0/0/2
- ipsec policy ipsec_policy
- 复制代码
查看
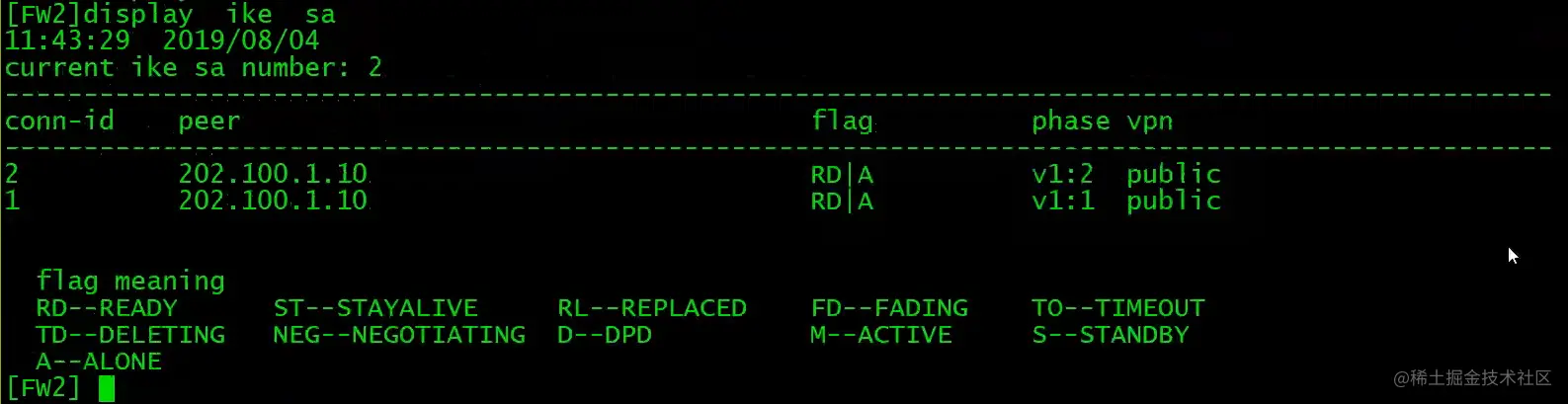
在ipsec policy没有配置auto-neg下,需要先在PC上通过PING触发IPSec隧道建立。(前提是防火墙策略已经配置完成,如local<->untrust,需放通ISKAMP和ESP,trust<->unstrust,需放通地址间所有流量)
-
相关阅读:
分布式进化算法
GraphRAG学习小结(4)
算法基础:堆【以大根堆为例】
每日三题 8.12
RCNN算法思想简单讲解概述————(究极简单的讲述和理解)
MobTech ShareSDK Android端快速集成
CentOS8迁移tencentOS实践
【接口测试】如何在 Eolink Apilkit 中使用 cookie ?
TS的class 继承 类型约束
安装docker-compose
- 原文地址:https://blog.csdn.net/guolianggsta/article/details/126688713
