-
Linux--CE-->DNS服务器详解
1.DNS的解析流程
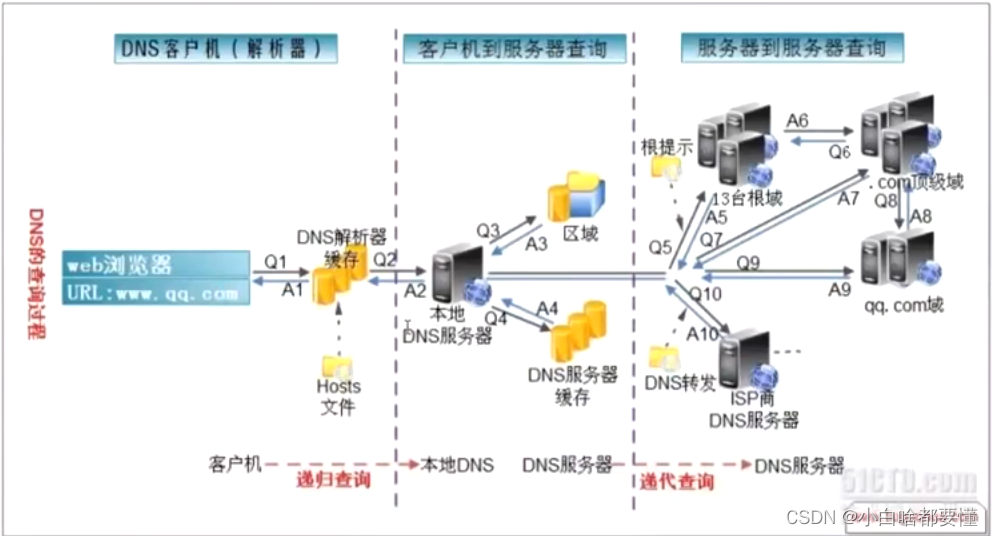
(1):DNS解析过程:
首先web浏览器此昂要访问URL:www.qq.com,第一步先去浏览器缓存中查询是否存在该域名和地址的映射,没查到第二步去本机Windows上查询是否在DNS解析器缓存中查询域名和ip的映射,第三步再去Linux中hosts文件中查看是否配置了这个域名和地址的关系,没找到,递归向本地DNS服务器去查询,本地DNS服务器先去查找DNS服务器缓存,看是否加载过该路径,有则直接返回地址,没有则去本地DNS所管理的区域中查询是否有这台主机,有则返回地址,没有则本地DNS服务器去查询根服务器,,根服务器中存有顶级域名服务器,根域名服务器返回顶级域名服务器域名和地址,本地DNS服务器去顶级域名服务器中查询,顶级域名服务器中查询到顶级域名com且存着二级域名服务器域名和地址,向本地DNS服务器返回二级域名服务器域名和地址,本地域名解析服务器去二级域名服务器寻找,找到qq.com,递归向前返回地址给浏览器且在DNS服务器缓存中进行记录,方便下次访问时的查找;
(2):递归和迭代查询:在客户机解析URL并且向服务器查询的过程属于是递归查询,逐级查询,从客户机到服务器;本地DNS服务器分别去根服务器,二级服务器,三级服务器查询地址属于是迭代查询,逐个查询;
2.DNS主从配置: 需要两台机器: 一台为主dns服务器,一台为从DNS服务器
(1):首先配置主服务器:
#:打开主配置文件,进行如下配置:
- [root@rhce-128 ~]# vim /etc/named.conf
- options {
- listen-on port 53 { 192.168.188.128; };
- #listen-on-v6 port 53 { ::1; };
- directory "/var/named";
- dump-file "/var/named/data/cache_dump.db";
- statistics-file "/var/named/data/named_stats.txt";
- memstatistics-file "/var/named/data/named_mem_stats.txt";
- recursing-file "/var/named/data/named.recursing";
- secroots-file "/var/named/data/named.secroots";
- allow-query { 192.168.188.0; };
- };
- zone "openlab.com" IN {
- type master;
- file "openlab.zone";
- };
- #include "/etc/named.rfc1912.zones";
- include "/etc/named.root.key";
#:还需要有多个IP给对应的服务:
- [root@rhce-128 ~]# nmcli
- ens160: connected to ens160
- "VMware VMXNET3 Ethernet Controller"
- ethernet (vmxnet3), 00:0C:29:E8:3C:A0, hw, mtu 1500
- ip4 default
- inet4 192.168.188.128/24
- inet4 192.168.188.100/24
- inet4 192.168.188.200/24
- inet4 192.168.188.140/24
- inet6 fe80::d856:2d39:81e6:f0d7/64
- lo: unmanaged
#:dns工作目录在/var/named/下,所以要去这个目录下面去创建 openlab.zone这个文件:并进行如下配置:
#:我这里的把128给dns服务器,其他的服务,mail.openlab.com,ftp,dhcp,www,web服务全部都给140:(没有规定说域名必须解析为不同的IP)
#:配置主从同步的设置:
先配置存货时间
配置SOA
配置NS :有NS记录一定会有A记录;
配置MX
#下面写正向解析记录:
解析dns
解析mail
解析ftp
解析dhcp
解析www
配置别名
#这里的注释用分号(;)
- [root@rhce-128 named]# cd /var/named/
- [root@rhce-128 named]# ll
- tatal 0
- -rw-r--r--. 1 root named 643 Aug 1 16:53 openlab.zone
- [root@rhce-128 named]# vim openlab.zone
- ------------------------------------------------------------------
- $TTL 1D
- #name IN SOA
- @ IN SOA dns.openlab.com. test.163.com ( // 邮箱可随便给test.163.com
- 0
- 1D
- 1H
- 1W
- 3H )
- ;注释
- IN NS dns.openlab.com.
- IN MX 10 mail.openlab.com.
- dns.openlab.com. IN A 192.168.188.140
- mail.openlab.com. IN A 192.168.188.100
- ftp IN A 192.168.188.100 // 如果只写名字,对应的会在后面加上域名
- dhcp IN A 192.168.188.100
- www IN A 192.168.188.100
- web IN CNAME www
- -------------------------------------------------------------------
#:如果只写名字,会默认的在后面加上域名,openlab.com. 所以如果写为ftp.openlab.com那么还是会在后面加上openlab.com.;只有在后面加点(.),才会被识别为全限定名称,不加点,只会被认为是名字,还会在后面加域名;
(2):常规操作,设置防火墙关闭,以及安全上下文宽容模式,永久设置在我之前的文章中有所提及,这里就不在详细说了:
- [root@rhce-128 named]# systemctl status firewalld
- ● firewalld.service - firewalld - dynamic firewall daemon
- Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled)
- Active: inactive (dead)
- Docs: man:firewalld(1)
- [root@rhce-128 named]# getenforce
- Permissive
- [root@rhce-128 named]#
(3):检查配置文件语法是否合法,并重新启动服务:
- [root@rhce-128 named]# named-checkconf
- [root@rhce-128 named]# named-checkzone dns.openlab.com openlab.zone
- openlab.zone:12: ignoring out-of-zone data (mail.openlab.com)
- zone dns.openlab.com/IN: dns.openlab.com/MX 'mail.openlab.com' (out of zone) has no addresses records (A or AAAA)
- zone dns.openlab.com/IN: loaded serial 0
- OK
- [root@rhce-128 named]#
- [root@rhce-128 named]# systemctl restart named
- [root@rhce-128 named]#
(4):测试:
- [root@rhce-128 named]# host -a dns.openlab.com 192.168.188.128
- Trying "dns.openlab.com"
- Using domain server:
- Name: 192.168.188.128
- Address: 192.168.188.128#53
- Aliases:
- ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24644
- ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 0
- ;; QUESTION SECTION:
- ;dns.openlab.com. IN ANY
- ;; ANSWER SECTION:
- dns.openlab.com. 86400 IN A 192.168.188.128
- ;; AUTHORITY SECTION:
- openlab.com. 86400 IN NS dns.openlab.com.
- Received 63 bytes from 192.168.188.128#53 in 0 ms
- [root@rhce-128 named]#
3.使用httpd服务演示安全上下文值的设定(selinux)
(1)先关闭防火墙:
- [root@server ~]# systemctl stop firewalld
- [root@server ~]# systemctl status firewalld
- ● firewalld.service - firewalld - dynamic firewall daemon
- Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled)
- Active: inactive (dead)
- Docs: man:firewalld(1)
- [root@server ~]#
(2)查看selinux配置文件:
- [root@server ~]# cat /etc/selinux/config
- # This file controls the state of SELinux on the system.
- # SELINUX= can take one of these three values:
- # enforcing - SELinux security policy is enforced.
- # permissive - SELinux prints warnings instead of enforcing.
- # disabled - No SELinux policy is loaded.
- SELINUX=permissive
- # SELINUXTYPE= can take one of three two values:
- # targeted - Targeted processes are protected,
- # minimum - Modification of targeted policy. Only selected processes are protected.
- # mls - Multi Level Security protection.
- SELINUXTYPE=targeted
- [root@server ~]#
#:可以看到,selinux有三种状态,分别为enforcing,permissive,disabled,创建一个index.html,通过httpd访问:
#Permissive:
- [root@server conf.d]# setenforce 0
- [root@server conf.d]# getenforce
- Permissive
- [root@server conf.d]#
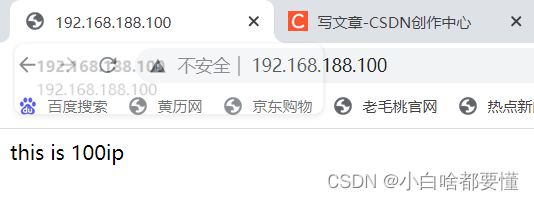
#:Enforcing:
- [root@server conf.d]# setenforce 1
- [root@server conf.d]# getenforce
- Enforcing
- [root@server conf.d]#

#disabled

4.使用web服务端口的改变来演示端口的设定(selinux)

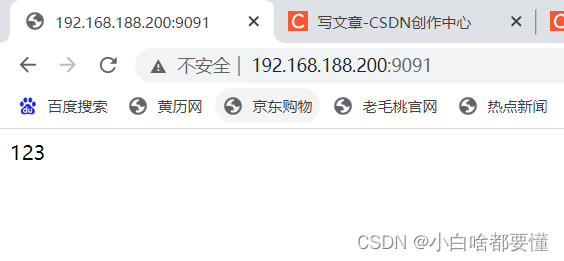
-
相关阅读:
贪心算法之背包问题
NX二次开发:保存时导出PDF并打开
电子设备行业智能供应链系统:打破传统供应链壁垒,提升电子设备企业管理效能
Dart-C、Dart-Kotlin/Java/Swift/Object-C、Kotlin-C数据类型对照表
wsl 中 docker-compose 搭建 kafka 集群出现的外部访问错误
华为、小米OV折叠屏市场再厮杀
FOC系列(二)----继续学习DRV8301芯片
Loss上升,精度却也上升?
CF464E The Classic Problem
ceph存储系统
- 原文地址:https://blog.csdn.net/AiTTTTTT/article/details/126098843
