-
实现DM VXN 的各阶段
实验目的
理解DM-VPN 与IPSEC VPN 的不同。
熟悉DM-VPN 三个阶段的机制。
熟练的配置DM-VPN 三个阶段。实验拓扑
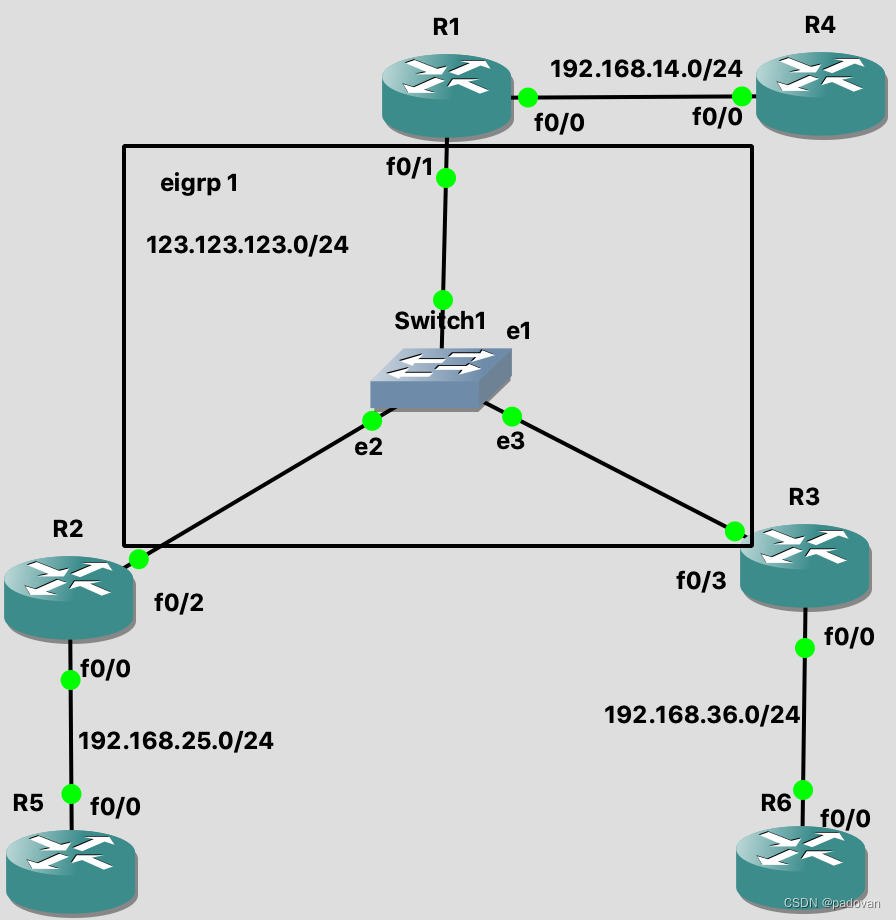
接口IP配置:
- R1(config)#interface e0/0
- R1(config-if)#ip address 192.168.14.1 255.255.255.0
- R1(config-if)#interface e0/1
- R1(config-if)#ip address 123.123.123.1 255.255.255.0
- R1(config-if)#no shutdown
- R2(config)#interface e0/2
- R2(config-if)#ip address 123.123.123.2 255.255.255.0
- R2(config-if)#no shutdown
- R2(config-if)#interface e0/0
- R2(config-if)#ip address 192.168.25.2 255.255.255.0
- R2(config-if)#no shutdown
- R3(config)#interface e0/3
- R3(config-if)#ip address 123.123.123.3 255.255.255.0
- R3(config-if)#no shutdown
- R3(config-if)#interface e0/0
- R3(config-if)#ip address 192.168.36.3 255.255.255.0
- R3(config-if)#no shutdown
路由协议配置:
- R1(config)#router eigrp 1
- R1(config-router)#network 123.123.123.0 0.0.0.255
- R1(config-router)#network 192.168.14.0 0.0.0.0255
- R1(config-router)#no auto-summary
- R2(config)#router eigrp 1
- R2(config-router)#no auto-summary
- R2(config-router)#network 123.123.123.0 0.0.0.255
- R2(config-router)#network 192.168.25.0 0.0.0.255
- R3(config-router)#router eigrp 1
- R3(config-router)#no auto-summary
- R3(config-router)#network 123.123.123.0 0.0.0.255
- R3(config-router)#network 192.168.36.0 0.0.0.255
R1 R2 R3 配置M-GRE。
- R1(config)#interface tunnel 123
- R1(config-if)#ip address 172.16.1.1 255.255.255.0
- R1(config-if)#tunnel source 123.123.123.1
- R1(config-if)#tunnel key 123
- R1(config-if)#tunnel mode gre multipoint
- R2(config)#interface tunnel 123
- R2(config-if)#ip address 172.16.1.2 255.255.255.0
- R2(config-if)#tunnel source e0/2
- R2(config-if)#tunnel key 123
- R2(config-if)#tunnel mode gre multipoint
- R3(config)#interface tunnel 123
- R3(config-if)#ip address 172.16.1.3 255.255.255.0
- R3(config-if)#tunnel source e0/3
- R3(config-if)#tunnel key 123
- R3(config-if)#tunnel mode gre multipoint
R1 R2 R3 上完成NHRP NHS的配置。
- R1(config)#interface tunnel 123
- R1(config-if)#ip nhrp network-id 123 //设置NHRP 的网络ID
- R1(config-if)#ip nhrp authentication 123 //设置NHRP的认证口令
- R1(config-if)#ip nhrp map multicast dynamic //允许多播流在M-GRE 传递
- R(config)#interface tunnel 123
- R2(config-if)#ip nhrp network-id 123
- R2(config-if)#ip nhrp authentication 123
- R2(config-if)#ip nhrp nhs 172.16.1.1 //指定NHS 服务器地址,该地址是HUB 的隧道地址
- R2(config-if)#ip nhrp map 172.16.1.1 123.123.123.1
- //完成NHS服务器隧道逻辑地址和HUB 物理地址的关联
- R2(config-if)#ip nhrp map multicast 123.123.123.1 //设置SPOKE 向HUB 发送多播流量
- R3(config)#interface tunnel 123
- R3(config-if)#ip nhrp network-id 123
- R3(config-if)#ip nhrp authentication 123
- R3(config-if)#ip nhrp nhs 172.16.1.1
- R3(config-if)#ip nhrp map 172.16.1.1 123.123.123.1
- R3(config-if)#ip nhrp map multicast 123.123.123.1
在HUB 和SPOKE 查看NHRP 信息,确认是否得到了SPOKE 的逻辑地址信息和物理地址信息;
- R1#sh ip nhrp
- 172.16.1.2/32 via 172.16.1.2
- Tunnel123 created 00:01:41, expire 01:58:18
- Type: dynamic, Flags: unique registered
- NBMA address: 123.123.123.2
- 172.16.1.3/32 via 172.16.1.3
- Tunnel123 created 00:01:17, expire 01:58:42
- Type: dynamic, Flags: unique registered
- NBMA address: 123.123.123.3
如上现象表明SPOKE 已经利用NHRP将本地的信息共享给HUB。
R1 R2 R3上隧道参与EIGRP。- R1(config)#router eigrp 1
- R1(config-router)#network 172.16.1.1 0.0.0.0
- R2(config)#router eigrp 1
- R2(config-router)#network 172.16.1.2 0.0.0.0
- R3(config)#router eigrp 1
- R3(config-router)#network 172.16.1.3 0.0.0.0
验证R1 作为HUB 是否和R2 R3的建立邻接关系;
- R1#show ip eigrp neighbors
- IP-EIGRP neighbors for process 1
- H Address Interface Hold Uptime SRTT RTO Q Seq
- (sec) (ms) Cnt Num
- 3 172.16.1.3 Tu123 10 00:28:13 96 5000 0 15
- 2 123.123.123.3 Fa0/1 10 00:28:29 745 4470 0 16
- 1 172.16.1.2 Tu123 12 00:28:46 107 5000 0 18
- 0 123.123.123.2 Fa0/1 12 00:28:51 97 582 0 17
- //如上现象表明R1 与R2 R3 正常建立
- R2#show ip eigrp neighbors
- IP-EIGRP neighbors for process 1
- H Address Interface Hold Uptime SRTT RTO Q Seq
- (sec) (ms) Cnt Num
- 2 172.16.1.1 Tu123 8 00:03:11 165 5000 0 12
- 1 123.123.123.1 Fa0/2 5 00:03:15 141 846 0 11
- 0 123.123.123.3 Fa0/2 8 00:03:15 132 792 0 9
- R3#show ip eigrp neighbors
- IP-EIGRP neighbors for process 1
- H Address Interface Hold Uptime SRTT RTO Q Seq
- (sec) (ms) Cnt Num
- 2 172.16.1.1 Tu123 5 00:02:09 1006 5000 0 13
- 1 123.123.123.2 Fa0/3 9 00:02:13 171 1026 0 14
- 0 123.123.123.1 Fa0/3 12 00:02:13 108 648 0 11
验证R1 R2 R3 的路由学习情况;
- R1#show ip route eigrp
- D 192.168.25.0/24 [90/30720] via 123.123.123.2, 00:26:34, FastEthernet0/1
- D 192.168.36.0/24 [90/30720] via 123.123.123.3, 00:28:12, FastEthernet0/1
- //如上现象表明R1已经学习R2 R3身后网络
- R2#show ip route eigrp
- D 192.168.14.0/24 [90/30720] via 123.123.123.1, 00:32:25, FastEthernet0/2
- D 192.168.36.0/24 [90/30720] via 123.123.123.3, 00:32:04, FastEthernet0/2
- R3#show ip route eigrp
- D 192.168.14.0/24 [90/30720] via 123.123.123.1, 00:20:38, FastEthernet0/3
- D 192.168.25.0/24 [90/30720] via 123.123.123.2, 00:15:50, FastEthernet0/3
R1 上M-GRE下关闭EIGRP 水平分割。
- R1(config)#interface tunnel 123
- R1(config-if)#no ip split-horizon eigrp 1
R1 R2 R3 配置IPSEC VXN,并且在Tunnel 123 下应用
- R1(config)#crypto isakmp enable
- R1(config)#crypto isakmp policy 1
- R1(config-isakmp)#authentication pre-share
- R1(config)#crypto isakmp key 6 cisco address 0.0.0.0 0.0.0.0
- //因为对等体地址是动态获取,无法提前已知,所以这里写0.0.0.0 0.0.0.0,等同于ANY。
- R1(config)#crypto ipsec transform-set r1-tr esp-des esp-md5-hmac
- R1(cfg-crypto-trans)#mode transport
- //VXN的隧道模式一定要改为传输
- R1(config)#crypto ipsec profile r1-pf
- R1(ipsec-profile)#set transform-set r1-tr
- //传统的crytpo map是必须配置set peer 指定对等体,
- //和macth address 匹配感兴趣流,但是DM-VPN 这两部分都是缺失的,
- //所以才创建IPSEC 配置文件,指定转换集即可。
- R1(config)#interface tunnel 123
- R1(config-if)#tunnel protection ipsec profile r1-pf
- R2(config)#crypto isakmp enable
- R2(config)#crypto isakmp policy 1
- R2(config-isakmp)#authentication pre-share
- R2(config)#crypto isakmp key 6 cisco address 0.0.0.0 0.0.0.0
- R2(config)#crypto ipsec transform-set r2-tr esp-des esp-md5-hmac
- R2(cfg-crypto-trans)#mode transport
- R2(config)#crypto ipsec profile r2-pf
- R2(ipsec-profile)#set transform-set r2-tr
- R2(ipsec-profile)#interface tunnel 123
- R2(config-if)#crypto ipsec profile r2-pf
- R3(config)#crypto isakmp enable
- R3(config)#crypto isakmp policy 1
- R3(config-isakmp)#authentication pre-share
- R3(config)#crypto isakmp key 6 cisco address 0.0.0.0 0.0.0.0
- R3(config)#crypto ipsec transform-set r3-tr esp-des esp-md5-hmac
- R3(cfg-crypto-trans)#mode transport
- R3(config)#crypto ipsec profile r3-pf
- R3(ipsec-profile)#set transform-set r3-tr
- R3(config)#interface tunnel 123
- R3(config-if)#tunnel protection ipsec profile r3-pf
利用命令行校验连通性和是否加密。
- R4#traceroute 192.168.25.5
- Type escape sequence to abort.
- Tracing the route to 192.168.25.5
- 1 192.168.14.1 1052 msec 72 msec 72 msec
- 2 123.123.123.2 136 msec 76 msec 104 msec
- 3 *
- 192.168.25.5 80 msec 108 msec
- R4#traceroute 192.168.36.6
- Type escape sequence to abort.
- Tracing the route to 192.168.36.6
- 1 192.168.14.1 1064 msec 72 msec 72 msec
- 2 123.123.123.3 76 msec 72 msec 104 msec
- 3 *
- 192.168.36.6 52 msec 108 msec
- R1#show crypto engine connections active
- ID Interface IP-Address State Algorithm Encrypt Decrypt
- 1 FastEthernet0/1 123.123.123.1 set HMAC_SHA+DES_56_CB 0 0
- 2001 FastEthernet0/1 123.123.123.1 set DES+MD5 0 92
- 2002 FastEthernet0/1 123.123.123.1 set DES+MD5 93 0
DMVXN阶段1完成
阶段2方法1:在阶段1的基础上:
- R1(config)#interface tunnel 123
- R1(config-if)#no ip next-hop-self eigrp 1
- //当R1共享SPOKE 路由时,不会修改下一跳信息,保持原有的下一跳地址
DMVXN阶段2方法1完成
DMVXN阶段2方法2
- R1(config)#interface tunnel 123
- R1(config-if)#ip split-horizon eigrp 1 // 开启水平分割
- R1(config-if)#ip summary-address eigrp 1 172.16.0.0 255.255.0.0//手动路由汇总
在中心和分支上配置捷径特性。
- R1(config)#interface tunnel 123
- R1(config-if)#ip nhrp redirect
- R2(config)#interface tunnel 123
- R2(config-if)#ip nhrp redirect
- R3(config)#interface tunnel 123
- R3(config-if)#ip nhrp redirect
-
相关阅读:
安利几个堪称黑科技的电脑软件
前端工程化工具系列(七)—— PNPM(v9.2.0):高性能的 NPM 替代品
【运维开源】轻量级低侵入式在线构建、自动部署、日常运维、项目监控-JPOM
图算融合使能不同优化等级尝试网络性能调优
nginx 正则匹配测试工具
Leo赠书活动-09期 【如何拿下数学】文末送书
Dubbo的设计理念原来就藏在这三张图中,读完恍然大悟了
如何自动注册推特推广号,推特注册的具体步骤
Revit MEP 平面视图中(立管)怎么设置二维表达?
【AI】PyTorch入门(五):构建神经模型
- 原文地址:https://blog.csdn.net/qq_43210022/article/details/125950955
