-
HSCTF2022-re题解
HSCTF2022
题目地址:https://github.com/scnu-sloth/hsctf-2022-trial
感谢师傅们的题目!checkininin
_int64 __fastcall main(int a1, char **a2, char **a3) { int i; // [rsp+Ch] [rbp-B4h] char v5[32]; // [rsp+10h] [rbp-B0h] char v6[32]; // [rsp+30h] [rbp-90h] char v7[31]; // [rsp+50h] [rbp-70h] char v8[32]; // [rsp+6Fh] [rbp-51h] BYREF char v9[41]; // [rsp+8Fh] [rbp-31h] BYREF unsigned __int64 v10; // [rsp+B8h] [rbp-8h] v10 = __readfsqword(0x28u); v5[0] = -119; v5[1] = -85; v5[2] = 0; v5[3] = 85; v5[4] = -23; v5[5] = -107; v5[6] = -58; v5[7] = -16; v5[8] = 124; v5[9] = -21; v5[10] = 28; v5[11] = 87; v5[12] = 43; v5[13] = 30; v5[14] = 106; v5[15] = -18; v5[16] = 80; v5[17] = 78; v5[18] = -55; v5[19] = 97; v5[20] = 124; v5[21] = -86; v5[22] = 98; v5[23] = 39; v5[24] = -74; v5[25] = 11; v5[26] = -31; v5[27] = 35; v5[28] = 74; v5[29] = 24; v5[30] = -61; v5[31] = 74; v6[0] = 108; v6[1] = -124; v6[2] = -80; v6[3] = 25; v6[4] = -16; v6[5] = 72; v6[6] = -5; v6[7] = -61; v6[8] = -115; v6[9] = -120; v6[10] = 122; v6[11] = 109; v6[12] = -37; v6[13] = -87; v6[14] = 92; v6[15] = 8; v6[16] = 10; v6[17] = 69; v6[18] = 0x80; v6[19] = -27; v6[20] = 10; v6[21] = 14; v6[22] = -74; v6[23] = -96; v6[24] = -53; v6[25] = 30; v6[26] = -4; v6[27] = 114; v6[28] = -115; v6[29] = 84; v6[30] = -42; v6[31] = 23; v7[0] = -96; v7[1] = 103; v7[2] = 68; v7[3] = -101; v7[4] = 121; v7[5] = -23; v7[6] = -65; v7[7] = 111; v7[8] = -96; v7[9] = -126; v7[10] = 46; v7[11] = -120; v7[12] = -123; v7[13] = 109; v7[14] = -11; v7[15] = 27; v7[16] = -95; v7[17] = -7; v7[18] = 30; v7[19] = 55; v7[20] = 127; v7[21] = -4; v7[22] = -69; v7[23] = 35; v7[24] = -74; v7[25] = 125; v7[26] = 7; v7[27] = 117; v7[28] = -113; v7[29] = -112; v7[30] = -13; qmemcpy(v8, "y-;", 3); v8[3] = -105; v8[4] = -93; v8[5] = 6; v8[6] = 79; v8[7] = -35; v8[8] = 14; v8[9] = 98; v8[10] = -43; v8[11] = 4; v8[12] = -2; v8[13] = 44; v8[14] = -123; v8[15] = -100; v8[16] = -72; v8[17] = -95; v8[18] = -83; v8[19] = 8; v8[20] = -20; v8[21] = 81; v8[22] = 23; v8[23] = 61; v8[24] = -21; v8[25] = -103; v8[26] = 39; v8[27] = 72; v8[28] = 5; v8[29] = 105; v8[30] = -3; v8[31] = -71; strcpy(v9, "Y"); memset(&v9[2], 0, 31); puts("Let's checkininin------!"); __isoc99_scanf("%32s", &v9[1]); for ( i = 0; i <= 31; ++i ) { v9[i + 1] ^= v5[i]; v9[i + 1] ^= v6[i]; v9[i + 1] ^= v7[i]; } if ( !memcmp(&v9[1], &v8[1], 0x20uLL) ) puts("Oh, ininin :D"); else puts("Oh, outoutout :X"); return 0LL; }- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
EXP
#include#include #include int main(int a1, char **a2, char **a3) { int i; // [rsp+Ch] [rbp-B4h] char v5[32]; // [rsp+10h] [rbp-B0h] char v6[32]; // [rsp+30h] [rbp-90h] char v7[31]; // [rsp+50h] [rbp-70h] char v8[33]={0}; // [rsp+6Fh] [rbp-51h] BYREF char v9[41]; // [rsp+8Fh] [rbp-31h] BYREF unsigned __int64 v10; // [rsp+B8h] [rbp-8h] v5[0] = -119; v5[1] = -85; v5[2] = 0; v5[3] = 85; v5[4] = -23; v5[5] = -107; v5[6] = -58; v5[7] = -16; v5[8] = 124; v5[9] = -21; v5[10] = 28; v5[11] = 87; v5[12] = 43; v5[13] = 30; v5[14] = 106; v5[15] = -18; v5[16] = 80; v5[17] = 78; v5[18] = -55; v5[19] = 97; v5[20] = 124; v5[21] = -86; v5[22] = 98; v5[23] = 39; v5[24] = -74; v5[25] = 11; v5[26] = -31; v5[27] = 35; v5[28] = 74; v5[29] = 24; v5[30] = -61; v5[31] = 74; v6[0] = 108; v6[1] = -124; v6[2] = -80; v6[3] = 25; v6[4] = -16; v6[5] = 72; v6[6] = -5; v6[7] = -61; v6[8] = -115; v6[9] = -120; v6[10] = 122; v6[11] = 109; v6[12] = -37; v6[13] = -87; v6[14] = 92; v6[15] = 8; v6[16] = 10; v6[17] = 69; v6[18] = 0x80; v6[19] = -27; v6[20] = 10; v6[21] = 14; v6[22] = -74; v6[23] = -96; v6[24] = -53; v6[25] = 30; v6[26] = -4; v6[27] = 114; v6[28] = -115; v6[29] = 84; v6[30] = -42; v6[31] = 23; v7[0] = -96; v7[1] = 103; v7[2] = 68; v7[3] = -101; v7[4] = 121; v7[5] = -23; v7[6] = -65; v7[7] = 111; v7[8] = -96; v7[9] = -126; v7[10] = 46; v7[11] = -120; v7[12] = -123; v7[13] = 109; v7[14] = -11; v7[15] = 27; v7[16] = -95; v7[17] = -7; v7[18] = 30; v7[19] = 55; v7[20] = 127; v7[21] = -4; v7[22] = -69; v7[23] = 35; v7[24] = -74; v7[25] = 125; v7[26] = 7; v7[27] = 117; v7[28] = -113; v7[29] = -112; v7[30] = -13; memcpy(v8, "y-;", 3); v8[3] = -105; v8[4] = -93; v8[5] = 6; v8[6] = 79; v8[7] = -35; v8[8] = 14; v8[9] = 98; v8[10] = -43; v8[11] = 4; v8[12] = -2; v8[13] = 44; v8[14] = -123; v8[15] = -100; v8[16] = -72; v8[17] = -95; v8[18] = -83; v8[19] = 8; v8[20] = -20; v8[21] = 81; v8[22] = 23; v8[23] = 61; v8[24] = -21; v8[25] = -103; v8[26] = 39; v8[27] = 72; v8[28] = 5; v8[29] = 105; v8[30] = -3; v8[31] = -71; v8[32] ='Y'; for ( i = 0; i <= 31; ++i ) { v8[i + 1] ^= v5[i]; v8[i + 1] ^= v6[i]; v8[i + 1] ^= v7[i]; printf("%c",v8[i+1]); } } //hsctf{_R34LLY__EZ___XOROROR!!!_} 最后一位手改} - 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
应该最后一位有些小细节没搞定,但可以猜
5rn4
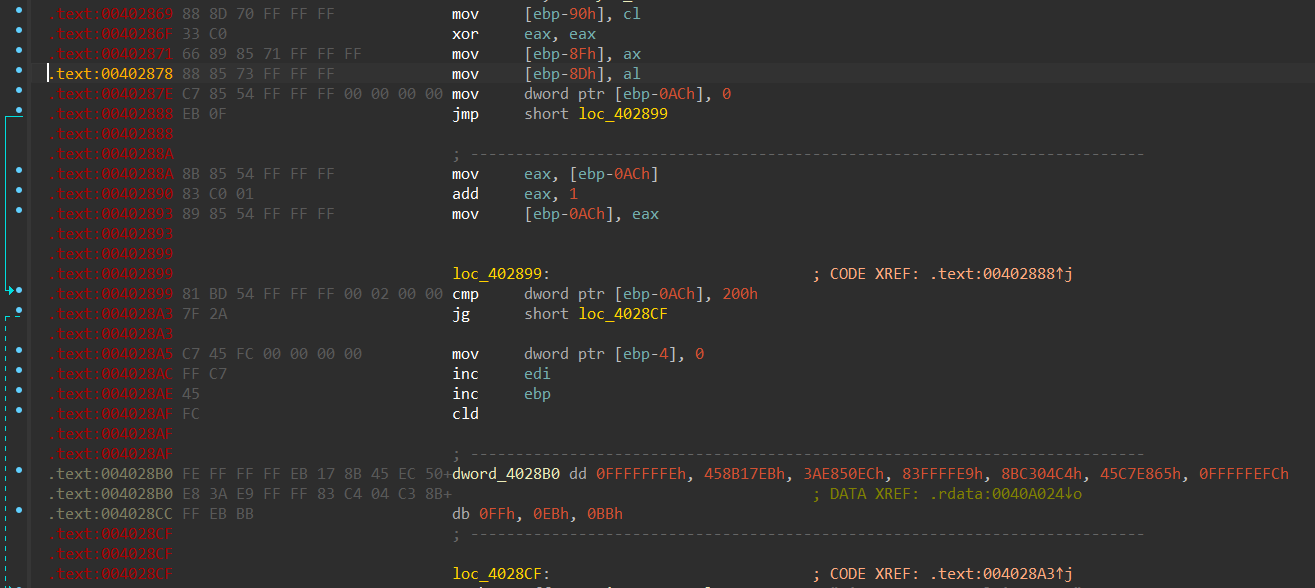
盲猜花指令,先全部转代码分分析
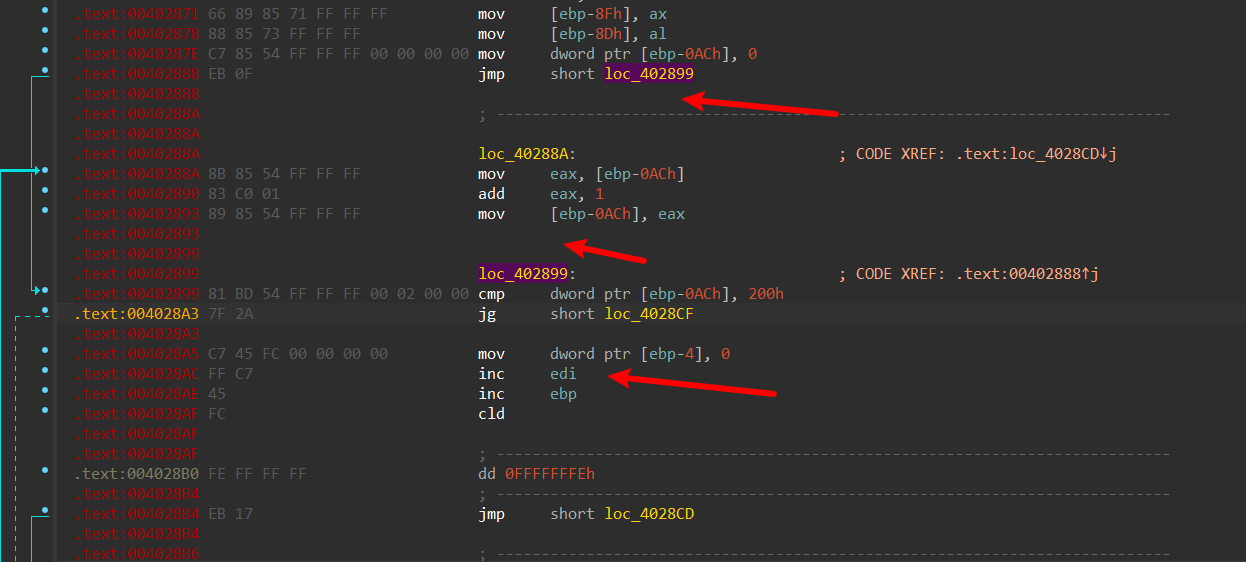
不能理解在没return前直接自增ebp,把0xff去nop

恢复了函数逻辑
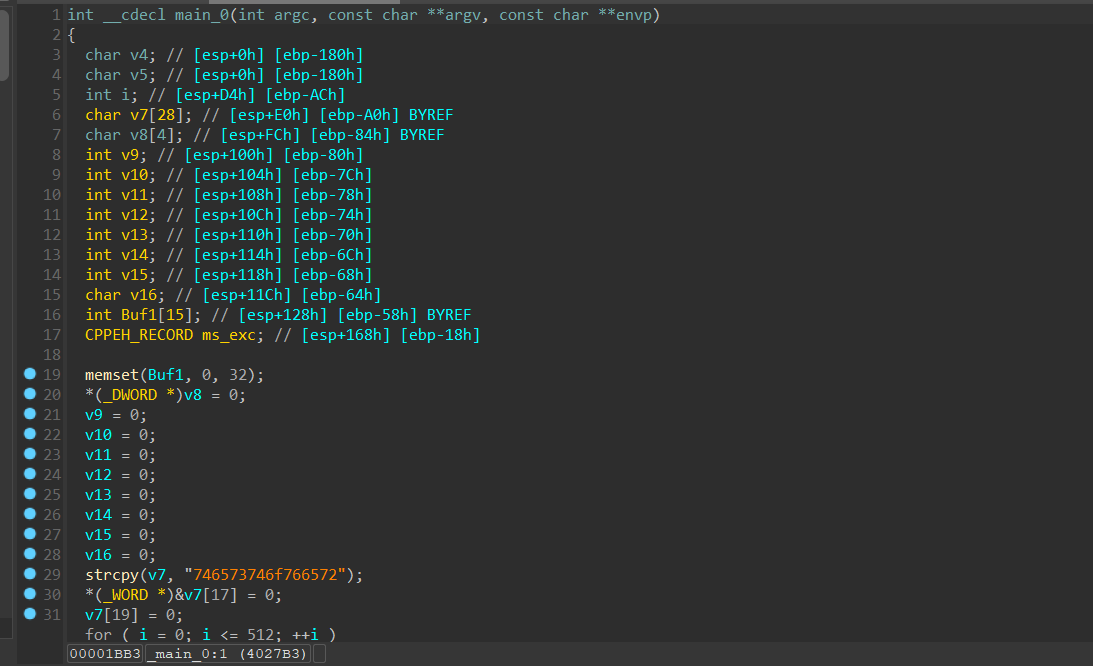
手修补一下
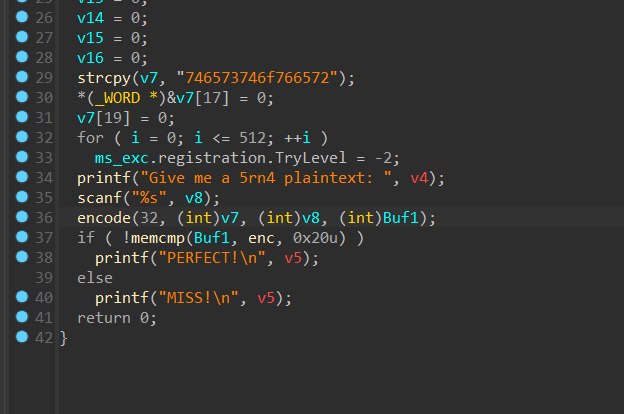

加密是sm4
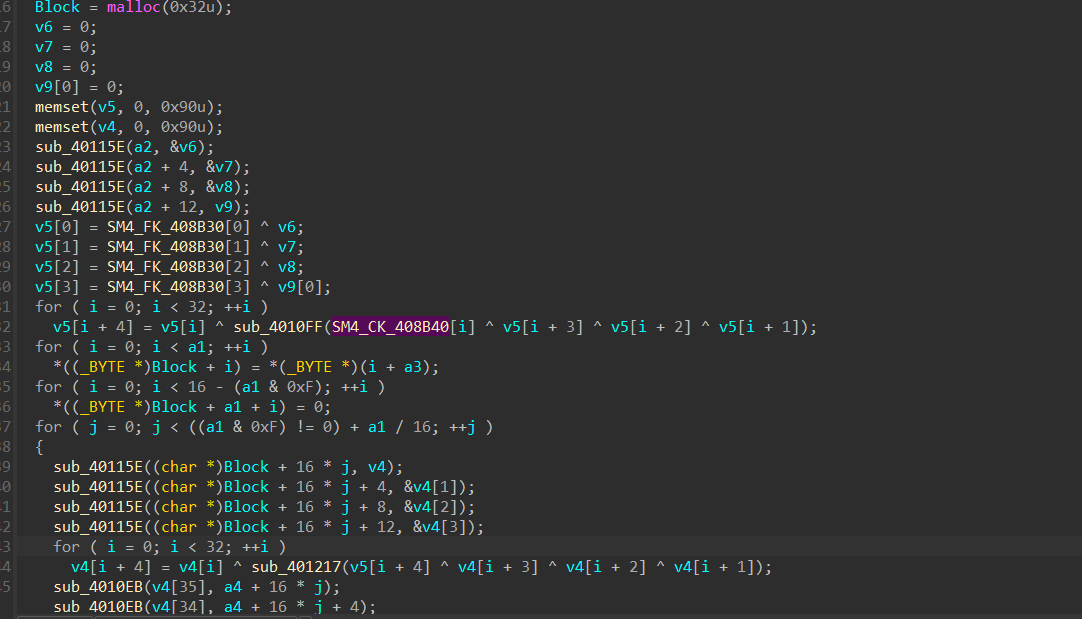
简单手修一下
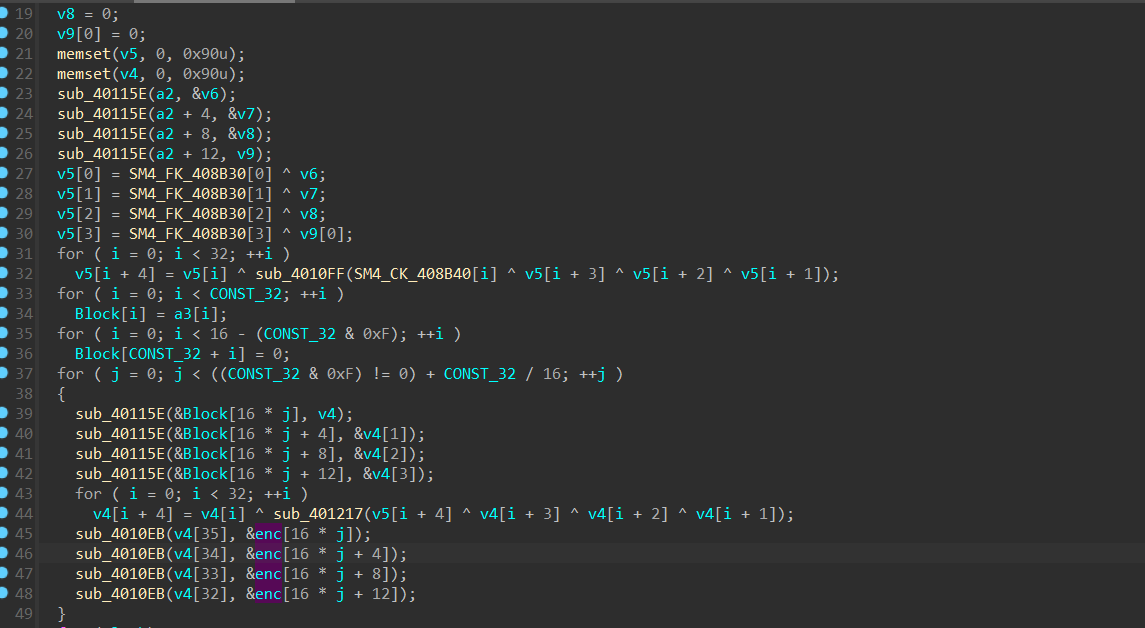
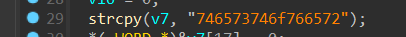
这个应是key,把enc也dump下来
我们找找v8,但又反调试,一直卡着
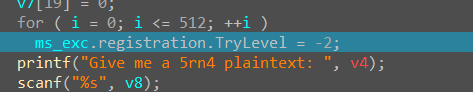
发现有个seh
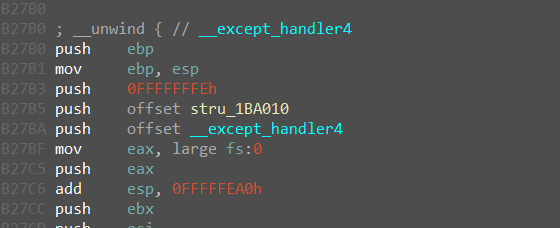
要进行512次异常,反调试真的烦,想nop掉的时候在异常中发现这个
在异常中发现密文
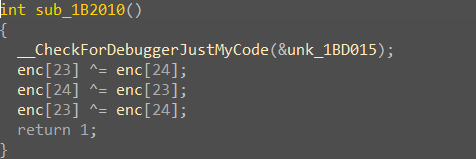
好家伙,吓得我赶紧交叉引用一手
EXP
#define _SM4_H_ #include#include #include #define char unsigned char #define u32 unsigned long void four_uCh2uLong(char *in, u32 *out); //四字节转换成u32 void uLong2four_uCh(u32 in, char *out); //u32转换成四字节 unsigned long move(u32 data, int length); //左移,保留丢弃位放置尾部 unsigned long func_key(u32 input); //先使用Sbox进行非线性变化,再将线性变换L置换为L' unsigned long func_data(u32 input); //先使用Sbox进行非线性变化,再进行线性变换L void print_hex(char *data, int len); //无符号字符数组转16进制打印 void encode_fun(char len,char *key, char *input, char *output); //加密函数 void decode_fun(char len,char *key, char *input, char *output); //解密函数 /******************************定义系统参数FK的取值****************************************/ const u32 TBL_SYS_PARAMS[4] = { 0xa3b1bac6, 0x56aa3350, 0x677d9197, 0xb27022dc }; /******************************定义固定参数CK的取值****************************************/ const u32 TBL_FIX_PARAMS[32] = { 0x00070e15,0x1c232a31,0x383f464d,0x545b6269, 0x70777e85,0x8c939aa1,0xa8afb6bd,0xc4cbd2d9, 0xe0e7eef5,0xfc030a11,0x181f262d,0x343b4249, 0x50575e65,0x6c737a81,0x888f969d,0xa4abb2b9, 0xc0c7ced5,0xdce3eaf1,0xf8ff060d,0x141b2229, 0x30373e45,0x4c535a61,0x686f767d,0x848b9299, 0xa0a7aeb5,0xbcc3cad1,0xd8dfe6ed,0xf4fb0209, 0x10171e25,0x2c333a41,0x484f565d,0x646b7279 }; /******************************SBox参数列表****************************************/ const char TBL_SBOX[256] = { 0xd6,0x90,0xe9,0xfe,0xcc,0xe1,0x3d,0xb7,0x16,0xb6,0x14,0xc2,0x28,0xfb,0x2c,0x05, 0x2b,0x67,0x9a,0x76,0x2a,0xbe,0x04,0xc3,0xaa,0x44,0x13,0x26,0x49,0x86,0x06,0x99, 0x9c,0x42,0x50,0xf4,0x91,0xef,0x98,0x7a,0x33,0x54,0x0b,0x43,0xed,0xcf,0xac,0x62, 0xe4,0xb3,0x1c,0xa9,0xc9,0x08,0xe8,0x95,0x80,0xdf,0x94,0xfa,0x75,0x8f,0x3f,0xa6, 0x47,0x07,0xa7,0xfc,0xf3,0x73,0x17,0xba,0x83,0x59,0x3c,0x19,0xe6,0x85,0x4f,0xa8, 0x68,0x6b,0x81,0xb2,0x71,0x64,0xda,0x8b,0xf8,0xeb,0x0f,0x4b,0x70,0x56,0x9d,0x35, 0x1e,0x24,0x0e,0x5e,0x63,0x58,0xd1,0xa2,0x25,0x22,0x7c,0x3b,0x01,0x21,0x78,0x87, 0xd4,0x00,0x46,0x57,0x9f,0xd3,0x27,0x52,0x4c,0x36,0x02,0xe7,0xa0,0xc4,0xc8,0x9e, 0xea,0xbf,0x8a,0xd2,0x40,0xc7,0x38,0xb5,0xa3,0xf7,0xf2,0xce,0xf9,0x61,0x15,0xa1, 0xe0,0xae,0x5d,0xa4,0x9b,0x34,0x1a,0x55,0xad,0x93,0x32,0x30,0xf5,0x8c,0xb1,0xe3, 0x1d,0xf6,0xe2,0x2e,0x82,0x66,0xca,0x60,0xc0,0x29,0x23,0xab,0x0d,0x53,0x4e,0x6f, 0xd5,0xdb,0x37,0x45,0xde,0xfd,0x8e,0x2f,0x03,0xff,0x6a,0x72,0x6d,0x6c,0x5b,0x51, 0x8d,0x1b,0xaf,0x92,0xbb,0xdd,0xbc,0x7f,0x11,0xd9,0x5c,0x41,0x1f,0x10,0x5a,0xd8, 0x0a,0xc1,0x31,0x88,0xa5,0xcd,0x7b,0xbd,0x2d,0x74,0xd0,0x12,0xb8,0xe5,0xb4,0xb0, 0x89,0x69,0x97,0x4a,0x0c,0x96,0x77,0x7e,0x65,0xb9,0xf1,0x09,0xc5,0x6e,0xc6,0x84, 0x18,0xf0,0x7d,0xec,0x3a,0xdc,0x4d,0x20,0x79,0xee,0x5f,0x3e,0xd7,0xcb,0x39,0x48 }; void four_uCh2uLong(char *in, u32 *out) { int i = 0; *out = 0; for (i = 0; i < 4; i++) *out = ((u32)in[i] << (24 - i * 8)) ^ *out; } //无符号long型转4字节无符号数组 void uLong2four_uCh(u32 in, char *out) { int i = 0; //从32位unsigned long的高位开始取 for (i = 0; i < 4; i++) *(out + i) = (u32)(in >> (24 - i * 8)); } //左移,保留丢弃位放置尾部 u32 move(u32 data, int length) { u32 result = 0; result = (data << length) ^ (data >> (32 - length)); return result; } //秘钥处理函数,先使用Sbox进行非线性变化,再将线性变换L置换为L' u32 func_key(u32 input) { int i = 0; u32 ulTmp = 0; char ucIndexList[4] = { 0 }; char ucSboxValueList[4] = { 0 }; uLong2four_uCh(input, ucIndexList); for (i = 0; i < 4; i++) { ucSboxValueList[i] = TBL_SBOX[ucIndexList[i]]; } four_uCh2uLong(ucSboxValueList, &ulTmp); ulTmp = ulTmp ^ move(ulTmp, 13) ^ move(ulTmp, 23); return ulTmp; } //加解密数据处理函数,先使用Sbox进行非线性变化,再进行线性变换L u32 func_data(u32 input) { int i = 0; u32 ulTmp = 0; char ucIndexList[4] = { 0 }; char ucSboxValueList[4] = { 0 }; uLong2four_uCh(input, ucIndexList); for (i = 0; i < 4; i++) { ucSboxValueList[i] = TBL_SBOX[ucIndexList[i]]; } four_uCh2uLong(ucSboxValueList, &ulTmp); ulTmp = ulTmp ^ move(ulTmp, 2) ^ move(ulTmp, 10) ^ move(ulTmp, 18) ^ move(ulTmp, 24); return ulTmp; } //解密函数(与加密函数基本一致,只是秘钥使用的顺序不同,即把钥匙反着用就是解密) //len:数据长度 key:密钥 input:输入的加密后数据 output:输出的解密后数据 void decode_fun(char len,char *key, char *input, char *output) { int i = 0,j=0; u32 ulKeyTmpList[4] = { 0 };//存储密钥的u32数据 u32 ulKeyList[36] = { 0 }; //用于密钥扩展算法与系统参数FK运算后的结果存储 u32 ulDataList[36] = { 0 }; //用于存放加密数据 /*开始生成子秘钥*/ four_uCh2uLong(key, &(ulKeyTmpList[0])); four_uCh2uLong(key + 4, &(ulKeyTmpList[1])); four_uCh2uLong(key + 8, &(ulKeyTmpList[2])); four_uCh2uLong(key + 12, &(ulKeyTmpList[3])); ulKeyList[0] = ulKeyTmpList[0] ^ TBL_SYS_PARAMS[0]; ulKeyList[1] = ulKeyTmpList[1] ^ TBL_SYS_PARAMS[1]; ulKeyList[2] = ulKeyTmpList[2] ^ TBL_SYS_PARAMS[2]; ulKeyList[3] = ulKeyTmpList[3] ^ TBL_SYS_PARAMS[3]; for (i = 0; i < 32; i++) //32次循环迭代运算 { //5-36为32个子秘钥 ulKeyList[i + 4] = ulKeyList[i] ^ func_key(ulKeyList[i + 1] ^ ulKeyList[i + 2] ^ ulKeyList[i + 3] ^ TBL_FIX_PARAMS[i]); } /*生成32轮32位长子秘钥结束*/ for (j = 0; j < len / 16; j++) //进行循环加密,并将加密后数据保存 { /*开始处理解密数据*/ four_uCh2uLong(input + 16 * j, &(ulDataList[0])); four_uCh2uLong(input + 16 * j + 4, &(ulDataList[1])); four_uCh2uLong(input + 16 * j + 8, &(ulDataList[2])); four_uCh2uLong(input + 16 * j + 12, &(ulDataList[3])); //解密 for (i = 0; i < 32; i++) { ulDataList[i + 4] = ulDataList[i] ^ func_data(ulDataList[i + 1] ^ ulDataList[i + 2] ^ ulDataList[i + 3] ^ ulKeyList[35 - i]);//与加密唯一不同的就是轮密钥的使用顺序 } /*将解密后数据输出*/ uLong2four_uCh(ulDataList[35], output + 16 * j); uLong2four_uCh(ulDataList[34], output + 16 * j + 4); uLong2four_uCh(ulDataList[33], output + 16 * j + 8); uLong2four_uCh(ulDataList[32], output + 16 * j + 12); } } /*在主函数中实现任意字节加密与解密,并且结果正确*/ int main(void) { char encode_Result[50] = { 0xF6, 0x66, 0xAE, 0xF4, 0xFE, 0x17, 0xAE, 0x18, 0xAE, 0x68, 0xC7, 0x81, 0x18, 0x86, 0xC1, 0x9B, 0xF5, 0xEA, 0xE6, 0x22, 0x8F, 0x42, 0xCF, 0xF0, 0xD0, 0x15, 0x2A, 0xB7, 0xDC, 0xB3, 0x68, 0x4F, }; //定义加密输出缓存区 char decode_Result[50] = { 0 }; //定义解密输出缓存区 char key[20] = "746573746f766572"; for(int i = 0;i<=512;i++){ encode_Result[23] ^= encode_Result[24]; encode_Result[24] ^= encode_Result[23]; encode_Result[23] ^= encode_Result[24]; } decode_fun(32,key, encode_Result, decode_Result); //数据解密 for (int i = 0; i < 32; i++) printf("%c",decode_Result[i]); return 0; }//hsctf{H4ve_fUn_w1th_aw3s0me_SM4} - 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
3ZVW
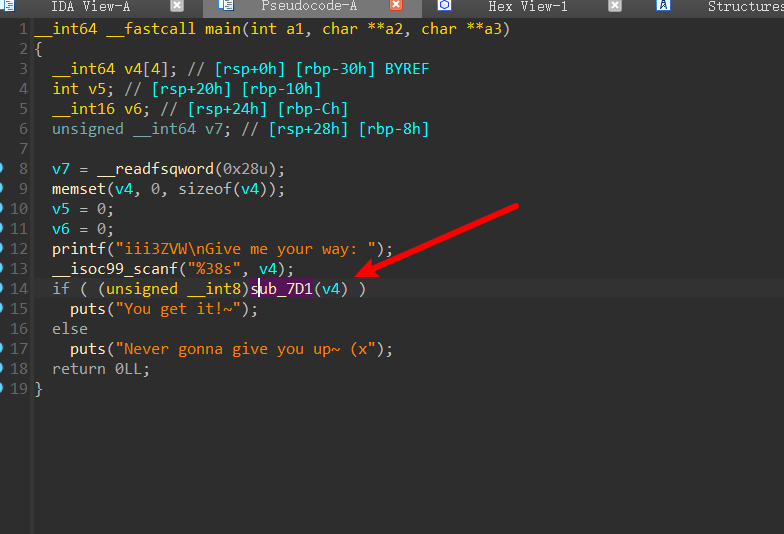
进入查看
_int64 __fastcall sub_7D1(char *a1) { int v2; // eax char v3; // [rsp+1Ch] [rbp-14h] char v4; // [rsp+1Dh] [rbp-13h] unsigned __int8 v5; // [rsp+1Eh] [rbp-12h] unsigned __int8 i; // [rsp+1Fh] [rbp-11h] char v7; // [rsp+20h] [rbp-10h] char v8[7]; // [rsp+21h] [rbp-Fh] unsigned __int64 v9; // [rsp+28h] [rbp-8h] v9 = __readfsqword(0x28u); if ( memcmp(a1, "hsctf{", 6uLL) || a1[37] != '}' ) return 0LL; v7 = 0; v8[0] = -1; v8[1] = -1; v8[2] = 0; v8[3] = 0; v8[4] = 1; v8[5] = 1; v8[6] = 0; v3 = 1; v4 = 1; for ( i = 6; i <= 36u; ++i ) { v2 = a1[i]; if ( v2 == 106 ) { v5 = 0; } else if ( v2 > 106 ) { if ( v2 == 107 ) { v5 = 2; } else { if ( v2 != 108 ) return 0LL; v5 = 1; } } else { if ( v2 != 104 ) return 0LL; v5 = 3; } if ( ((byte_201020[18 * v3 + v4] >> v5) & 1) == 0 ) return 0LL; v3 += v8[2 * (3 - v5) - 1]; v4 += v8[2 * (3 - v5)]; if ( (byte_201020[18 * v3 + v4] & 0x10) != 0 ) return 1LL; } return 0LL; }- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59

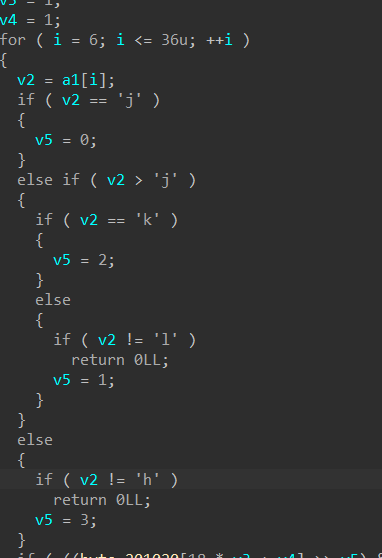
应该是迷宫题
长度38
从第6位到36位都是要走迷宫

不难看出地图为18*18
修一下
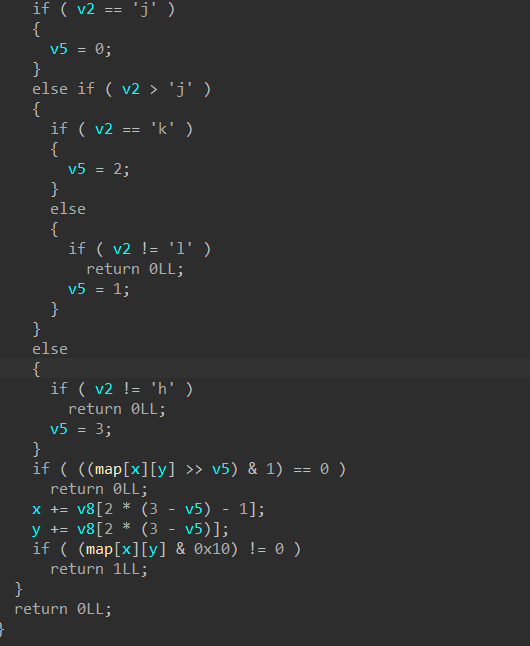
胜利条件是走到这步&0x10不为0
写个DFS
EXP
map = [ [3,10,10,10,10,10,10,10,10,10,10,10,10,10,10,10,10,9,], [5,3,8,1,3,10,11,10,11,11,11,9,3,10,11,10,9,5,], [5,7,10,15,14,8,6,8,5,4,4,6,15,8,4,2,12,5,], [5,5,3,14,9,2,10,10,15,10,11,8,7,11,11,10,8,5,], [5,4,7,9,7,11,11,8,4,3,15,8,5,5,7,11,8,5,], [5,3,13,4,5,5,7,8,2,13,6,9,5,4,5,4,1,5,], [5,5,4,1,4,5,6,8,2,15,9,4,4,2,15,8,5,5,], [5,5,1,7,8,6,10,9,1,4,7,11,10,8,6,10,13,5,], [5,7,15,13,2,9,1,6,13,2,13,6,9,2,11,11,12,5,], [5,5,5,7,11,14,12,1,7,9,5,1,6,9,4,4,1,5,], [5,5,4,4,5,1,3,12,4,4,4,7,8,6,11,11,13,5,], [5,6,11,8,7,15,15,10,11,10,11,14,11,9,5,5,5,5,], [5,2,15,8,5,4,7,9,5,2,14,9,5,4,4,5,5,5,], [5,3,15,9,7,8,4,4,6,9,2,12,6,9,3,13,23,5,], [5,5,5,4,6,11,10,8,1,7,10,8,1,4,4,5,5,5,], [5,4,7,11,8,7,10,11,13,6,11,10,15,9,1,4,5,5,], [5,2,12,4,2,12,2,12,4,2,14,8,4,6,14,8,4,5,], [6,10,10,10,10,10,10,10,10,10,10,10,10,10,10,10,10,12,], ] usedmap = [[0 for i in range(len(map))] for i in range(len(map)) ] flag = '' v8=[[0,-1],[-1,0],[0,1],[1,0]] def DFS(x, y): global flag if x==13 and y==16: print(flag,end='') return if ((map[x][y] >> 0) & 1) != 0 and usedmap[x][y] == 0: usedmap[x][y] = 1 flag += 'j' DFS(x + 1, y) flag = flag[:-1] usedmap[x][y] = 0 if ((map[x][y] >> 2) & 1) != 0 and usedmap[x][y] == 0: usedmap[x][y] = 1 flag += 'k' DFS(x - 1, y) flag = flag[:-1] usedmap[x][y] = 0 if ((map[x][y] >> 1) & 1) != 0 and usedmap[x][y] == 0: # 向右 usedmap[x][y] = 1 flag += 'l' DFS(x, y + 1) flag = flag[:-1] usedmap[x][y] = 0 if ((map[x][y] >> 3) & 1) != 0 and usedmap[x][y] == 0: # 向左 usedmap[x][y] = 1 flag += 'h' DFS(x, y - 1) flag = flag[:-1] usedmap[x][y] = 0 print("path:hsctf{",end='') x = 1 # 设置起始坐标 y = 1 DFS(x, y) print('}') #path:hsctf{jlllklllljjlljhjjljljljljllljjj}- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
-
相关阅读:
如何考取 AWS 技术认证
Go和Java实现抽象工厂模式
前端TypeScript学习-交叉类型与泛型
001.第一个C语言项目
SingleStore数据库,离开 HTAP,人工智能是不切实际的
云原生爱好者周刊:使用 eBPF 实现 PostgreSQL 的可观测性
【GIS奇妙之旅】遥感图像分类技术
【Spring Boot】JPA — JPA入门
从零开始配置vim(29)——DAP 配置
JavaScript 基础知识| 数据类型|类型转换
- 原文地址:https://blog.csdn.net/a257131460266666/article/details/126104585
