-
Strongswan:gcrypt-ikev2/rw-cert测试浅析
实验介绍
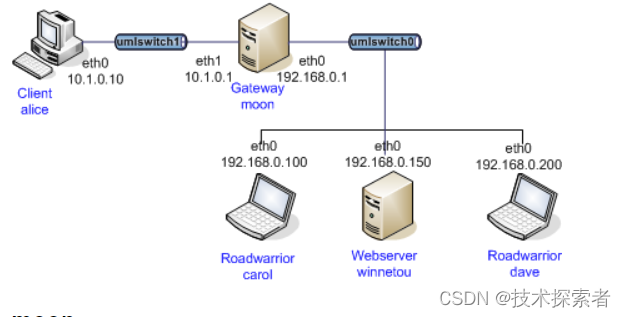
该场景是远程用户(roadwarrior)carol和网关moon使用基于GNU libgcrypt库的加密插件gcrypt,执行加密相关操作。而远程用户dave使用strongswan默认的加密插件:为IKE连接使用加密套件:aes des sha1 sha2 md5 gmp等。远程用户carol和dave建立到网关moon的连接,认证采用X.509证书方式,连接成功建立之后,在主机carol和dave上ping网关moon之后的虚拟主机alice,以验证连通性。
以下启动gcrypt-ikev2/rw-cert测试用例.
注意:在启动之前需要执行start-testing脚本开启测试环境。
$ cd strongswan-5.9.6/testing
$
$ sudo ./do-tests gcrypt-ikev2/rw-cert
Guest kernel : 5.2.11
strongSwan : 5.9.6
Date : 20220621-1053-20[ ok ] 1 gcrypt-ikev2/rw-cert: pre..test..post
Passed : 1
Failed : 0The results are available in /srv/strongswan-testing/testresults/20220621-1053-20
or via the link http://192.168.0.150/testresults/20220621-1053-20Finished : 202206221-1053-36
由以上显示可知:测试用例gcrypt-ikev2/rw-cert的测试结果记录文件保存在以下目录:/srv/strongswan-testing/testresults/20220621-1053-20/gcrypt-ikev2/rw-cert/中,这些文件记录了测试过程中虚拟机carol和dave,以及网关moon的各种状态信息和运行日志。
测试拓扑如下:
配置
moon网关配置
配置文件swanctl.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/moon/etc/swanctl/swanctl.conf注意网关moon的连接配置
- 连接rw(roadwarrior)的proposals使用:aes128-sha256-modp3072,3des-sha1-modp1536,分别对于主机dave和carol的连接proposals配置 。
- 子连接net的esp_proposals使用:caes128-sha256-modp3072,3des-sha1-modp1536,分别对于主机dave和carol的子连接proposals配置。
作为网关,其事先并不知晓连接对端的IP地址信息,此处只有local_addrs的配置。
- connections {
- rw {
- local_addrs = 192.168.0.1
- local {
- auth = pubkey
- certs = moonCert.pem
- id = moon.strongswan.org
- }
- remote {
- auth = pubkey
- }
- children {
- net {
- local_ts = 10.1.0.0/16
- updown = /usr/local/libexec/ipsec/_updown iptables
- esp_proposals = aes128-sha256-modp3072,3des-sha1-modp1536
- }
- }
- version = 2
- proposals = aes128-sha256-modp3072,3des-sha1-modp1536
- }
- }
配置文件strongswan.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/moon/etc/strongswan.conf该配置文件指定要加载的模块,与carol配置相同,这里使用gcrypt插件。(也可以保持默认)
swanctl {
load = pem pkcs1 x509 revocation constraints pubkey openssl random
}charon-systemd {
load = curl test-vectors pem pkcs1 gcrypt nonce x509 revocation hmac xcbc ctr ccm gcm vici kernel-netlink socket-default updown
integrity_test = yes
crypto_test {
on_add = yes
}
}carol配置
配置文件swanctl.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/carol/etc/swanctl/swanctl.conf虚拟主机carol的IP地址为192.168.0.100,而moon网关的IP地址为192.168.0.1。
另,
- 连接home使用proposals:3des-sha1-modp1536
- 子连接home使用esp_proposals:3des-sha1-modp1536
- IKE协议使用version 2
- connections {
- home {
- local_addrs = 192.168.0.100
- remote_addrs = 192.168.0.1
- local {
- auth = pubkey
- certs = carolCert.pem
- id = carol@strongswan.org
- }
- remote {
- auth = pubkey
- id = moon.strongswan.org
- }
- children {
- home {
- remote_ts = 10.1.0.0/16
- updown = /usr/local/libexec/ipsec/_updown iptables
- esp_proposals = 3des-sha1-modp1536
- }
- }
- version = 2
- proposals = 3des-sha1-modp1536
- }
- }
配置文件strongswan.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/carol/etc/strongswan.conf该配置文件指定需要加载的模块,注意这里加载测试的gcrypt插件。
swanctl {
load = pem pkcs1 x509 revocation constraints pubkey openssl random
}charon-systemd {
load = curl test-vectors pem pkcs1 gcrypt nonce x509 revocation hmac xcbc ctr ccm gcm vici kernel-netlink socket-default updown
integrity_test = yes
crypto_test {
on_add = yes
}
}dave配置
配置文件swanctl.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/dave/etc/swanctl/swanctl.conf虚拟主机carol的IP地址为192.168.0.200,而moon网关的IP地址为192.168.0.1。
另,
- 连接home使用proposals:aes128-sha256-modp3072
- 子连接home使用esp_proposals:aes128-sha256-modp3072
- IKE协议使用version 2
- connections {
- home {
- local_addrs = 192.168.0.200
- remote_addrs = 192.168.0.1
- local {
- auth = pubkey
- certs = daveCert.pem
- id = dave@strongswan.org
- }
- remote {
- auth = pubkey
- id = moon.strongswan.org
- }
- children {
- home {
- remote_ts = 10.1.0.0/16
- updown = /usr/local/libexec/ipsec/_updown iptables
- esp_proposals = aes128-sha256-modp3072
- }
- }
- version = 2
- proposals = aes128-sha256-modp3072
- }
- }
配置文件strongswan.conf
strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/hosts/dave/etc/strongswan.conf该配置文件指定需要加载的模块,与carol的配置不同,这里不使用gcrypt插件,而是加载strongswan默认的aes des sha1 sha2等插件。
swanctl {
load = pem pkcs1 x509 revocation constraints pubkey openssl random
}charon-systemd {
load = test-vectors aes des sha1 sha2 md5 pem pkcs1 gmp random nonce x509 curl revocation hmac xcbc ctr ccm vici stroke kernel-netlink socket-default updown
integrity_test = yes
crypto_test {
required = yes
on_add = yes
}
}准备
配置文件:strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/pretest.dat,内容参考如下。
在预测试pre-test阶段:
- 备份moon和carol,dave主机的iptables配置。
- 启动strongswan。
- 使用脚本expect-connection检测名称为net的连接(carol和dave主机上为home)是否建 立,超过5秒钟检测不到,打印失败信息。
- 在主机carol和dave上swanctl初始化一个名称为home的子连接。
通过之前的介绍已经在carol,dave和moon虚拟主机的配置文件(etc/swanctl/swanctl.conf)中看到了home和net的配置信息。
moon::iptables-restore < /etc/iptables.rules
carol::iptables-restore < /etc/iptables.rules
dave::iptables-restore < /etc/iptables.rules
moon::systemctl start strongswan
carol::systemctl start strongswan
dave::systemctl start strongswan
moon::expect-connection net
carol::expect-connection home
carol::swanctl --initiate --child home 2> /dev/null
dave::expect-connection home
dave::swanctl --initiate --child home 2> /dev/null测试
配置文件:strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/evaltest.dat,内容如下。
在第一,二行中,SSH登录到carol/dave主机执行ping命令,目的IP为alice主机的地址,检查alice返回的信息。
carol::ping -c 1 PH_IP_ALICE::64 bytes from PH_IP_ALICE: icmp_.eq=1::YES
dave:: ping -c 1 PH_IP_ALICE::64 bytes from PH_IP_ALICE: icmp_.eq=1::YES
carol::swanctl --list-sas --raw 2> /dev/null::home.*version=2 state=ESTABLISHED local-host=192.168.0.100 local-port=4500 local-id=carol@strongswan.org remote-host=192.168.0.1 remote-port=4500 remote-id=moon.strongswan.org initiator=yes.*encr-alg=3DES_CBC integ-alg=HMAC_SHA1_96 prf-alg=PRF_HMAC_SHA1 dh-group=MODP_1536.*child-sas.*home.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=3DES_CBC integ-alg=HMAC_SHA1_96.*local-ts=\[192.168.0.100/32] remote-ts=\[10.1.0.0/16]::YES
dave:: swanctl --list-sas --raw 2> /dev/null::home.*version=2 state=ESTABLISHED local-host=192.168.0.200 local-port=4500 local-id=dave@strongswan.org remote-host=192.168.0.1 remote-port=4500 remote-id=moon.strongswan.org initiator=yes.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=MODP_3072.*child-sas.*home.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128.*local-ts=\[192.168.0.200/32] remote-ts=\[10.1.0.0/16]::YES
moon:: swanctl --list-sas --ike-id 1 --raw 2> /dev/null::rw.*version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=4500 local-id=moon.strongswan.org remote-host=192.168.0.100 remote-port=4500 remote-id=carol@strongswan.org.*encr-alg=3DES_CBC integ-alg=HMAC_SHA1_96 prf-alg=PRF_HMAC_SHA1 dh-group=MODP_1536.*child-sas.*net.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=3DES_CBC integ-alg=HMAC_SHA1_96.*local-ts=\[10.1.0.0/16] remote-ts=\[192.168.0.100/32]::YES
moon:: swanctl --list-sas --ike-id 2 --raw 2> /dev/null::rw.*version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=4500 local-id=moon.strongswan.org remote-host=192.168.0.200 remote-port=4500 remote-id=dave@strongswan.org.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=MODP_3072.*child-sas.*net.*state=INSTALLED mode=TUNNEL protocol=ESP.*encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128.*local-ts=\[10.1.0.0/16] remote-ts=\[192.168.0.200/32]::YES
moon::tcpdump::IP carol.strongswan.org > moon.strongswan.org: ESP::YES
moon::tcpdump::IP moon.strongswan.org > carol.strongswan.org: ESP::YES
moon::tcpdump::IP dave.strongswan.org > moon.strongswan.org: ESP::YES
moon::tcpdump::IP moon.strongswan.org > dave.strongswan.org: ESP::YES第三行测试语句在carol主机上执行命令 swanctl --list-sas --raw,检查输出结果是否与指定内容匹配。以下为swanctl的执行结构,可见两者完全匹配。
home: #1, ESTABLISHED, IKEv2, 66bd06168e658b7a_i* 221eec35659acbb3_r
local 'carol@strongswan.org' @ 192.168.0.100[4500]
remote 'moon.strongswan.org' @ 192.168.0.1[4500]
3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
established 7s ago, rekeying in 12967s
home: #1, reqid 1, INSTALLED, TUNNEL, ESP:3DES_CBC/HMAC_SHA1_96
installed 7s ago, rekeying in 3448s, expires in 3953s
in c504c668, 84 bytes, 1 packets, 1s ago
out cd086628, 84 bytes, 1 packets, 1s ago
local 192.168.0.100/32
remote 10.1.0.0/16第四行测试语句在dave主机上执行命令 swanctl --list-sas --raw,检查输出结果是否与指定内容匹配。以下为swanctl的执行结构,可见两者完全匹配。
home: #1, ESTABLISHED, IKEv2, 89a722d0fd880266_i* 0102abcab287ac44_r
local 'dave@strongswan.org' @ 192.168.0.200[4500]
remote 'moon.strongswan.org' @ 192.168.0.1[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_3072
established 2s ago, rekeying in 13626s
home: #1, reqid 1, INSTALLED, TUNNEL, ESP:AES_CBC-128/HMAC_SHA2_256_128
installed 2s ago, rekeying in 3257s, expires in 3958s
in ccc0b755, 84 bytes, 1 packets, 2s ago
out c4eff1c9, 84 bytes, 1 packets, 2s ago
local 192.168.0.200/32
remote 10.1.0.0/16第五行测试语句在moon网关上执行命令 swanctl --list-sas --ike-id 1 --raw,这里指定了ike-id参数为1,由于在测试过程中,carol主机首先发起了连接请求,此处匹配的为carol的连接。检查输出结果是否与指定内容匹配。以下为swanctl的执行结构,可见两者完全匹配。
rw: #1, ESTABLISHED, IKEv2, 66bd06168e658b7a_i 221eec35659acbb3_r*
local 'moon.strongswan.org' @ 192.168.0.1[4500]
remote 'carol@strongswan.org' @ 192.168.0.100[4500]
3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
established 7s ago, rekeying in 14077s
net: #1, reqid 1, INSTALLED, TUNNEL, ESP:3DES_CBC/HMAC_SHA1_96
installed 7s ago, rekeying in 3409s, expires in 3953s
in cd086628, 84 bytes, 1 packets, 1s ago
out c504c668, 84 bytes, 1 packets, 1s ago
local 10.1.0.0/16
remote 192.168.0.100/32第六行测试语句在moon网关上执行命令 swanctl --list-sas --ike-id 2 --raw,这里指定了ike-id参数为2,由于在测试过程中,dave主机在carol之后发起连接请求,此处匹配的为dave的连接。检查输出结果是否与指定内容匹配。以下为swanctl的执行结构,可见两者完全匹配。
rw: #2, ESTABLISHED, IKEv2, 89a722d0fd880266_i 0102abcab287ac44_r*
local 'moon.strongswan.org' @ 192.168.0.1[4500]
remote 'dave@strongswan.org' @ 192.168.0.200[4500]
AES_CBC-128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_3072
established 1s ago, rekeying in 13301s
net: #2, reqid 2, INSTALLED, TUNNEL, ESP:AES_CBC-128/HMAC_SHA2_256_128
installed 1s ago, rekeying in 3318s, expires in 3959s
in c4eff1c9, 84 bytes, 1 packets, 1s ago
out ccc0b755, 84 bytes, 1 packets, 1s ago
local 10.1.0.0/16
remote 192.168.0.200/32最后4行测试语句都是在moon网关上执行的,这里的tcpdump命令并不执行,而是检查在以上的测试过程中后台tcpdump名称输出到文件/tmp/tcpdump.log中的日志信息,确认carol与alice,以及dave和alice之间的ESP加密的ping报文是否正常。
12:53:50.633829 IP moon.strongswan.org > carol.strongswan.org: ESP(spi=0xc504c668,seq=0x1), length 116
12:53:50.687277 IP dave.strongswan.org > moon.strongswan.org: ESP(spi=0xc4eff1c9,seq=0x1), length 136
12:53:50.687362 IP dave.strongswan.org > alice.strongswan.org: ICMP echo request, id 6242, seq 1, length 64
12:53:50.687634 IP moon.strongswan.org > dave.strongswan.org: ESP(spi=0xccc0b755,seq=0x1), length 136收尾
配置文件:strongswan-5.9.6/testing/tests/gcrypt-ikev2/rw-cert/posttest.dat,内容如下。停止carol和dave主机上的ike连接home。终止carol,dave和moon上的StrongSwan进程。恢复moon和carol,dave主机上的iptables规则配置。
carol::swanctl --terminate --ike home
dave::swanctl --terminate --ike home
carol::systemctl stop strongswan
dave::systemctl stop strongswan
moon::systemctl stop strongswan
moon::iptables-restore < /etc/iptables.flush
carol::iptables-restore < /etc/iptables.flush
dave::iptables-restore < /etc/iptables.flush测试结果文件默认都保存在目录:/srv/strongswan-testing/testresults/20220621-1053-20/gcrypt-ikev2/rw-cert下。
其中,
- 文件console.log 记录了整个的测试过程。
- 文件carol.daemon.log,dave.daemon.log和moon.daemon.log文件记录了charon-systemd主进程的日志。
完整的测试结果文件里边见本文开始部分。
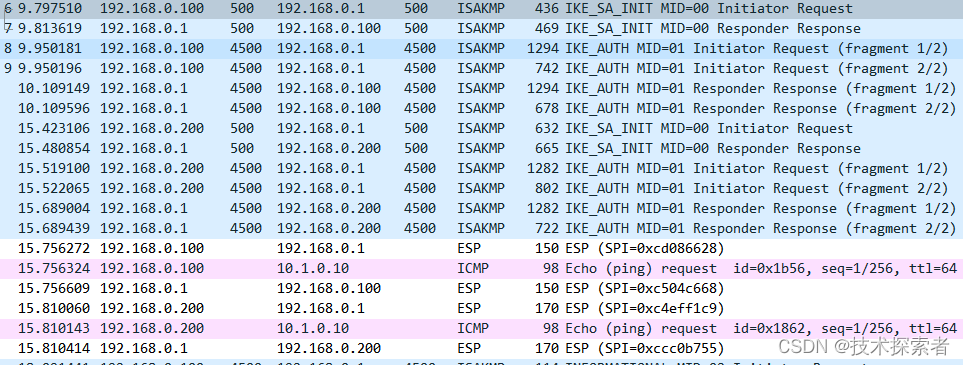
下图为IKEv2报文的交互报文:
-
相关阅读:
centos7.9 扩容swap分区
【Leetcode刷题Python】337. 打家劫舍 III
【语音去噪】基于切比雪夫+椭圆形低通滤波器语音去噪附GUI界面
踩坑,发现一个ShardingJdbc读写分离的BUG
泛型知识汇总
汽车电子专业知识篇(六十四)-车载毫米波雷达基本概念
JavaSE - 逻辑控制语句
从零到一落地接口自动化测试
https下载图片
【Java面试】Kafka 怎么避免重复消费
- 原文地址:https://blog.csdn.net/hhd1988/article/details/125406115