-
华为USG6000防火墙nat / nat server 配置(多出口情况)
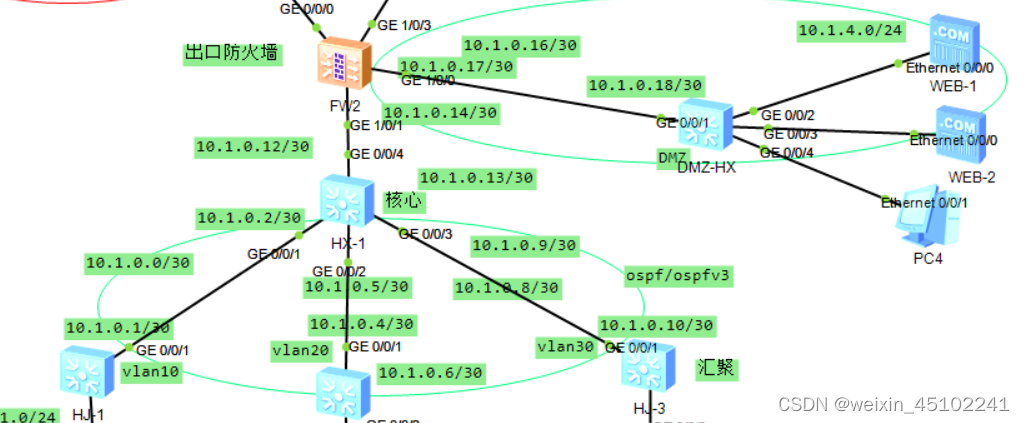
基本配置:
- 防火墙usg6000的g0/0/0口默认是管理口,配置的地址不加入路由表,如要加入路由表,则把该接口下的ip binding vpn-instance default删除
- 配置防火墙安全策略:
[FW1] security-policy // 配置安全策略
[FW1-policy-security] rule name lyshark // 规则名称
[FW1-policy-security-rule-lyshark] source-zone trust // 原安全区域(内部)
[FW1-policy-security-rule-lyshark] destination-zone untrust // 目标安全区域(外部)
[FW1-policy-security-rule-lyshark] source-address any // 原地址区域
[FW1-policy-security-rule-lyshark] destination-address any // 目标地址区域
[FW1-policy-security-rule-lyshark] service any // 放行所有服务
[FW1-policy-security-rule-lyshark] action permit // 放行配置
[FW1-policy-security-rule-lyshark] quit
使防火墙交换机能够互ping:
security-policy
rule name 1
source-zone local //如需防火墙ping别的设备需要配置local区域的安全策略,因为防火墙接口的区域都是local
destination-zone trust service protocol icmp //从local区域放通到trust区域,放通icmp协议,local区域为防火墙本身所有接口
action permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.0.14 255.255.255.252
service-manage ping permit //防火墙接口放通ping包,也可以放通http、ssh、telnet等
配置内外网接口:
[FW1] interface GigabitEthernet 1/0/2 // 选择外网接口
[FW1-GigabitEthernet1/0/2] undo shutdown // 开启外网接口
[FW1-GigabitEthernet1/0/2] ip address 10.10.10.10 255.255.255.0 // 配置IP地址
[FW1-GigabitEthernet1/0/2] gateway 10.10.10.20 // 配置网关
[FW1-GigabitEthernet1/0/2] undo service-manage enable
[FW1-GigabitEthernet1/0/2] quit
[FW1] firewall zone untrust // 选择外网区域
[FW1-zone-untrust] add interface GigabitEthernet 1/0/2 // 将接口加入到此区域
# -------------------------------------------------------
system-view [FW1] interface GigabitEthernet 1/0/0
[FW1-GigabitEthernet1/0/0] ip address 192.168.1.1 255.255.255.0
[FW1-GigabitEthernet1/0/0] undo shutdown
[FW1-GigabitEthernet1/0/0] quit
[FW1] firewall zone trust // 将接口加入trust区域
[FW1-zone-trust] add interface GigabitEthernet 1/0/0
nat映射:
- 相同区域不同出口配置nat server的情况:
[USG6000V1]nat server 1 zone untrust protocol tcp global 59.79.100.101 www inside 10.1.4.1 www no-reverse //no-reverse代表可以配置多个映射表项,但只有单向映射,只能外部网络单向发起连接
[USG6000V1]nat server 2 zone untrust protocol tcp global 202.96.100.101 www inside 10.1.4. 1 www no-reverse //设置第二个出口的映射
- 多出口的情况通过设置多个区域的方式即可配置多条nat server
- 建立安全区域:
[USG6000V1]firewall zonenamedianxin
[USG6000V1-zone-dianxin]set priority 5 //设置区域优先级
[USG6000V1-zone-dianxin]add interface g1/0/1
[USG6000V1]firewall zonenameliantong
[USG6000V1-zone-liantong]set priority2
[USG6000V1-zone-liantong]add interface g1/0/2
- 别忘了汇聚或核心交换机设置默认或静态路由!!!!!
- 地址池,内网访问外部网络:
nat address-group cernet //地址池
mode pat //可以一对多
section 0 59.79.100.100 //地址池的地址 多个出口,设置多个地址池,设置nat策略
根据不同的目的网段映射不同的地址池:
nat-policy
rule name dianxin
source-zone trust
destination-zone untrust
destination-address 202.96.200.0 mask 255.255.255.0
action source-nat address-group dianxin
rule name cernet
source-zone trust
destination-zone untrust
destination-address 59.79.200.0 mask 255.255.255.0
action source-nat address-group cernet
-
相关阅读:
Java语言高级-03常用API第二部分-第1节Object类
【soloπ】adb连接单个多个手机
微积分在金融投资的应用
算法进修Day-32
PMP考试提分必刷题
LeetCode977. 有序数组的平方
基于美洲狮优化算法(Puma Optimizar Algorithm ,POA)的无人机三维路径规划(提供MATLAB代码)
Empire(三)域内渗透
操作系统学习笔记12 | 从生磁盘到文件
[apue] linux 文件系统那些事儿
- 原文地址:https://blog.csdn.net/weixin_45102241/article/details/132654531