-
深入理解RBAC
RBAC是一种基于角色实现访问控制的权限管理机制,通过定义角色和权限、用户和角色、角色和角色之间的关系,实现多层次、细粒度、可复用的权限管理系统。原文: Role-based Access Control (RBAC) Model[1]

Bernard Hermant@Unsplash
Avery Pennarun写的"RBAC like it was meant to be[2]非常值得一读。
在web或移动应用中,访问权限控制机制是保证系统安全[3]的重要手段,其中最常见的就是基于角色的访问控制(RBAC, Role-based Access Control)。
基于角色的访问控制是传统访问控制(自主访问[4]、强制访问[5])的一种有前途的替代方案。在RBAC模式下,权限与角色相关联,从而大大简化了对权限的管理。组织为了完成各种任务,从而创建了角色,用户根据职责和技能被分配到相应的角色,也可以从一个角色分配到另一个角色。新角色可以根据新需求和系统集成赋予新的权限,也可以从角色中撤回权限。可以建立角色-角色关系来包含更广泛的客观情况。

图片来源: https://www.dnsstuff.com/rbac-vs-abac-access-control 访问控制模型
-
访问控制列表(ACL, Access Control List) [6] -
自主访问控制(DAC, Discretionary Access Control) [7] -
强制访问控制(MAC, Mandatory Access Control) [8] -
基于角色的访问控制(RBAC, Role-Based Access Control) [9] -
基于属性的访问控制(ABAC, Attribute-based Access Control) [10] -
基于历史的访问控制(HBAC, History-based Access Control) [11] -
基于身份的访问控制(IBAC, Identity-based Access Control) [12] -
基于组织的访问控制(OrBAC, Organization-based Access Control) [13] -
基于网格的访问控制(LBAC, Lattice-based access control) [14] -
基于上下文的访问控制(CBAC, Context-based Access Control) [15] -
基于实体关系的访问控制(ReBAC, Entity-Relationship-based Access Control) [16] -
扩展基于角色的访问控制(Extended Role-Based Access Control) [17] -
语义访问控制(SAC, Semantic Access Control) [18]
什么是RBAC?
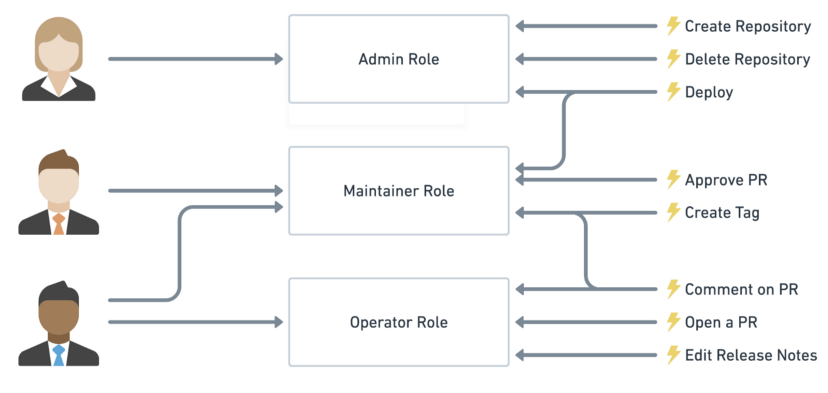
图片来源: https://www.quora.com/What-does-the-role-based-access-control-model-mean-in-workforce-management -
通过分配一组与角色关联的权限来提供高级访问 -
支持公认的安全原则: 最小特权原则、责任分离原则和数据抽象原则 -
最小权限原则(The principle of least privilege) — 限制与角色关联的权限的数量和大小 -
职责分离原则(The principle of separation of responsibilities) — 在完成重要任务的过程中,分配一个以上相互约束的角色 -
数据抽象原则(The principle of data abstraction) — 对不同用户的操作提供不同权限的清晰分离 -
不同类型用户可以根据其工作职能和职责获得不同类型的访问权限来履行其职责 -
低级操作人员(例如运维人员)只能查看本部门记录,高级操作人员(例如经理)可以查看和编辑本部门记录
概念
角色(Roles)
-
由许多标准定义,包括权限、职责、成本中心以及业务操作流程。 -
无法通过身份确定角色,权限与角色绑定。 -
角色是围绕访问管理组织的,无论是什么样的活动、身份、职能等,角色可能都不变。
权限(Permissions)
-
权限是一组资源的集合,用户需要批准权限才能使用一组资源对受保护对象执行操作。 -
操作功能模块(添加、删除、更新、编辑、查看、上传),进入菜单,一键进入页面 -
在某些系统设计中,功能操作可以被视为文件、类别、菜单、页面元素、模块、数据、字段等。
User -> Role -> Permissions -> resources
RBAC模型
NIST RBAC96模型是由美国国家标准与技术研究院[19]开发的标准化RBAC定义。
4个基本概念模型:
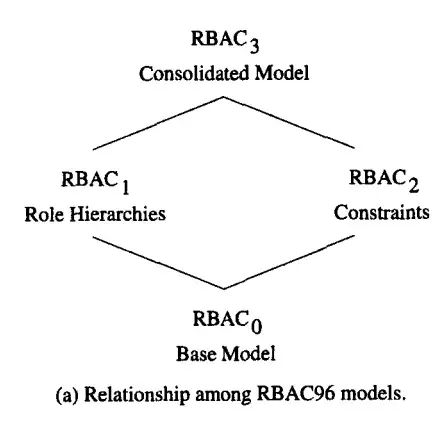
图片来源: https://transang.me/pattern-oriented-software-architecture-access-control-pattern -
RBACO — 核心RBAC -
RBAC1 — 层次RBAC (RBAC0 + 角色层次结构) -
RBAC2 — 约束RBAC (RBAC0 + 约束) -
RBAC3 — 组合RBAC (RBAC1 + RBAC2)
RBAC授权的过程可以抽象为:
-
谁(Who) — 权限的用户或角色 -
什么(What) — 资源 -
如何(How) — 具体的权限
RBAC0
-
3个元素: 用户、角色和权限 -
设计基于"[多对多(many-to-many)](https://en.wikipedia.org/wiki/Many-to-many_(data_model "多对多(many-to-many "多对多(many-to-many)")"))"关系,即多个用户可以拥有相同的角色,一个用户可以拥有多个角色。
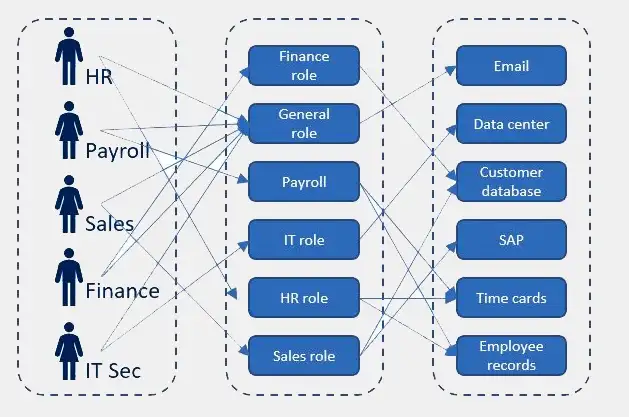
图片来源: https://www.bettercloud.com/monitor/the-fundamentals-of-role-based-access-control RBAC1
-
4个元素: 用户、角色、权限、层次结构/继承 -
定义了不同角色之间的从属关系 -
高级别角色可以自动从低级别角色获取权限 -
角色之间的继承关系可以分为一般继承关系和有限继承关系 -
一般继承关系只要求角色继承关系是绝对的偏序关系( 角色之间的多重继承) -
有限继承关系要求角色继承关系是树状结构( 角色之间的单一继承)
StackOverflow的Q/A帖子"如何设计基于角色的分层访问控制系统[20]"是一个很好的例子,值得一读。
-
树(Tree) — (自底向上的层次结构) — 树底部的元素被授予更大的权限。 -
倒立树(Inverted Tree) — (自顶向下的层次结构) — 高级角色将其部分权限继承给低级角色,同一级别的节点不共享权限。
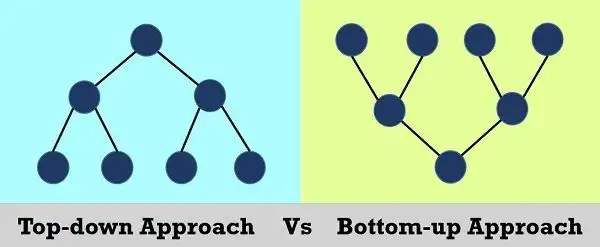
图片来源: https://techdifferences.com/difference-between-top-down-and-bottom-up-approach.html -
网格(Grid) — (自底向上和自顶向下的组合) — 每个角色都可以从它下面和上面的节点继承权限,因此相对灵活,可以共享权限。顶级节点被授予更大的权限。
图片来源: http://grid-layout.com/grid-lines.html RBAC2
-
4个元素: 用户、角色、权限和约束 -
由于存在利益冲突策略,角色之间的关系存在约束
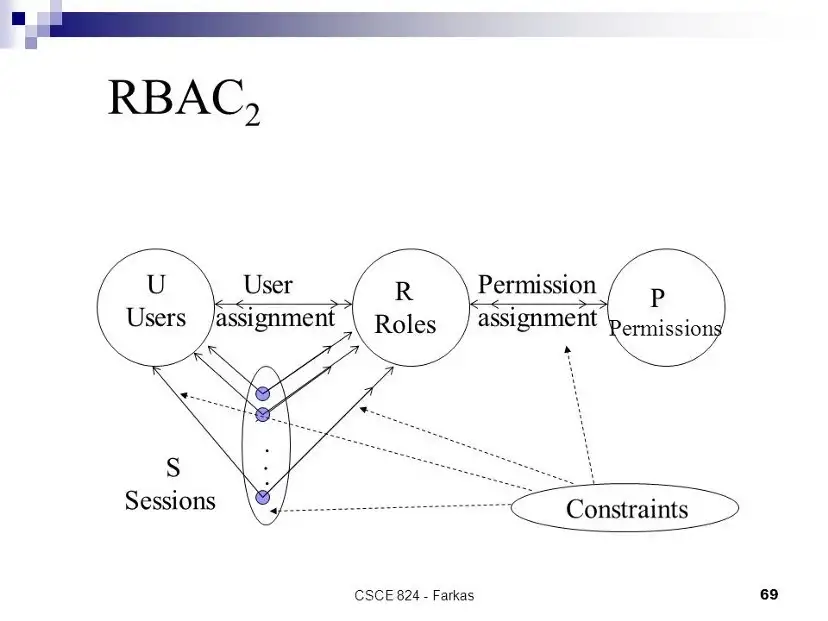
图片来源: https://slideplayer.com/user/10879796 RBAC3
-
将RBAC1和RBAC2的所有特征(角色继承和约束关系)集成到模型中。 -
可以根据不同的上下文限制或激活可用的用户权限,当用户在会话期间执行的任务可能需要不同级别的访问时,可以在会话期间激活更高级别的权限。
类图
-
User表(用户ID、用户名和其他属性) -
Role表(角色ID,角色名,角色类型) -
User_Role表(用户角色关联表) -
Product表(产品ID,产品类型,渠道,费用,地区) -
Region表(地区代码、渠道) -
Permission表(权限ID、权限类型、权限名称和其他属性) -
Role_permission表(角色权限关联表) -
Menu表(菜单ID,菜单名称,菜单路径URL,父菜单ID,资源和其他属性) -
Page_element表(资源、页面元素ID、页面元素代码和其他属性) -
File表(文件ID,文件名,文件路径) -
Permission_Menu表(权限ID,菜单ID) -
Permission_Element表(权限ID,页面元素ID) -
Permission_File表(权限ID,文件ID) -
Operation表(动作ID、动作名称、动作代码等属性) -
Permission_Operation表(权限ID,操作ID)
RBAC模型的优点
-
降低授权管理的复杂性 -
降低管理成本 -
创建系统级的、可复用的权限分配 -
减少分配用户权限时出错的可能性 -
支持企业安全策略
RBAC模型的缺点
-
不提供操作顺序控制机制
参考文献
History-based access control[21]
Pattern-Oriented Software Architecture - Access control pattern[22]
Role-Based Access Control | CSRC[23]
Role-Based Access Control - Wikipedia[24]
What is Role-Based Access Control (RBAC)? Example, Benefits, and More[25]
What is Role-Based Access Control | RBAC vs ACL vs ABAC | Imperva[26]
Using RBAC Authorization[27]
What is Azure role-based access control (Azure RBAC)?[28]
Role-Based Access Control[29]
RBAC vs ABAC: Make the Right Call | OneLogin[30]
Understanding Role-Based Access Control (RBAC) | StrongDM[31]
What is Role-Based Access Control (RBAC)?[32]
What is Role-Based Access Control (RBAC)?[33]
Role-Based Access Control (RBAC) User Guide | Chronicle Security | Google Cloud[34]
What is Role-Based Access Control (RBAC)? A Complete Guide | Frontegg[35]
Role-Based Access Control (RBAC): What is it and why use it? | Harness[36]
What is Role-Based Access Control (RBAC)? | Tools4ever[37]
你好,我是俞凡,在Motorola做过研发,现在在Mavenir做技术工作,对通信、网络、后端架构、云原生、DevOps、CICD、区块链、AI等技术始终保持着浓厚的兴趣,平时喜欢阅读、思考,相信持续学习、终身成长,欢迎一起交流学习。
微信公众号:DeepNoMind参考资料
[1] - END -Role-based Access Control (RBAC) Model: https://medium.com/geekculture/role-based-access-control-rbac-model-7d8e7b7350d2
[2]RBAC like it was meant to be: https://tailscale.com/blog/rbac-like-it-was-meant-to-be
[3]系统安全: https://twitter.com/jinlow_blogger/status/1580022558396936192
[4]自主访问: https://en.wikipedia.org/wiki/Discretionary_access_control
[5]强制访问: https://en.wikipedia.org/wiki/Mandatory_access_control
[6]Access Control List: https://en.wikipedia.org/wiki/Access-control_list
[7]Discretionary Access Control: https://en.wikipedia.org/wiki/Discretionary_access_control
[8]Mandatory Access Control: https://en.wikipedia.org/wiki/Mandatory_access_control
[9]Role-Based Access Control: https://en.wikipedia.org/wiki/Role-based_access_control
[10]Attribute-based Access Control: https://en.wikipedia.org/wiki/Attribute-based_access_control
[11]History-based Access Control: https://en.everybodywiki.com/History-based_access_control
[12]Identity-based Access Control: https://en.wikipedia.org/wiki/Identity-based_security
[13]Organization-based Access Control: https://en.wikipedia.org/wiki/Organisation-based_access_control
[14]Lattice-based access control: https://www.ibm.com/docs/en/db2/11.5?topic=security-label-based-access-control-lbac
[15]Context-based Access Control: https://en.wikipedia.org/wiki/Context-based_access_control
[16]Entity-Relationship-based Access Control: https://www.scaledaccess.com/whitepapers/the-developers-guide-to-relationship-based-access-control/#:~:text=Relationship%2Dbased%20access%20control%20is,specific%20relationships%20the%20subject%20has.
[17]Extended Role-Based Access Control: https://ucm.riskmanager.modulo.com/manual/en/default.htm#!Documents/extendedrolebasedaccesscontrolmodel.htm
[18]Semantic Access Control: https://en.wikipedia.org/wiki/Semantic_security
[19]美国国家标准与技术研究院: https://www.nist.gov
[20]如何设计基于角色的分层访问控制系统: https://stackoverflow.com/questions/16139712/how-to-design-a-hierarchical-role-based-access-control-system
[21]History-based access control: https://en.everybodywiki.com/History-based_access_control
[22]Pattern-Oriented Software Architecture - Access control pattern: https://transang.me/pattern-oriented-software-architecture-access-control-pattern/
[23]Role-Based Access Control | CSRC: https://csrc.nist.gov/projects/role-based-access-control
[24]Role-Based Access Control - Wikipedia: https://en.wikipedia.org/wiki/Role-based_access_control
[25]What is Role-Based Access Control (RBAC)? Example, Benefits, and More: https://digitalguardian.com/blog/what-role-based-access-control-rbac-examples-benefits-and-more
[26]What is Role-Based Access Control | RBAC vs ACL vs ABAC | Imperva: https://www.imperva.com/learn/data-security/role-based-access-control-rbac
[27]Using RBAC Authorization: https://kubernetes.io/docs/reference/access-authn-authz/rbac
[28]What is Azure role-based access control (Azure RBAC)?: https://learn.microsoft.com/en-us/azure/role-based-access-control/overview
[29]Role-Based Access Control: https://auth0.com/docs/manage-users/access-control/rbac
[30]RBAC vs ABAC: Make the Right Call | OneLogin: https://www.onelogin.com/learn/rbac-vs-abac
[31]Understanding Role-Based Access Control (RBAC) | StrongDM: https://www.strongdm.com/rbac
[32]What is Role-Based Access Control (RBAC)?: https://www.varonis.com/blog/role-based-access-control
[33]What is Role-Based Access Control (RBAC)?: https://www.okta.com/identity-101/what-is-role-based-access-control-rbac
[34]Role-Based Access Control (RBAC) User Guide | Chronicle Security | Google Cloud: https://cloud.google.com/chronicle/docs/administration/rbac
[35]What is Role-Based Access Control (RBAC)? A Complete Guide | Frontegg: https://frontegg.com/guides/rbac
[36]Role-Based Access Control (RBAC): What is it and why use it? | Harness: https://harness.io/blog/rbac
[37]What is Role-Based Access Control (RBAC)? | Tools4ever: https://www.tools4ever.com/glossary/what-is-role-based-access-control
本文由 mdnice 多平台发布
-
-
相关阅读:
sketch for Mac快捷键大全
linux(centOs7)部署mysql(8.0.20)数据库
不了解无线调制方式?这几个“老古董”大家现在还在用!
vue 02
cesium加载倾斜影像数据(模拟雨、雪、雾、无人机飞行、测距、箭头标绘、电子围栏等)
STM32 PWM波频率、占空比以及死区计算详细讲解
每天一个数据分析题(三百九十七)- 逻辑回归
笔记 | 非素数个数(朴素筛查 || 埃式筛查法)
Leetcode168. Excel表列名称
Java - SpringBoot整合Shiro之缓存功能
- 原文地址:https://blog.csdn.net/yuff100/article/details/133744474