-
加速乐源码(golang版本)
一、分析
分析过程网上有很多,这里只说个大概,主要是提供golang源码
- 请求网站,发现前两次请求都会返回521,第三次请求成功,说明前两次请求肯定是干了什么事情;使用接口请求工具模拟请求分析该过程

- 使用postman工具请求
a. 第一次请求会在响应头返回jsluid,返回内容中拼接一个jsl_clearance值
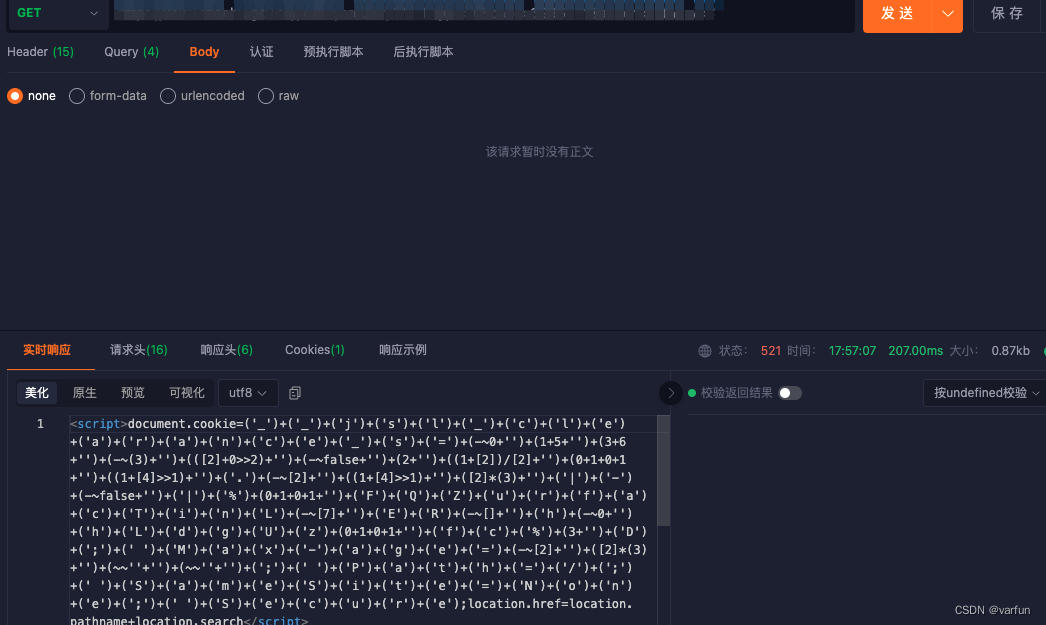
b. 从浏览器的第二次请求得知,需要拿上第一次返回的这两个值,这个时候浏览器会返回一段js代码,这段代码才是真正的设置cookie。

二、调试
像这种网站,我们可以使用hook cookie的方式来调试这段代码,然后找到最终加密的方式然后导出来。
// ==UserScript== // @name Hook Cookie // @namespace http://tampermonkey.net/ // @version 0.1 // @description try to take over the world! // @author You // @include * // @grant none // @run-at document-start // ==/UserScript== // ==UserScript== // @name 获取 cookie 设置的地方 hook // @namespace http://tampermonkey.net/ // @version 0.1 // @description try to take over the world! // @author You // @match https://www.python-spider.com/challenge/2 // @include https://www.python-spider.com/ // @icon https://www.google.com/s2/favicons?sz=64&domain=python-spider.com // @grant none // @run-at document-start // ==/UserScript== alert('hook success') var cookieTemp = ""; Object.defineProperty(document, 'cookie', { set: function(val) { console.log('Hook捕获到cookie设置->', val); debugger; cookieTemp = val; return val; }, get: function() { return cookieTemp; } })- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
三、源码
package main import ( "crypto/md5" "crypto/sha1" "crypto/sha256" "encoding/hex" "encoding/json" "fmt" "io/ioutil" "net/http" "regexp" "github.com/robertkrimen/otto" "github.com/pkg/errors" ) func main() { // 创建http客户端 baseUrl := "这里换成你自己网站的url" method := "GET" cookie, jsLuidCookie, _ := getFirstCookie(baseUrl, method) realCookie, _ := getRealCookie(method, baseUrl, cookie) result := fmt.Sprintf("%s;%s", jsLuidCookie, realCookie) fmt.Println(result) } // getFirstCookie 第一次请求网站,获取第一次cookie;返回第二次请求需要的cookie以及jsluid-Cookie func getFirstCookie(baseUrl, method string) (cookie string, cookie2 string, err error) { // 创建请求 req, err := http.NewRequest(method, baseUrl, nil) if err != nil { return "", "", errors.WithStack(err) } // 这里会验证user-agent,必须与获取cookie保持一致 req.Header.Add("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7") req.Header.Add("Accept-Language", "zh-CN,zh;q=0.9,en;q=0.8") req.Header.Add("User-Agent", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36") req.Header.Add("Accept-Encoding", "deflate, gzip") // 发送请求 resp, err := http.DefaultClient.Do(req) if err != nil { return "", "", errors.WithStack(err) } defer resp.Body.Close() body, err := ioutil.ReadAll(resp.Body) if err != nil { return "", "", errors.WithStack(err) } // 解析出返回内容中的cookie cookie, err = parseCookie(string(body)) if err != nil { return "", "", errors.WithStack(err) } // 获取响应头中的cookie if len(resp.Cookies()) < 1 { return "", "", errors.New("response cookie error") } cookie2 = fmt.Sprintf("%s=%s", resp.Cookies()[0].Name, resp.Cookies()[0].Value) return cookie2 + ";" + cookie, cookie2, nil } /** 返回格式为: */ // parseCookie 解析出cookie部分并执行js进行拼接 func parseCookie(script string) (string, error) { re := regexp.MustCompile(`document\.cookie=([^"]*);location`) matches := re.FindStringSubmatch(script) if len(matches) < 2 { return "", errors.New("first cookie parse error") } vm := otto.New() // 返回格式需要执行js拼接 cookieStr, err := vm.Run(matches[1]) if err != nil { return "", errors.WithStack(err) } return cookieStr.String(), nil } // getRealCookie 解密出真正的cookie func getRealCookie(method, baseUrl, cookie string) (string, error) { // 创建请求 // 这里会验证user-agent,必须与获取cookie保持一致 req, err := http.NewRequest(method, baseUrl, nil) req.Header.Add("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7") req.Header.Add("Accept-Language", "zh-CN,zh;q=0.9,en;q=0.8") req.Header.Add("User-Agent", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36") req.Header.Add("Cookie", cookie) // 发送请求 res, err := http.DefaultClient.Do(req) if err != nil { return "", errors.WithStack(err) } defer res.Body.Close() body, err := ioutil.ReadAll(res.Body) if err != nil { return "", errors.WithStack(err) } // 从混淆代码中取出相关信息 cookieData, err := parseCookie2(string(body)) if err != nil { return "", errors.WithStack(err) } var data scriptData if err := json.Unmarshal([]byte(cookieData), &data); err != nil { return "", errors.WithStack(err) } // 从返回数据获取到对应的cookie cookieValue := decryptCookie(&data) if cookieValue == "" { return "", errors.New("cookie empty") } // 拼接出真正的cookie realCookie := fmt.Sprintf("%s=%s", data.Tn, cookieValue) return realCookie, nil } // decryptCookie 解密cookie,这部分代码是从js中一点一点分析出来的 func decryptCookie(data *scriptData) string { chars := data.Chars for i := 0; i < len(chars); i++ { for j := 0; j < len(chars); j++ { realCookie := data.Bts[0] + chars[i:i+1] + chars[j:j+1] + data.Bts[1] value := hash(data.Ha, realCookie) if value == data.Ct { return realCookie } } } return "" } type scriptData struct { Bts []string `json:"bts"` Chars string `json:"chars"` Ct string `json:"ct"` Ha string `json:"ha"` Is bool `json:"is"` Tn string `json:"tn"` Vt string `json:"vt"` Wt string `json:"wt"` } // parseCookie2 返回的数据是ob混淆,经过分析后提出有用的部分为: /** ; go({ "bts": ["1692867818.638|0|j2C", "SjkeBkkPhhJzCsfPy8YxCg%3D"], "chars": "nIqNnycLKKKdDxvfkwMHdO", "ct": "1756d5ed879c6b656cf7afb10b75a54690ab7bd17b21c84b6d2bded8f9524fe1", "ha": "sha256", "is": false, "tn": "__jsl_clearance_s", "vt": "3600", "wt": "1500" }) */ func parseCookie2(script string) (string, error) { re := regexp.MustCompile(`;go\((.*?)\)`) matches := re.FindStringSubmatch(script) if len(matches) < 2 { return "", errors.New("cookie2 error") } return matches[1], nil } // hash 解密用到的方法 func hash(typ string, value string) string { switch typ { case "md5": h := md5.Sum([]byte(value)) return hex.EncodeToString(h[:]) case "sha1": h := sha1.Sum([]byte(value)) return hex.EncodeToString(h[:]) case "sha256": h := sha256.Sum256([]byte(value)) return hex.EncodeToString(h[:]) } return "" }- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 请求网站,发现前两次请求都会返回521,第三次请求成功,说明前两次请求肯定是干了什么事情;使用接口请求工具模拟请求分析该过程
-
相关阅读:
JUC并发编程第三篇,CompletableFuture场景练习,电商比价需求性能提升
Weblogic各版本历史
Grads:绘制风流畅
将nestjs项目迁移到阿里云函数
PTA_乙级_1011
从MVC到DDD的架构演进
STM32与陀螺仪、加速度计传感器的数据融合与姿态估计
Shell(4)条件控制语句
【XSS跨站脚本】反射型xss(非持久型)
7.Scala类
- 原文地址:https://blog.csdn.net/qq_32890891/article/details/132990157
