-
genEcc256-test
// Get a random value to sign using the built in DRBG state
DRBG_Generate(NULL, digest.t.buffer, digest.t.size);
if(g_inFailureMode)
5322080903370CCDEA83B6FE92607D5A642506F792D4D4E8CAF8567F948A2D0E759125B2DE3AFF293CA5DD81D5D7374Cg_inFailureMode1 = 0
g_inFailureMode2 = 0
g_inFailureMode3 = 0
g_inFailureMode4 = 0
g_inFailureMode5 = 0
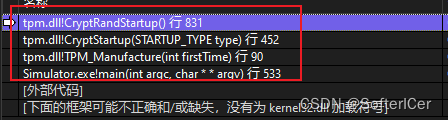
g_inFailureMode6 = 1LIB_EXPORT BOOL
CryptRandStartup(
void
)
{
#if ! _DRBG_STATE_SAVE
// If not saved in NV, re-instantiate on each startup
return DRBG_Instantiate(&drbgDefault, 0, NULL);
#else
// If the running state is saved in NV, NV has to be loaded before it can
// be updated
if(go.drbgState.magic == DRBG_MAGIC)
return DRBG_Reseed(&go.drbgState, NULL, NULL);
else
return DRBG_Instantiate(&go.drbgState, 0, NULL);
#endif
}
- /* 通过rand计算出ECC256 ECC384 SM2密钥对*/
- int
- main(
- int argc,
- char* argv[]
- )
- {
- int i; /* argc iterator */
- int irc;
- printf("C:begin genEcc256\n");
- UINT32 e = 0;
- TPMT_PUBLIC publicArea;
- TPMT_SENSITIVE sensitive;
- RAND_STATE rand;
- // 初始化全局的go.drbgState,在 CryptEccGenerateKey中的 DRBG_Generate 中用到
- CryptRandStartup();
- // 5322080903370CCDEA83B6FE92607D5A642506F792D4D4E8CAF8567F948A2D0E759125B2DE3AFF293CA5DD81D5D7374C
- unsigned char c[] = { 0x53, 0x22, 0x08, 0x09, 0x03, 0x37, 0x0C, 0xCD, 0xEA, 0x83, 0xB6, 0xFE, 0x92, 0x60, 0x7D, 0x5A, 0x64, 0x25, 0x06, 0xF7, 0x92, 0xD4, 0xD4, 0xE8, 0xCA, 0xF8, 0x56, 0x7F, 0x94, 0x8A, 0x2D, 0x0E, 0x75, 0x91, 0x25, 0xB2, 0xDE, 0x3A, 0xFF, 0x29, 0x3C, 0xA5, 0xDD, 0x81, 0xD5, 0xD7, 0x37, 0x4C };
- memset(rand.drbg.seed.bytes, 0, 48);
- memcpy(rand.drbg.seed.bytes, c, 48);
- char name9[] = "after copy rand.seed";
- myprintf2(name9, rand.drbg.seed.bytes, 48);
- rand.drbg.magic = DRBG_MAGIC;
- rand.drbg.reseedCounter = 0x0000000000000064;
- publicArea.type = 0x0023;
- publicArea.nameAlg = 0x000b;
- publicArea.objectAttributes = 0x00040060;
- publicArea.authPolicy.t.size = 0;
- //#define TPM_ECC_NIST_P256 (TPM_ECC_CURVE)(0x0003)
- //#define TPM_ECC_NIST_P384 (TPM_ECC_CURVE)(0x0004)
- //#define TPM_ECC_SM2_P256 (TPM_ECC_CURVE)(0x0020)
- // 根据这个来决定使用哪个曲线对应的n
- publicArea.parameters.eccDetail.curveID = 0x20;
- publicArea.parameters.eccDetail.symmetric.algorithm = 0x0010;
- publicArea.parameters.eccDetail.symmetric.keyBits.aes = 0;
- publicArea.parameters.eccDetail.symmetric.keyBits.camellia = 0;
- publicArea.parameters.eccDetail.symmetric.keyBits.sym = 0;
- publicArea.parameters.eccDetail.symmetric.keyBits.xor = 0;
- publicArea.parameters.eccDetail.symmetric.mode.aes = 0;
- publicArea.parameters.eccDetail.symmetric.mode.camellia = 0;
- publicArea.parameters.eccDetail.symmetric.mode.sym = 0;
- publicArea.parameters.eccDetail.scheme.scheme = 0x0018;
- publicArea.parameters.eccDetail.scheme.details.ecdh.hashAlg = 0x000b;
- publicArea.parameters.eccDetail.scheme.details.ecdaa.hashAlg = 0x000b;
- publicArea.parameters.eccDetail.scheme.details.ecdaa.count = 0;
- sensitive.sensitiveType = 0x0023;
- sensitive.authValue.t.size = 0x0020;
- sensitive.seedValue.t.size = 0;
- sensitive.sensitive.ecc.t.size = 0;
- TPM_RC ret = CryptEccGenerateKey(
- &publicArea,
- &sensitive,
- &rand
- );
- printf("C:CryptEccGenerateKey = %d \n", ret);
- return ret;
- }
-
相关阅读:
一文2500字手把手教你使用jmeter进行分布式压力测试【保姆级教程】
剑指Offer || 044.在每个树行中找最大值
CG-FX 风向传感器 聚碳 浅谈工作原理
WebSocket实现聊天功能
信息差也能赚钱?具体是怎么做的?看完这个你就懂了!
Python按类别和比例从Labelme数据集中划分出训练数据集和测试数据集
UE4 使用材质后期 制作玻璃有雨效果
32/100 二叉树的层序遍历 33/100 二叉树的最大深度 34/100 平衡二叉树
PG数据库表及表注释查询语句
解决微信小程序报错:“SyntaxError:Unexpected end of JSON input”
- 原文地址:https://blog.csdn.net/liudong200618/article/details/132877632
