-
服务器被矿工入侵记录
前两天,日常巡查发现某台甲骨文服务器CPU异常,如下
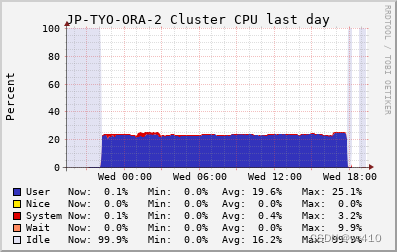

遂登录服务器检查,果然发现有名为kthreaddk的高CPU进程,然后一系列手工处置完毕。
倒查入侵过程:
1、检查ssh登录日志,监控提示挖矿时间在22:05附近,过滤auth.log发现确为ssh认证登录,属于密码爆破事件
Aug 9 13:06:11 ora-jp-vm-2 sshd[3121717]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=177.37.160.16 user=root
Aug 9 13:06:13 ora-jp-vm-2 sshd[3121717]: Failed password for root from 177.37.160.16 port 32884 ssh2
Aug 9 13:06:14 ora-jp-vm-2 sshd[3121717]: Connection closed by authenticating user root 177.37.160.16 port 32884 [preauth]
Aug 9 13:06:15 ora-jp-vm-2 sshd[3121719]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=177.37.160.16 user=root…………………………………………………………………………
Aug 9 14:03:29 ora-jp-vm-2 sshd[3123227]: Accepted password for root from 177.37.160.16 port 29432 ssh2
Aug 9 14:03:29 ora-jp-vm-2 sshd[3123227]: pam_unix(sshd:session): session opened for user root by (uid=0)
Aug 9 14:03:29 ora-jp-vm-2 systemd-logind[668]: New session 12071 of user root.
Aug 9 14:03:29 ora-jp-vm-2 systemd: pam_unix(systemd-user:session): session opened for user root by (uid=0)
Aug 9 14:03:44 ora-jp-vm-2 sshd[3123227]: pam_unix(sshd:session): session closed for user root
Aug 9 14:03:44 ora-jp-vm-2 systemd-logind[668]: Session 12071 logged out. Waiting for processes to exit.2、异常进程由两部分组成,一个是分布式爆破程序,另一个是挖矿程序
a.启动器释放爆破程序至 /var/tmp/ 目录下运行并创建目录/etc/calendar/*******
root@ora-jp-vm-2:~# lsof -p 3124482
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
12ac4b39f 3124482 root cwd DIR 8,1 0 1043365 /etc/calendar/1zp583 (deleted)
12ac4b39f 3124482 root rtd DIR 8,1 4096 2 /
12ac4b39f 3124482 root txt REG 8,1 3509800 45205 /var/tmp/12ac4b39f08 (deleted)
12ac4b39f 3124482 root 0r CHR 1,3 0t0 6 /dev/null
12ac4b39f 3124482 root 1w CHR 1,3 0t0 6 /dev/null
12ac4b39f 3124482 root 2w CHR 1,3 0t0 6 /dev/null
12ac4b39f 3124482 root 3u IPv6 262950353 0t0 TCP *:50847 (LISTEN)
12ac4b39f 3124482 root 4u a_inode 0,14 0 11450 [eventpoll]
12ac4b39f 3124482 root 5u raw 0t0 262950356 BF00000A:0006->00000000:0000 st=07
12ac4b39f 3124482 root 9u IPv4 264436563 0t0 TCP ora-jp-vm-2...oraclevcn.com:53438->199.192.29.89:ssh (ESTABLISHED)
12ac4b39f 3124482 root 12u IPv4 264092883 0t0 TCP ora-jp-vm-2...oraclevcn.com:55224->47.100.116.35:ssh (ESTABLISHED)
12ac4b39f 3124482 root 13u IPv4 264442314 0t0 TCP ora-jp-vm-2...oraclevcn.com:40772->ns3140029.ip-94-23-38.eu:ssh (ESTABLISHED)
12ac4b39f 3124482 root 18u IPv4 264633167 0t0 TCP ora-jp-vm-2...oraclevcn.com:38822->185-25-241-251.rdns.posilan.com:ssh (ESTABLISHED)
12ac4b39f 3124482 root 28u IPv4 264279094 0t0 TCP ora-jp-vm-2...oraclevcn.com:44344->47.242.6.229:ssh (ESTABLISHED)
12ac4b39f 3124482 root 30u IPv4 264092495 0t0 TCP ora-jp-vm-2...oraclevcn.com:39112->120.48.174.154:ssh (ESTABLISHED)
12ac4b39f 3124482 root 31u IPv4 264281143 0t0 TCP ora-jp-vm-2...oraclevcn.com:34514->server1.nordvpn.com:ssh (ESTABLISHED)
12ac4b39f 3124482 root 32u IPv4 264113575 0t0 TCP ora-jp-vm-2...oraclevcn.com:39862->70.182.181.94:ssh (ESTABLISHED)
12ac4b39f 3124482 root 37u IPv4 263133938 0t0 TCP ora-jp-vm-2...oraclevcn.com:51280->nbl37.ntup.net:http (ESTABLISHED)b.释放矿工至/etc/calendar/*******/kthreaddk并开始挖矿,完成后均自我删除
root@ora-jp-vm-2:~# lsof -p 3148134
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
kthreaddk 3148134 root cwd DIR 8,1 4096 2 /
kthreaddk 3148134 root rtd DIR 8,1 4096 2 /
kthreaddk 3148134 root txt REG 8,1 5781824 1043366 /etc/calendar/1zp583/kthreaddk (deleted)
kthreaddk 3148134 root DEL REG 0,15 264994119 /anon_hugepage
kthreaddk 3148134 root DEL REG 0,15 264991570 /anon_hugepage
kthreaddk 3148134 root DEL REG 0,15 264991569 /anon_hugepage
kthreaddk 3148134 root 0r CHR 1,3 0t0 6 /dev/null
kthreaddk 3148134 root 1w CHR 1,3 0t0 6 /dev/null
kthreaddk 3148134 root 2w CHR 1,3 0t0 6 /dev/null
kthreaddk 3148134 root 3r CHR 1,9 0t0 11 /dev/urandom
kthreaddk 3148134 root 4u a_inode 0,14 0 11450 [eventpoll]
kthreaddk 3148134 root 5r FIFO 0,13 0t0 264991565 pipe
kthreaddk 3148134 root 6w FIFO 0,13 0t0 264991565 pipe
kthreaddk 3148134 root 7r FIFO 0,13 0t0 264994106 pipe
kthreaddk 3148134 root 8w FIFO 0,13 0t0 264994106 pipe
kthreaddk 3148134 root 9u a_inode 0,14 0 11450 [eventfd]
kthreaddk 3148134 root 10u a_inode 0,14 0 11450 [eventfd]
kthreaddk 3148134 root 11u a_inode 0,14 0 11450 [eventfd]
kthreaddk 3148134 root 12r CHR 1,3 0t0 6 /dev/null
kthreaddk 3148134 root 13u IPv4 264991567 0t0 TCP ora-jp-vm-2...oraclevcn.com:56140->nbl37.ntup.net:5443 (ESTABLISHED)c.处置过程中,上述进程会反复重新运行,查crontab,发现有写入自启动命令
释放了一个可执行程序(启动器)在/dev/cpu/中每分钟执行检查
root@ora-jp-vm-2:~# crontab -l
* * * * * /dev/cpu/idtxdm-rwxr-xr-x 1 root root 3509800 Aug 10 09:45 idtxdm
root@ora-jp-vm-2:/dev/cpu# file idtxdm
idtxdm: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, no section header
最后看了下,nbl37.ntup.net的80端口应该是用来报告肉鸡信息的,5443是其矿池的代理接口,整体来说比较简单的入侵过程,清理也不太费劲。
-
相关阅读:
微信小程序获取当前的位置
简单电子琴设计verilog蜂鸣器8音阶,视频/代码
GFS分布式文件系统
1.renren框架windows下搭建
C基础-数组
2023年贵州省职业院校技能大赛(高职组)“软件测试”赛项竞赛规程
详解 Flink 的容错机制
【Linux安全之iptables的target】
程序员面试必备软技能,值得收藏!
go语言实现心跳机制样例
- 原文地址:https://blog.csdn.net/wr410/article/details/126279865