-
Android Qcom USB Driver学习(十一)
该系列文章总目录链接与各部分简介: Android Qcom USB Driver学习(零)
基于TI的Firmware Update固件升级的流程分析usb appliction layers的数据USB Protocol Package
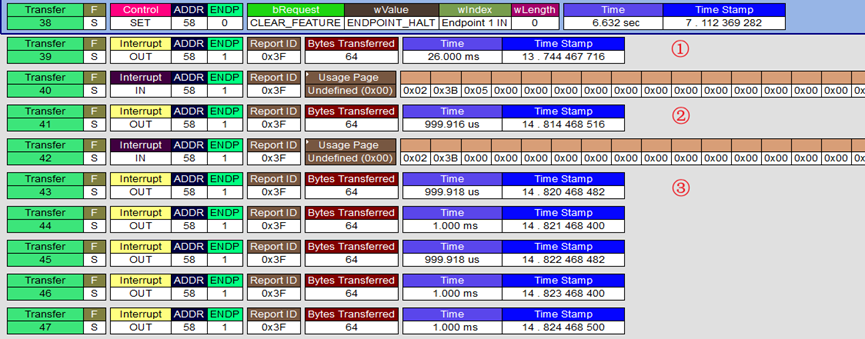



①/② map to check password correct
Package Format: Byte[0] = Report Id Byte[1] = Valid Length (0x21 = 33) Byte[2] = BSL Core Commands(0x11 RX Password) Byte[3] = Valid Data (0xFF) ... Byte[Byte[1]+1] = Valid Data (0x00) Byte[Byte[1]+2] = 0xAC ... Byte[63] = 0xAC (Full Length = 64) Interrupt Out: Host Transfer(Client Receive) (Interrupt IN): Client Transfer(Host Receive) 3F2111FF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FF0000AC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC 3F2111FF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFAC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC ACACACAC- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
③ map to download bsl program(bootloader)
TI provide the bsl program named RAM_BSL_xxx.txt,拆包后每48个字节进行组包发送

Package Format: Byte[0] = Report Id Byte[1] = Valid Length(0x34 = 52) Byte[2] = BSL Core Commands(0x1B RX Data Block Fast) Byte[3] = RAM_ADDRESS(0x00) Byte[4] = RAM_ADDRESS(0x25) Byte[5] = RAM_ADDRESS(0x00) Byte[6] = Valid Data (0x00) ... Byte[Byte[1]+1] = Valid Data(0x85) Byte[Byte[1]+2] = 0xAC ... Byte[63] = 0xAC 3F341B00 25000008 0839B240 805A5C01 32C23140 9033B013 982CFF3F 12010002 00000008 47200002 09010000 00010600 FF0901A1 0185ACAC ACACACAC ACACACAC 下一组写入数据的RAM地址为0x002500 + 48 = 0x002530(30 2500) 3F341B30 25003F95 3F750825 01150109 01810285 3F953F75 08250115 01090191 02C00902 29000101 00803209 04000002 03000000 0921ACAC ACACACAC ACACACAC- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
④ map to load PC(usb reconnect)
⑤ map to send the BSL Version
⑥ map to write the firmware to flash
这里的firmware是指由固件编译后生成的.txt文件,数据格式如上,同样以48个字节拆分进行传输
3F341B00 80002A14 C80C4A48 5A0E3F40 AEA10F5A 5E4F0200 3A502224 1B4A0600 0B930420 8A430000 0C437D3C 5E0A3E50 88235D4E 0600ACAC ACACACAC ACACACAC- 1
- 2
- 3
- 4
⑦ map to Software BOR Reset
⑧ map to load PC(usb reconnect)
详情见User’s Guide MSP430™ Flash Devices Bootloader (BSL)
BSL Mode - Firmware Update
这里的流程图只是大概流程,具体流程还得用usb分析仪进行抓包分析,如上章所示的几个步骤可实现固件升级

下面就不用看拉,写着完的,本想向直接再hal层写数据下去的,但每framework方便。
Demo C for process password
#include#include #include #include #include #include void printf_pkg(uint8_t* data){ for(int i = 0; i < 4; i++){ for(int j = 0; j < 16; j++){ printf("%02X",*(data + (i*16+j))); if(j == 3 || j == 7 || j == 11) printf(" "); } printf("\n"); } printf("\n"); } //int转16进制 int DectoHex(int dec, unsigned char *hex, int length) { for(int i=length-1; i>=0; i--) { hex[i] = (dec%256)&0xFF; dec /= 256; } return 0; } //1.读取文件中所有内容 //2.去除空字符和回车字符(头@2500 尾'q') //3.组包(每两位数据转为int再转为16进制存储) int main(){ FILE* fd; int len = 0; int count = 0; int pkg_cnt = 0; int ram_address = 0; int hex_data = 0; uint8_t rdata[6]; uint8_t ** pkg; uint8_t * data; fd = fopen("RAM_BSL_00.08.08.39.txt", "r+"); if(fd == NULL) printf("failed to open\n"); fseek(fd, 0, SEEK_END); len = ftell(fd); printf("the password file length = %d\n", len); fseek(fd, 0, SEEK_SET); fread(rdata, 1, 1, fd); fread(rdata, 5, 1, fd); rdata[5] = '\0'; ram_address = atoi(rdata); sscanf(rdata, "%x", &ram_address); printf("ram_address start = %X\n", ram_address); len = len - 6; data = (uint8_t *)malloc(sizeof(uint8_t)*len); uint8_t * head = data; while(*rdata != 'q'){ fread(rdata, 1, 1, fd); if(* rdata != ' ' && * rdata != '\n' && *rdata != 'q'){ *data = *rdata; data ++; } } *data = '\0'; data = head; fclose(fd); printf("%s\n", data); len = strlen(data); if(len % 48 == 0) pkg_cnt = len / (48 * 2); else pkg_cnt = len / (48 * 2) + 1; printf("the password file len = %d pkg count = %d the reset = %d\n", len, pkg_cnt, len % 48); pkg = (uint8_t **)malloc(sizeof(uint8_t*)* pkg_cnt); for(int i = 0; i < pkg_cnt; i++){ *(pkg+i) = (uint8_t*)malloc(sizeof(uint8_t)*64); memset(*(pkg+i), 0xAC, 64); } int rest = 0; for(int i = 0; i < pkg_cnt; i++){ *(*(pkg+i)+0) = 0x3F; *(*(pkg+i)+1) = 0x34; *(*(pkg+i)+2) = 0x1B; *(*(pkg+i)+3) = ram_address & 0xFF; *(*(pkg+i)+4) = (ram_address >> 8) & 0xFF; *(*(pkg+i)+5) = (ram_address >> 16) & 0xFF; if(i != pkg_cnt-1) rest = 48; else rest = (len % 48)/2; for(int j = 0; j < rest; j++){ rdata[0] = data[count++]; rdata[1] = data[count++]; rdata[2] = '\0'; sscanf(rdata, "%x", &hex_data); *(*(pkg + i) + 6 + j) = (uint8_t)hex_data; } ram_address += 48; } for(int i = 0; i < pkg_cnt; i++){ printf_pkg(*(pkg+i)); } return 0; } - 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
Demo Java for process password
Android Framwork基础之FileInputStream文件数据流处理
Android Framework 通过bulkTransfer(mUsbEndpoint_out, bytes, bytes.length, 1000)调用libusbhost.so(system/core/libusbhost)对节点
/dev/bus/usb/002/001进程操作 -
相关阅读:
【SpringMVC】RESTFul风格设计和实战 第三期
如何在 Ubuntu 上安装 EMQX MQTT 服务器
如何使用pywinauto打开Windows上指定的应用程序
基于YOLOv8/YOLOv7/YOLOv6/YOLOv5的条形码二维码检测系统(深度学习+UI界面+训练数据集+Python代码)
Web 部署
电子协会 C语言 1级 33 、奇偶数判断
TiDB-从0到1-数据导出导入
selinux权限添加总结
出差学小白知识No6:LD_PRELOAD变量路径不对找不到库文件
时间任务管理软件OmniFocus 3 mac中文版软件特色
- 原文地址:https://blog.csdn.net/qq_40405527/article/details/130843332
